Security and Compliance Dashboard
Overview
The Security and Compliance Dashboard in the Zoho Mail Admin Console provides an overview of all the recommended security configurations. It displays the overall security and compliance score along with the completion status for each action.
Dashboard Actions
You can do the following actions from the Security and Compliance Dashboard:
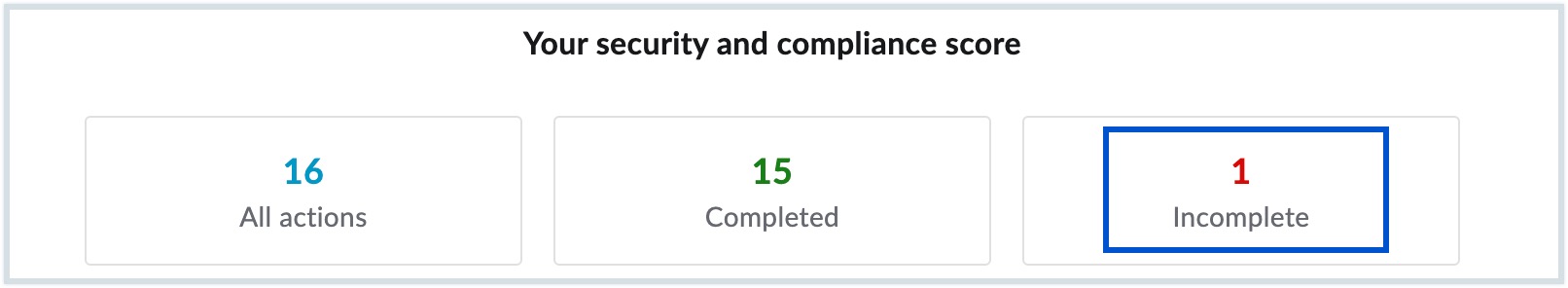
- Filter security parameters based on configuration status - You can click either All actions, Completed or Incomplete to view a list of security configurations based on the status you select. For example, you can quickly view the list of pending security configurations by clicking Incomplete.
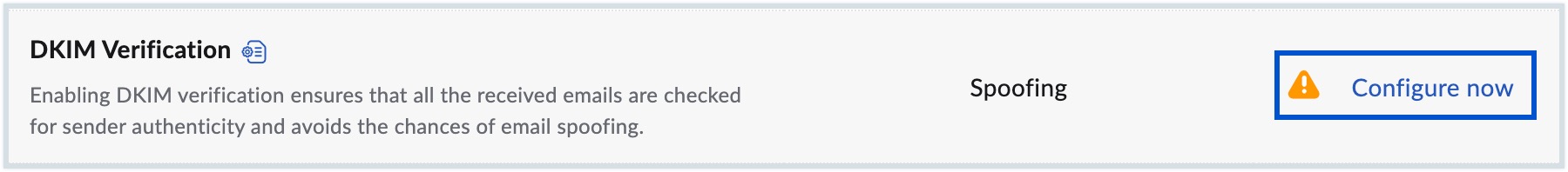
Configure a security parameter - Hover over a security parameter which is not yet configured and click the Configure now button. You will be redirected to the corresponding page in Admin Console where you can configure the desired settings.
Note:
The Configure now button will be visible only when you hover over a security parameter which is not yet configured.
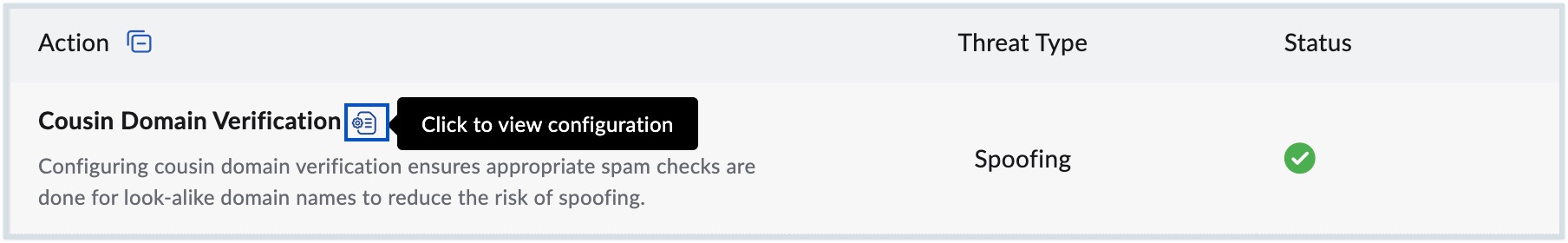
- View configuration - Click the tooltip icon next to a security parameter to navigate to its corresponding settings in the Admin Console. From there, you can review the current configuration or make necessary modifications.
