Business Email Compromise (BEC)
What is Business Email Compromise?
Business Email Compromise (BEC) is an email scam similar to phishing, in which a hacker targets a user or business with the intention to divulge sensitive information. BEC, also known as Email Account Compromise (EAC) is a technique cybercriminals use to trick victims into paying huge sums of money to fraudulent bank accounts.
How do BEC attacks work?
In BEC, attackers disguise themselves as a trusted/legitimate sender, such as an executive of a company, a senior leader, etc. Due to oversight, the recipients assume that the email has come from a legitimate sender, and they fall prey to the attack.
Typically, hackers specialized in cybercrime activities, carry out a BEC attack in an organized manner. Below is an outline of the different stages of a BEC attack:
- Attacker identifies a target
- Send spear-phishing emails to the target
- Share instructions to complete a wire transfer
- Recipient becomes a victim and completes the wire transfer
BEC Methods
Once the attacker identifies a target, they achieve BEC using one of the methods that follow.
Compromised accounts
When a hacker gains access to a legitimate account, they can use the compromised email account and send messages to users in your organization. Emails received from a compromised account do not raise suspicion. In such cases of email account compromise (EAC), the recipient tends to act as per the instructions given in the email.
Domain spoofing
The attacker spoofs the email domain name and attempts to trick the recipient. In domain spoofing, cybercriminals forge the sender address of an email and send the message to a targeted user, and request to do a wire transfer. It can also be called display name spoofing, where the fraudster fakes the sender's display name to appear as if it originated from a senior leader of the organization.
Lookalike domain
In this case, the attacker sends an email from a domain that looks similar to a trusted domain. For example, the actual email address user@webhosting.com can be spoofed as user@vvebhosting.com. It is possible that a user skips to identify the cousin domain name in the email address field and oversees the letter "w" with "vv". If such an email requests an urgent fund transfer, the user tends to fall prey to the BEC attack.
Common types of BEC
Most BEC emails will have a sense of urgency and instruct the recipient to action immediately. Users tend to fall prey to such time-sensitive messages and become a victim of BEC. Following are the common BEC attacks that are prevalent across various industries.
Attorney impersonation
The type of BEC in which the attacker disguises as the official legal advisor of an organization and sends out emails to employees in an organization. It is quite uncommon for an employee to verify or validate the email that appears to originate from their organization's attorney.
CEO fraud
CEO fraud attempts are often directed to employees who are in the capacity to make financial transactions. Scammers send out an email that appears to be from the CEO or the highest executive of the organization and direct them to transfer funds to close a deal or to purchase gift cards, etc.
Data theft
The Human Resources (HR) team is the primary target for data theft where spammers intend to steal the confidential information of employees such as financial data, personal mobile number, etc. Once they gain access to the personal details, they look for various monetization options.
Employee impersonation
In this type of BEC fraud, the attacker disguises himself as a known employee within the organization and sends out emails to targeted users who are vulnerable to social engineering attacks. The recipient will not suspect the email's authenticity since it had originated from his colleague or manager.
Fake invoice scheme
Spammers act as an authorized vendors of your organization and send fake bills and invoices via email that appear similar to original bills. They request a finance team employee to transfer funds to a different bank account citing audit or compliance reasons that the recipient might not suspect.
Impact of BEC
In recent years, the Business Email Compromise has evolved as a major social engineering threat that can cause huge setbacks to a business. Some of the potential impacts a BEC could cause are mentioned below:
- Irrecoverable financial loss
- Incorrect vendor transactions
- Reputational downfall due to leak of personally identifiable information
- Intellectual property/data loss
Targets of BEC attack
Any employee in your organization could be a target of BEC. However, scammers target high-profile executives (such as the CEO), HR and finance team managers with decision-making privileges, and new joiners who generally do not suspect time-sensitive emails sent by senior team members.
How to identify BEC emails?
Although BEC emails look authentic, users can recognize the hidden threats when they read them carefully. Whenever you get an email, check if the email contains the following flags.
- Sense of urgency in the email subject or content - Keywords such as confidential, urgent, last day, etc. tend to make the users nervous and make mistakes. Do not respond to such emails.
- Wire transfer request from a trustworthy email account - If the email account of a known colleague gets compromised, spammers can send an email using the compromised account requesting a fund transfer.
- Executive of the company requests to purchase gift cards - The most common example of a BEC attack is an email from the CEO requesting an urgent wire transfer or purchase of gift vouchers.
