Securing your email with eProtect
Keep spam away from your mailbox
eProtect's in-built spam filtering mechanisms keep spam emails at bay, catching even the emails that slip through the cracks in your email service. Additionally, you can fine-tune your organization's spam policies to ensure that users don't have to deal with annoying spam emails or fall for emails that nudge them to divulge sensitive information.
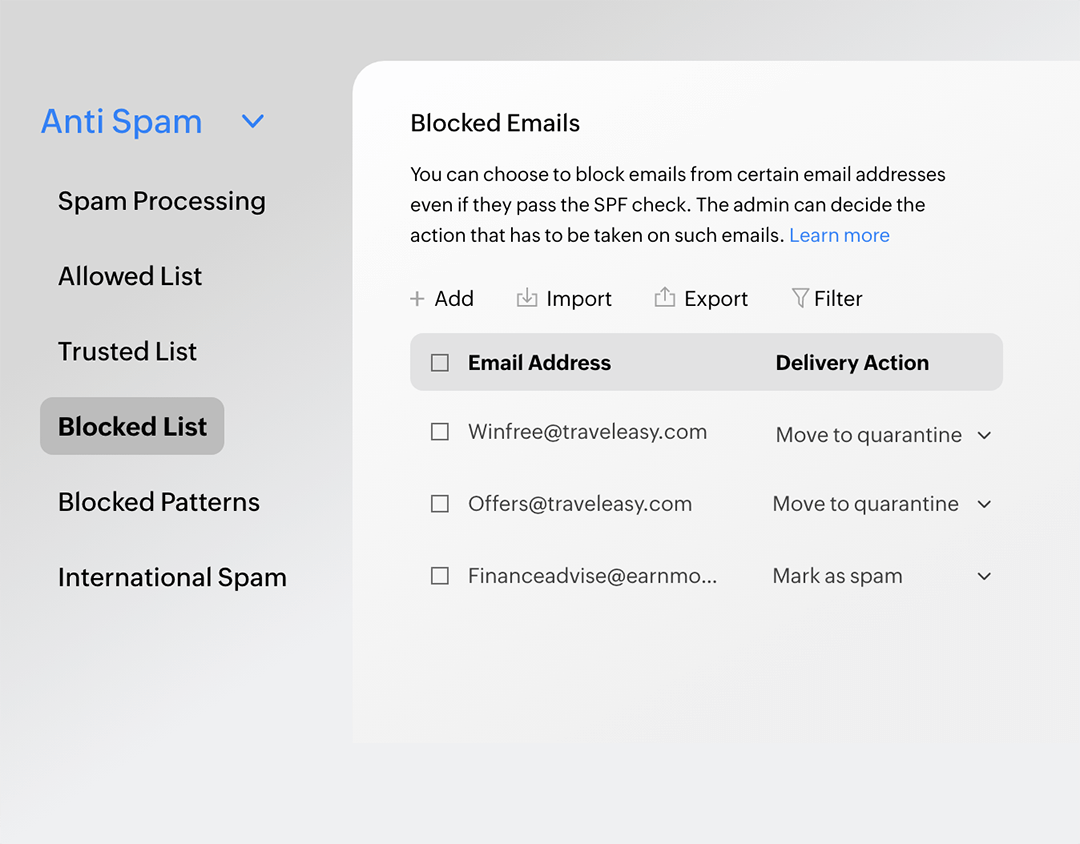
Allowed and blocked lists
Choose exactly which email address, domains or IP addresses to receive or block emails from. Enter separate lists for allowed and blocked lists to protect your users.