Security Threats
The security threats that we protect you from include:
- Spoofing - An email is considered to be spoofed when spammers forge an email address of an organization/ person.
- Malware - Malware is any file or program that is intentionally designed to harm your computer/ network/ server.
- Account Breach - An account breach is a security violation that exposes any confidential or sensitive information to an outsider.
- Data Exfiltration - Data exfiltration is an unauthorised removal or movement of data from a device.
- Data Leak - Data leak is the accidental exposure of sensitive data onto the internet.
Security and Compliance Score
The security and compliance score assesses your progress in completing the recommended actions to improve your organization's security. The highest score indicates that your organization is highly secure against all types of spoofing, account breaches and any data leaks, while the lowest score suggests that your organization is vulnerable to a security breach.
Your organization's security score is classified under four categories:
- Low - When you add and verify your domain in Admin Console, the DMARC Verification, DNSBL Verification, No Trusted Senders and No presence of own domain in Trusted Domains get configured automatically and the security score status will be Low.
- Moderate - The next step after verifying your domain, is to configure email security/authentication protocols for all your mail-hosted domains. If you configure these settings when you are in a low score range, the score moves to the Moderate level.
- Good - Configuring the spam control settings and account related parameters will help you reach a Good security score range.
- Excellent - After you complete configuring all the parameters given in the Security & Compliance Dashboard, the score reaches the Excellent zone.
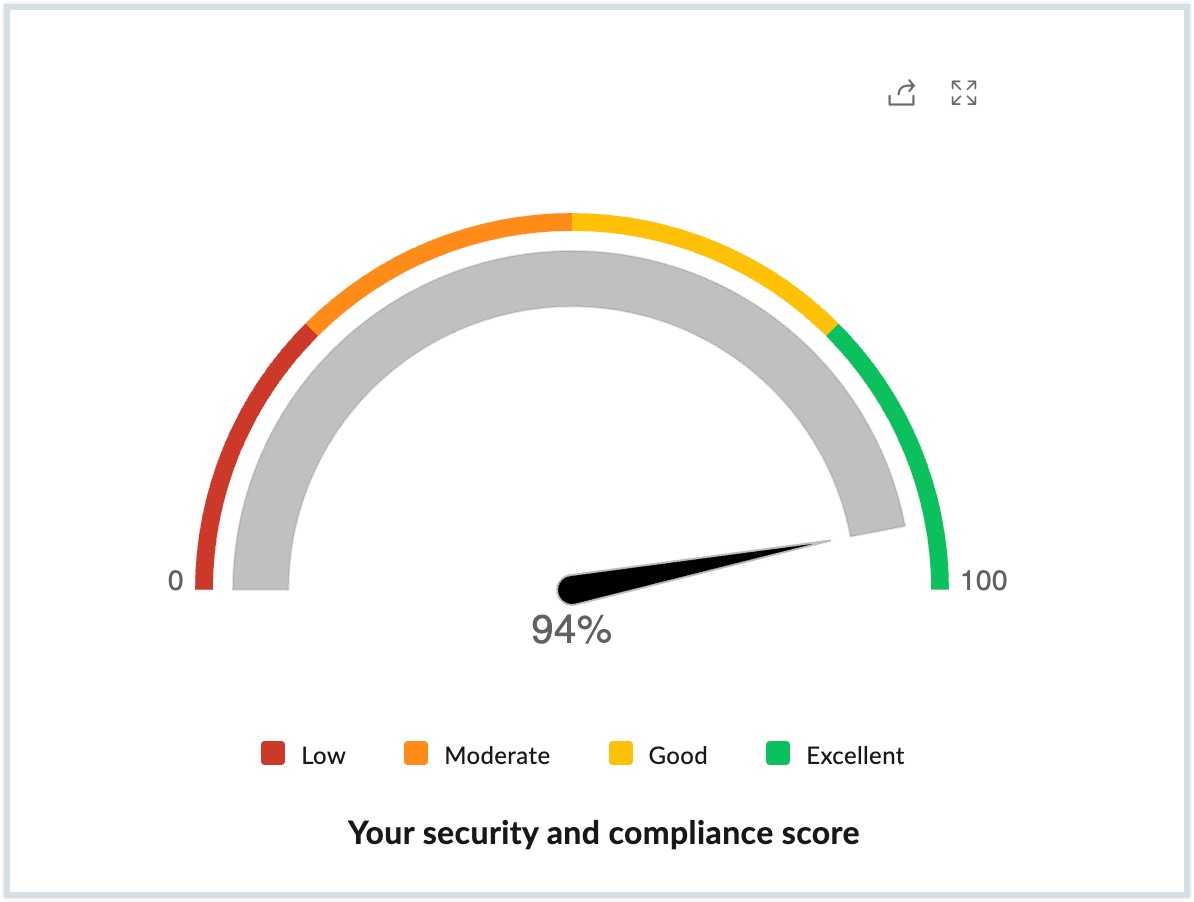
There is no particular order that you need to follow while setting up these parameters. Configure each security parameter as per your organization's requirements and ensure the security and compliance score is Excellent.
