Why is data protection critical in contract management?
In today’s business landscape, government regulations such as GDPR and CCPA have a big impact on data management, putting the emphasis on protecting personally identifiable information (PII) at an all-time high. Noncompliance has severe consequences, including heavy fines and imprisonment.
Since contracts contain critical information about you and your counterparties, data protection plays a key role in contract management. Safeguarding contract data is not just a legal necessity, but a crucial step to earning customer and supplier trust, strengthening brand reputation, mitigating business risks, and meeting current business standards. This is why you need to ensure your company invests in comprehensive CLM systems with data protection features that improve compliance and prevent data loss or breach.
Data protection in Zoho Contracts
At Zoho, the safety of our customer data is of utmost importance. To achieve data security, we’ve built robust internal mechanisms. Some of these mechanisms are incorporated as features in Zoho Contracts so you can effectively protect your counterparty data and comply with data protection regulations. In Zoho Contracts, the PII information and contract data remain encrypted at rest. With our Data Protection Settings, you can mark the fields containing personal data and efficiently manage the following requests from your data subjects and counterparties:
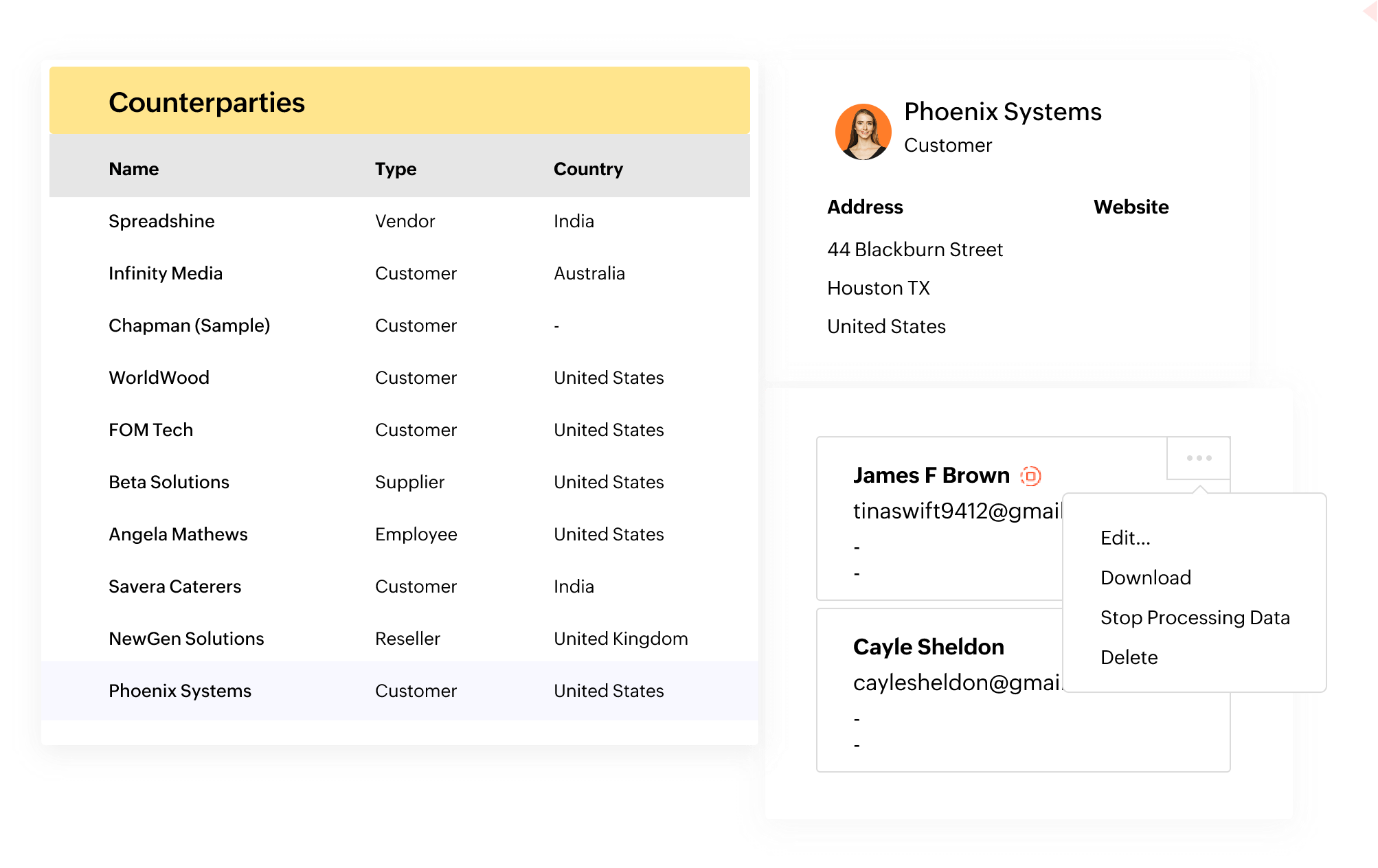
Stop processing data
At any point in time, your data subjects or counterparties have the right to restrict the processing of their data. With the help of our Data Protection Settings in Zoho Contracts, you can easily handle these requests. When the Data Protection Settings is enabled, you can stop processing a particular counterparty contact’s data with a single click. You can resume processing the data at any time.
When you stop processing data for a contact:
- They will be removed from the Negotiators and Signers lists for contracts they are part of.
- They will not have access to any contract pending negotiation review or signature.
- They will not receive any further communication from Zoho Contracts.
Anonymize personal data
In most contracts, there is a time-bound term requiring you to delete and anonymize the PII of counterparties from your CLM system upon contract termination. Counterparties can also request to remove contacts and anonymize their identity if the contacts are no longer associated with them. Complying with these contractual terms and requests becomes complicated without a CLM designed to protect data.
In Zoho Contracts, the option to anonymize a contact will appear as a checkbox when you delete a contact.
When you delete and anonymize a contact:
- They will be displayed as “Anonymized User” in Zoho Contracts, and assigned a number based on the order in which they were anonymized.
- They will be removed from the Negotiators and Signers lists for contracts they are part of.
- They will not have access to any contracts pending negotiation review or signature.

Restrict access for non-admins
Zoho Contracts includes an export option for users to download counterparty contact details. While often necessary, download and export options create data vulnerabilities. With this in mind, Contracts empowers you to restrict access to these features. When only admins can export or download counterparty contact details from your CLM, there’s reduced potential for breaches.
Enhanced security for user access
Zoho Contracts ensures a secure sign-in process for users with multi-factor authentication (MFA). Ensuring that all your users enable MFA can help your organization prevent data hacks that could cost millions. Zoho offers four modes of MFA that allow quick and secure sign-in. In addition to the authentication layers, different user profiles and roles allow for granular access control.
Improved compliance and accurate audits
Zoho Contracts stores all activities performed by users in a central audit system that is easily accessible to admins. The admin audit logs ensure that all admins are aware of the changes made to organization-wide settings. Activity tracking is available on multiple levels, and stores events in chronological order. At the same time, the download logs keep track of all downloads made from the CLM system. This improved visibility makes your CLM system easily auditable and drives accountability.