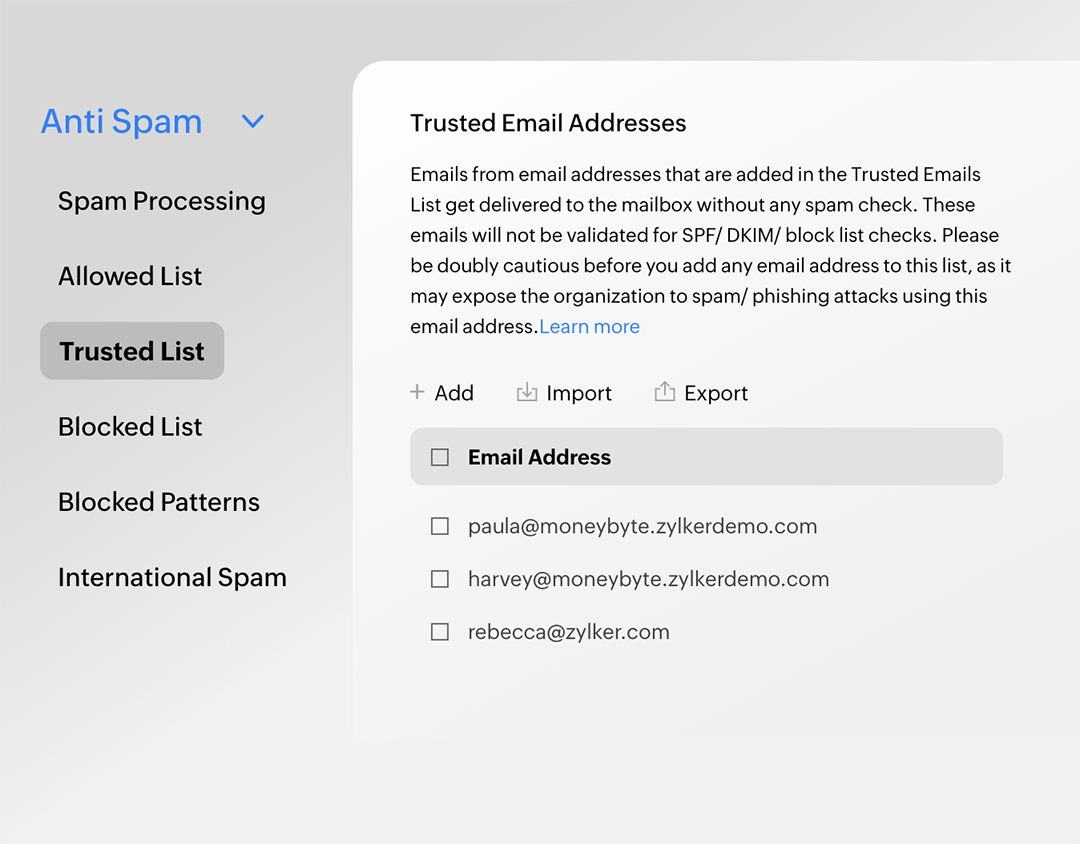
Safe sender lists
For emails, domains, and IPs that you absolutely trust, simply add them to your trusted lists and these emails will be delivered to your mailbox right away.
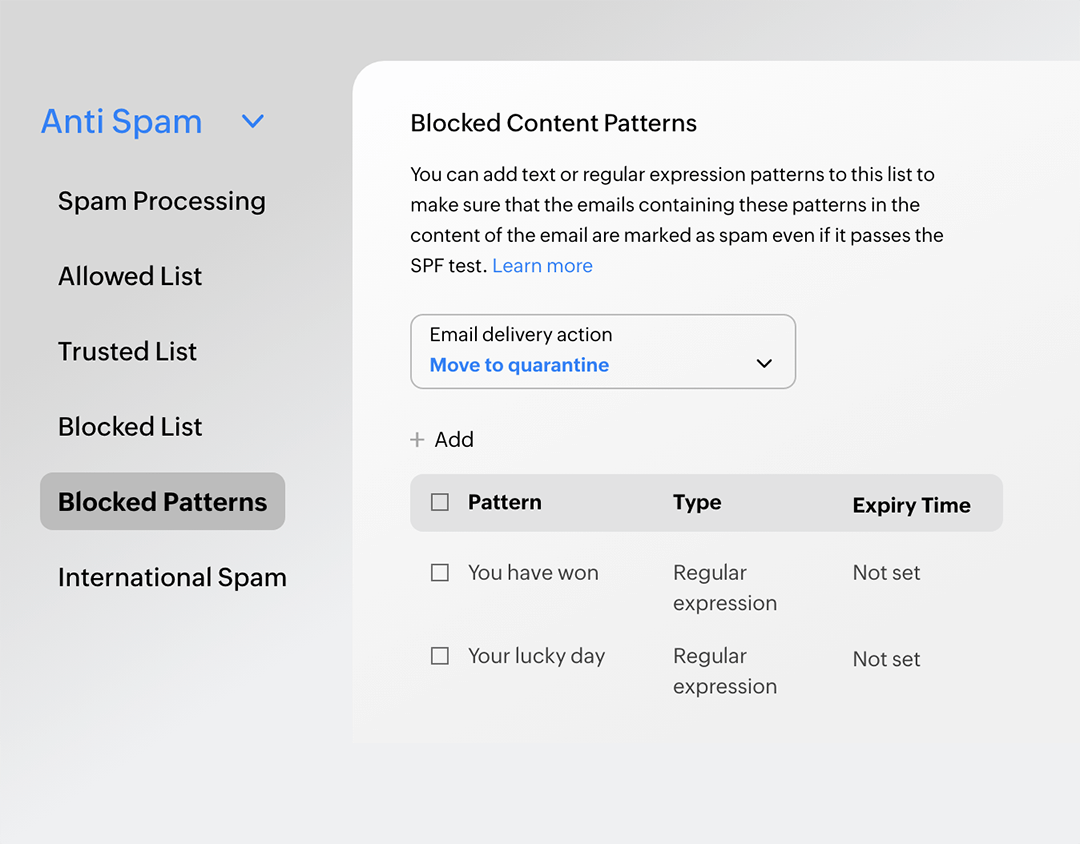
Pattern-based blocking
Enter text or regular expression patterns for