Phishing Emails
What is phishing?
Phishing is a type of cyber attack intended to steal a user's sensitive information like bank account details, passwords, and other personal information. The attackers lure their targets by masking their identity and pretending to be from a trusted source. Every user in an organization is responsible to act diligently in identifying phishing to prevent data breaches.
What is a phishing email?
Phishing email is an email sent by online fraudsters to steal a user's personal and financial information by tricking them. Since emails are predominantly used by every organization, scammers send out phishing emails tempting users to click on links or download attachments containing viruses, etc. Such emails which contain malicious links and malware prone files are called phishing email.
Cybercriminals also use telephone and messaging services (SMS, social media messages, etc.) as a tool to trap their targets.
Sample of a phishing email
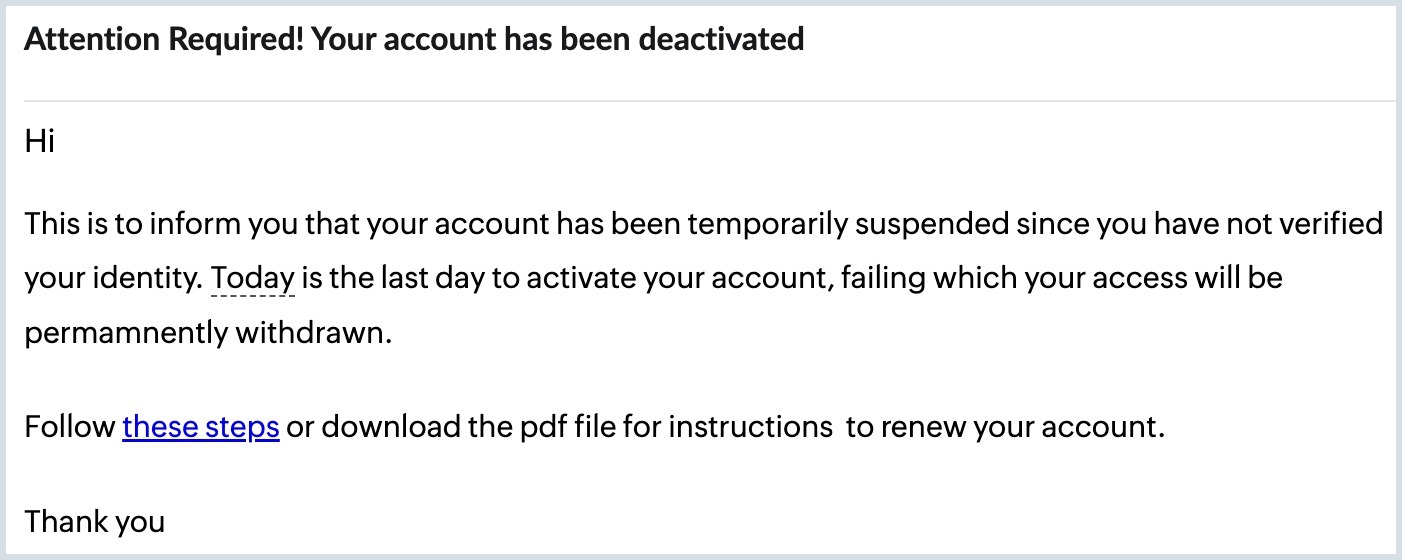
In the above example, the subject of the email has a sense of urgency, which increases the chances of a response. If the target user downloads the file or clicks the URL, it will result in a security compromise that will pose an immediate threat to the user's confidential information like passwords, bank account details, business email compromise (BEC), and more.
What are the different types of phishing?
Phishing attacks are classified based on the medium the phishing attempt is made by fraudsters. The different types of phishing are:
Email phishing
The standard and well-known phishing method is email phishing. Fraudsters send emails to bulk recipients with a sense of urgency requesting users to take immediate action. Email phishing attempts to manipulate the users and deceive them into sharing their personal information including login credentials, bank account details, etc.
Spear phishing
This is a targeted approach to phishing, unlike bulk or group phishing. The attacker gathers information about its target user through sources like social media and sends a personalized email that might include information like their full name, company's name, job title, or details of their job role. Collecting information about the target makes it easier to deceive them.
Whaling
Whaling refers to targeting 'big fish'—the senior officials in a company. It's difficult for the attackers to lure in senior executives, so the content drafted for whaling attacks is made to look like it's from government offices, courts, or customers. Policy violations and urgent money transfers to close a deal are some of the examples of Whaling.
Smishing and Vishing
In this case, the phishing attacks are carried out using a telephone. Smishing is nothing but sending a text message with a website URL and requesting the user to complete a mandatory user verification process. Voice phishing also known as Vishing, uses a voice call as a tool for deception. The attackers persuade a user on voice call making them believe that their request is legitimate. Users fall prey to vishing attacks if they follow the instructions given by the attacker.
Clone phishing
As the term indicates, clone phishing is an attempt to clone an existing legitimate email and replace the links/ attachments in that email. This attack has two levels of compromise. In the first step, the attacker hacks the contents of either the sender's or receiver's emails. In the second step, the attacker replaces the files in the legitimate email with malware and imitates the sender's identity.
Angler phishing
Social media has become a popular channel for interacting with companies and financial or government institutions. Phishing attacks on social media can be highly targeted as information about user interests is freely available. The attackers share fake tweets, reels, posts, or malicious URLs with their targets on social media, masquerading their true identity. This is called angler phishing.
These attacks can be avoided if social media users are cautious enough to identify and interact with verified company accounts only.
How to prevent phishing?
- Email security software - Businesses which use email for professional communication should ensure their email communication is secured using an email protection software. A strong anti-spam, phishing and malware setting can reduce the risk of data theft and account breaches.
- Email filters - The administrator of an organization can configure and monitor email filters, incoming and outgoing rules.
- Identify and avoid phishing communication - Phishing communication is done with a spoofed identity. Checking the sender's name, email address, and domain name before responding to any email can mitigate the risk of falling into the phishing trap.
- Sense of urgency - The contents of phishing communication generally have an urgent tone, ask for personal/confidential information, offer financial rewards, or have a set of instructions to download a file that is malware. Proceed with caution when you receive such emails.
- Create awareness among employees - In any organization, their security and privacy standards are only as strong as their weakest link. Since employees are susceptible to phishing attacks, they must be given all the information they will need in case there is an attempt to breach security and privacy.
- Phishing simulation - Use approved phishing simulator tools to send phishing emails to the users within your organization. Monitor how many users reported the email as phishing and otherwise. Take appropriate steps after the activity.
- Implement SPF, DKIM and DMARC - Configuring these protocols in DNS broadly serves two purposes—email authentication and encryption. Email authentication assures that the sender's identity is verified and an encrypted message indicates that the email's content has not been tampered with.
Learn more about SPF, DKIM, and DMARC.
Best practices to identify phishing emails
Although the emails appear to be from a trustworthy source, users can differentiate a phishing email from a legitimate one. The users in an organization are the first line of defence against email phishing. Educate your users on the best practices to recognize phishing emails. Listed below are some of the ways using which a phishing email can be identified:
- Pay attention to emails that have a sense of urgency. Reach out to the official customer care toll-free number of the company to ensure the email's credibility.
- Do not click hyperlinks inside an email if you are unsure of the sender.
- Do not download attachments since it can be a malware attempting to download a virus into your computer.
- Validate the sender information/ metadata. If you receive an unusual email from a known sender, cross-check with the sender about the legitimacy of the email.
- Look out for attractive statements in the email content.
- Identify grammatical and spelling errors.
- Hover over the link in an email and observe the actual redirection link.