- Emails requesting to share an employee's personal information - The vendor responsible for completing the background verification of your organization's employees, can request the HR team to share the details of a newly joined resource.
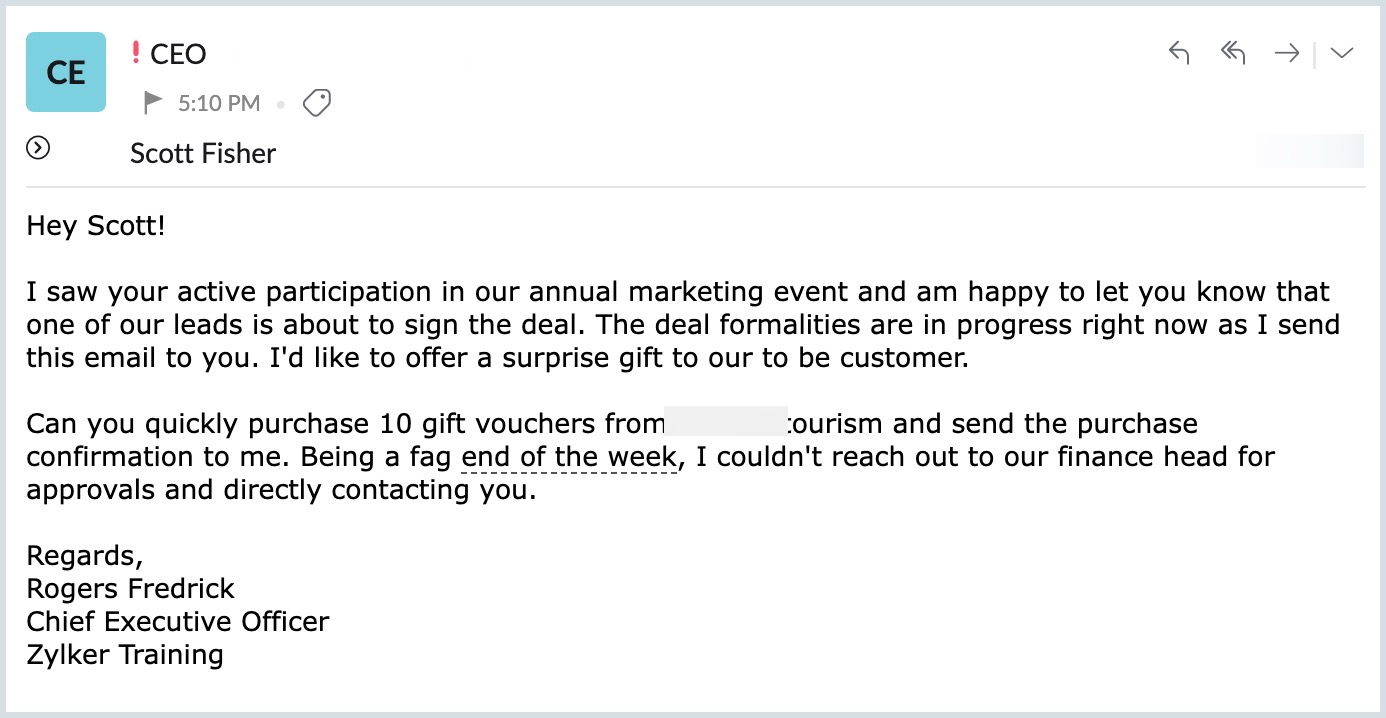
The image below depicts a CEO requesting the team member to purchase gift vouchers.
Best practices to protect against BEC attacks
The loss and damage caused by a BEC attack can be unimaginable. BEC scams cannot be entirely eliminated. However, it is recommended that you follow some of the widely deployed email best practices to fight against BEC attacks. A few of the best practices to protect your organization from BEC are:
- Conduct frequent cybersecurity and security awareness training sessions and encourage employees to attend them.
- Setup a robust email protection solution to fight against email threats.
- Configure the necessary rules, alerts, and email policies to protect against spam. You can configure a rule in such a way that the suspicious emails are quarantined and the admin can review the genuineness of the email and then deliver it to the recipient(s).
- Setup Multi-Factor Authentication (MFA) for all the user accounts.
- Review the audit logs in the email security application to constantly review the threats blocked and take appropriate actions.
- Do not respond to emails that have a sense of urgency. Look out for the words such as confidential, immediate action required, etc. If you receive an email, contact the sender to confirm the legitimacy of the email.
- Keep your device software up-to-date, such as the latest operating system, network patch updates, browser security updates, etc.