recipient addresses, email subjects, or content and block suspicious emails from entering mailboxes.
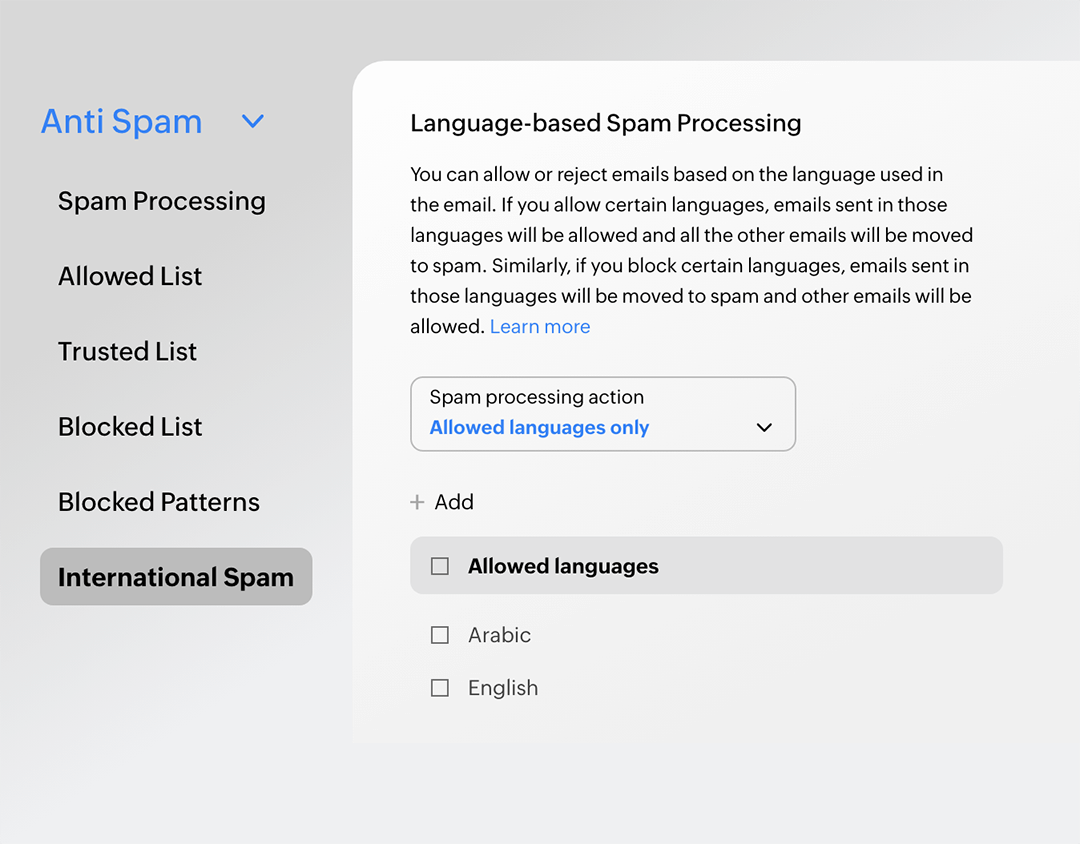
International spam protection
Spam emails know no borders! Protect your users from emails they might not fully comprehend by marking emails in specific languages or specific countries as spam.