Recommended Security Settings
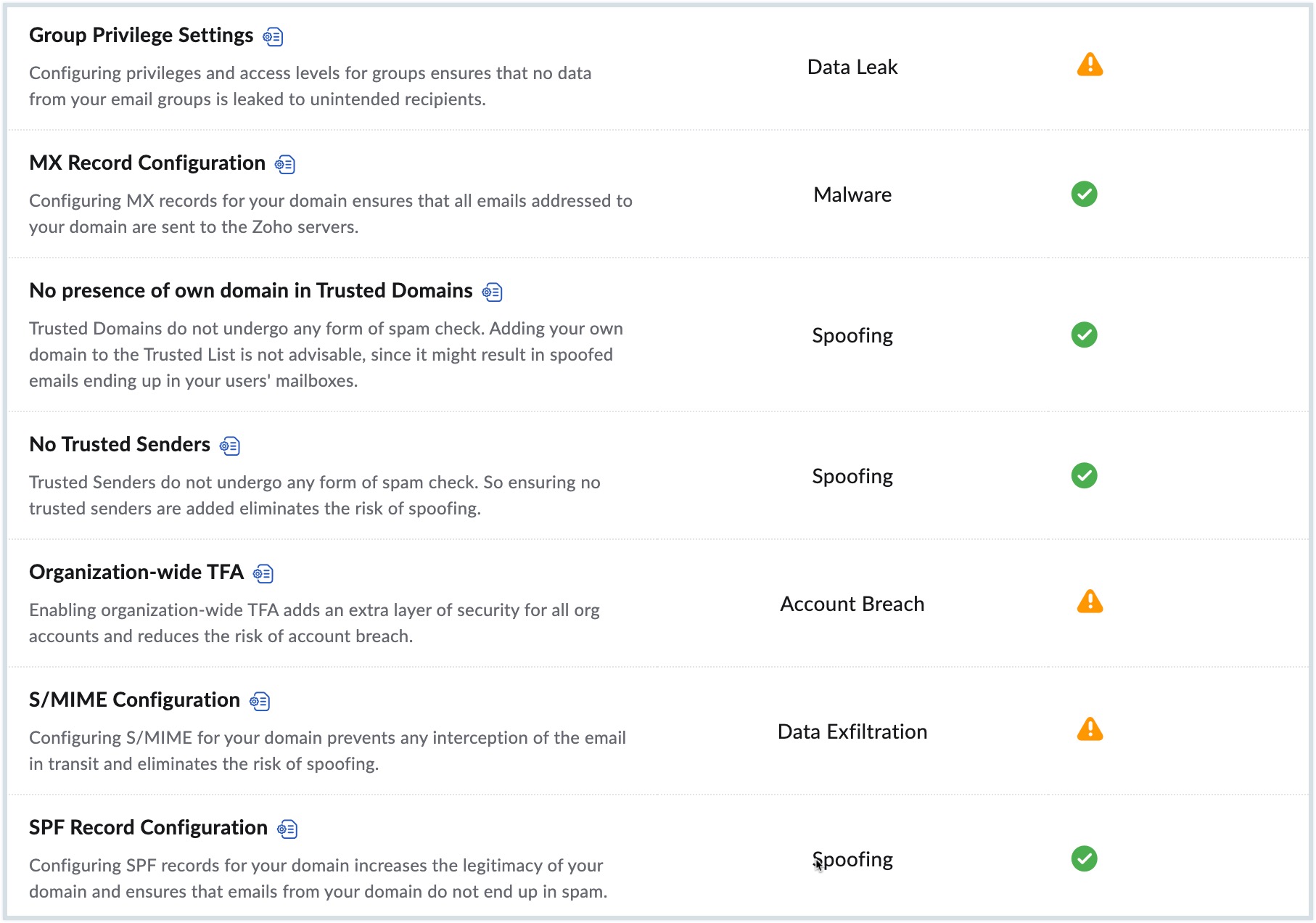
Zoho Mail provides various security settings and each parameter protects a particular threat type. Refer to the table given below to learn more about the settings available in Admin Console:
| Threat Type | Security Parameters | Description |
| Spoofing | DMARC Verification | DMARC is an email authentication protocol, which builds on the widely deployed SPF and DKIM protocols. In case of authentication failure, the DMARC policy is set to quarantine. Refer to DMARC Verification for the steps to configure your preferred setting. |
| DNSBL Verification | DNSBL is a consolidated blocked list based on user spam marking, abuse patterns, and certain third-party blocklists. Emails are detected as spam if the sending domain/ email address or IP address is present on the blocked list. Refer to DNSBL Verification for the steps to configure your preferred setting. | |
| No Trusted Senders | Emails from email addresses that are added to the Trusted Emails List get delivered to the mailbox without any spam check. These emails will not be validated for SPF/ DKIM/ blocklist checks. Please be doubly cautious before you add any email address to this list, as it may expose the organization to spam/ phishing attacks using this email address. Refer to No Trusted Senders in order to add or remove email addresses from the Trusted List. | |
| No presence of own domain in Trusted Domains | Emails from domains that are added to the Trusted Domains List get delivered to the mailbox without any spam check. These emails will not be validated for SPF/ DKIM/ blocklist checks. Please be doubly cautious before you add any domain to this list, as it may expose the organization to spam/ phishing attacks using this domain. Refer to No Trusted Domains to ensure that there are no own domains in the Trusted Domain list. | |
| SPF Record Configuration | SPF is an authentication mechanism that helps in identifying the IP addresses permitted to send emails using the domain name. Refer to SPF Record Configuration for the steps to configure the SPF records. | |
| DKIM Configuration | DKIM is an email validation system that uses encryption to validate if an email has been sent from authorized servers configured by the administrator of the domain. Refer to DKIM Configuration for the steps to configure DKIM. | |
| DMARC Policy | DMARC is an email authentication protocol. It builds on the widely deployed SPF and DKIM protocols. Additionally, it includes a reporting function that allows senders and receivers to monitor and protect their domain from fraudulent emails. Refer to DMARC Policy for the steps to configure your organization's DMARC policy. | |
| DKIM Verification | DKIM is an email authentication method that uses encryption to validate if an email is generated from systems authorized by the domain administrator. Emails are detected as spam in case of DKIM Failure. Refer to DKIM Verification for the steps to configure your preferred setting. | |
| SPF Verification | Sender Policy Framework, commonly known as SPF, is a text record associated with the domain to identify the servers permitted to send emails using the particular domain name. Emails are detected as spam in the case of SPF Failure and SPF Soft Failure. Refer to SPF Verification for the steps to configure your preferred setting. | |