Protect your organization from advanced threats
As email protection mechanisms grow stronger, cybercriminals continue to find new and innovative ways to get past these defenses. eProtect’s advanced threat detection mechanisms have been refined and perfected over the years to spot only the emails that shouldn’t be allowed entry into your users’ mailboxes, while ensuring zero false positives.
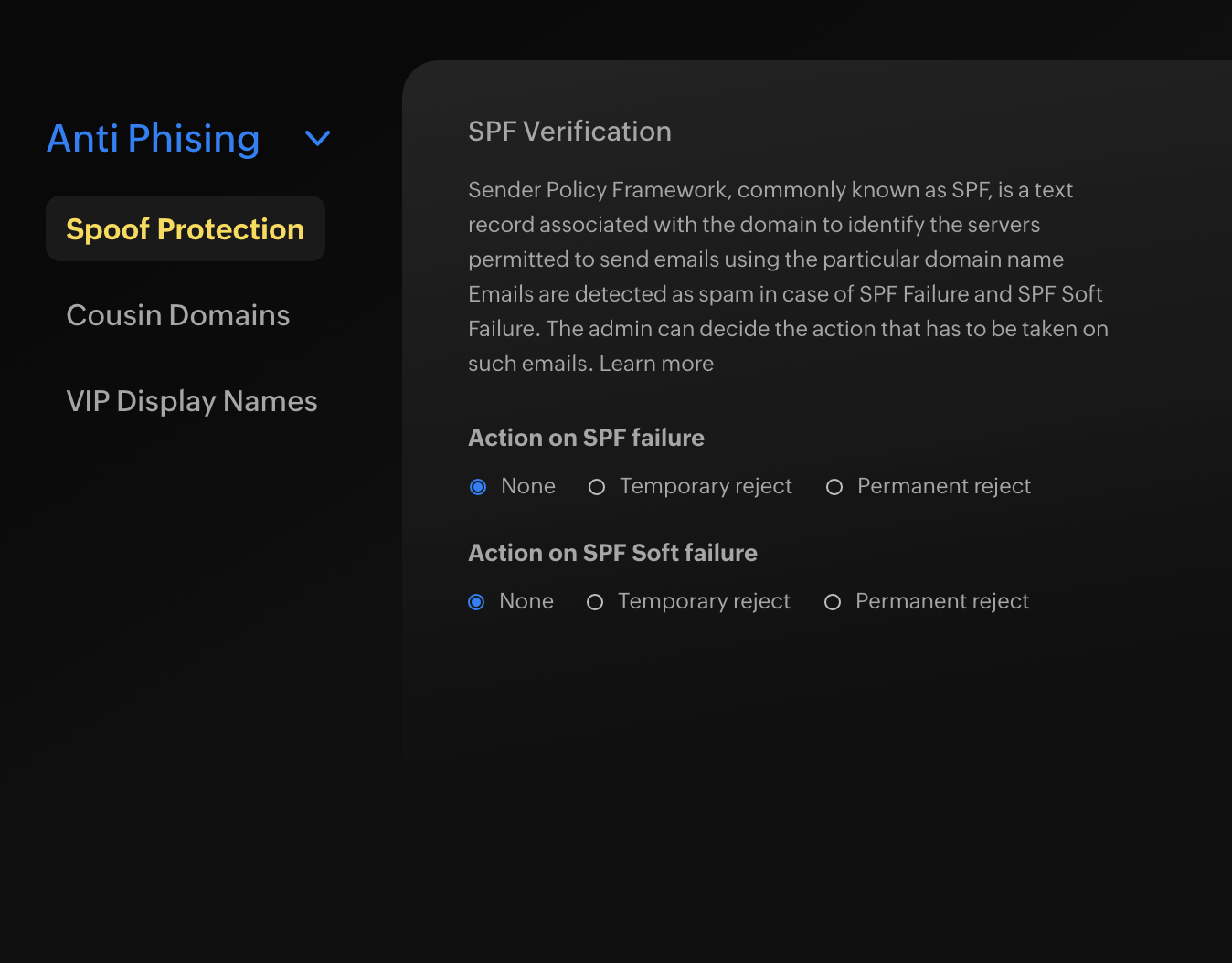
Spoof protection
Most spam emails pose from a different domain. Set up the action for emails that fail the SPF, DKIM, DMARC, or DNSBL authentication and deny unauthenticated emails from getting through to your mailbox.
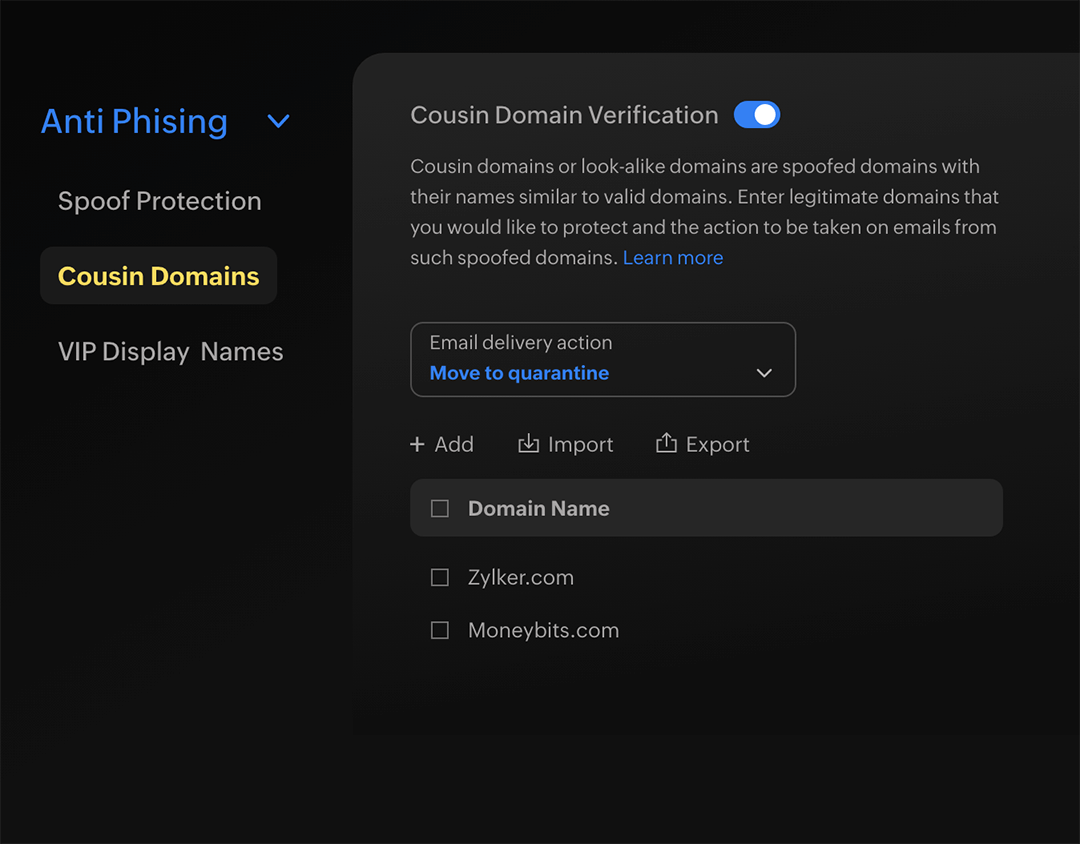
Brand protection
Scammers are constantly looking to exploit the trust users have in familiar brands. Configure quarantine for emails from any lookalikes of domain names your users trust.