| Cousin Domain Verification | Cousin domains or look-alike domains are spoofed domains with names similar to valid domains. If you expect a domain to send genuine emails, but want to mark an email from any other variations of the domain name as spam, you can add it in this section. Refer to Cousin Domain Verification for the steps to configure cousin domains. | |
| Display Name Verification | You can set up a display name and associate one or more email addresses with this display name. The emails that arrive with other display names, other than the ones added here will be considered fraudulent or spoofed emails. Refer to Display Name Fraud for the steps to configure display name fraud. | |
| Internationalized Spam Settings | You can allow or reject emails based on the language used in the email. If you allow certain languages, emails sent in those languages will be allowed and all the other emails will be moved to spam. Similarly, if you block certain languages, emails sent in those languages will be moved to spam and other emails will be allowed. Refer to Internationalized Spam for the steps to configure your preferred language settings. | |
| Malware | MX Record Configuration | MX records are special DNS Server records that designate recipient email servers for your domain. Configuring MX records for your domain ensures that all emails addressed to your domain are sent to the Zoho servers. Refer to Configure Email Delivery for the steps to configure MX records. |
| Account Breach | Suspicious Login Alerts | Suspicious Login Alerts, if enabled send an email alerting users of any unusual logins into their email accounts. Refer to Suspicious Login Alerts for the steps to configure suspicious alerts. |
| Organization-wide TFA | Two-factor authentication is an additional security process to secure organization accounts with the combination of a password and a mobile device. You can choose to enable or disable TFA for your organization. Refer to Two-factor Authentication for the steps to configure TFA for your organization. | |
| Data Exfiltration | S/MIME Configuration | Secure/Multipurpose Internet Mail Extensions (S/MIME) provide high-level security to your organization's emails. This encrypts the content of the email using keys, and curbs any misuse. It ensures that only authorized personnel can access your data. Refer to S/MIME Configuration for the steps to configure S/MIME. |
| Data Leak | Group Privilege Settings | You can choose who can have access to create organization and personal groups under group privileges settings. By default, the super admin will have all the privileges in the organization. Refer to Group Privilege Settings for the steps to configure group privileges. |
Note:
- It is equally important that your organization's users remain cautious irrespective of a high security and compliance score. Users must also adhere to standard email security protocols to prevent data loss or account breaches.
- This security feature will be available only for organizations that are using one of our paid plans.