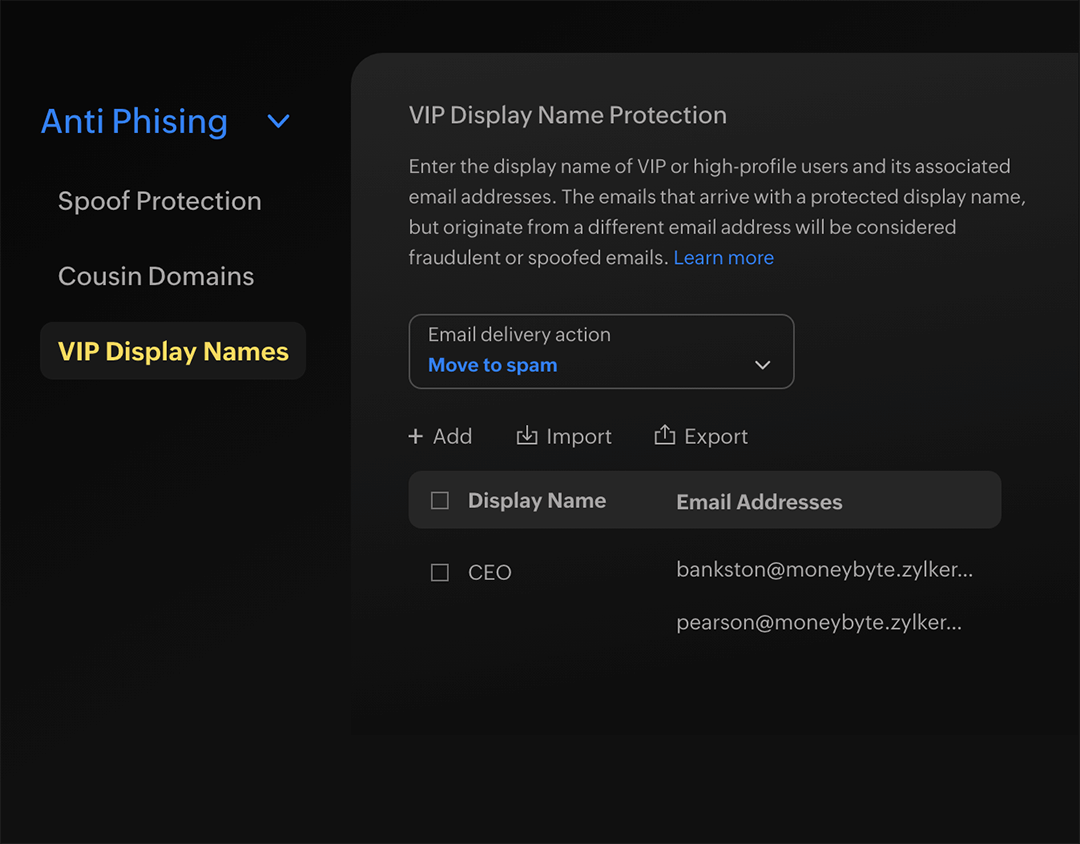
Executive impersonation protection
Secure your organization from fraudulent emails posing to be from high-profile employees by tagging relevant VIP display names with approved email addresses.
Safeguard users from malicious malware
Several types of malware—such as ransomware, viruses, and bots—have been on the rise over the past few years. eProtect detects emails that might contain such harmful files or links through URL protection and attachment analysis, making sure your users don't open them and lose their data to cybercriminals.
Stay ahead of breaches by impersonators
Scammers are using increasingly deceptive techniques to get their hands on confidential data. They cleverly create lookalike domain names of trusted brands to appear legitimate to the recipient. With eProtect's spoof protection features, you and your organization can stay protected from such attacks.
Protect your organization from phishing attacks
With more targeted attacks like spear phishing, attackers do diligent research on the organization they intend to attack and build their attack around a person or brand that users trust. eProtect's refined threat detection filters and advanced spoof detection mechanisms, spot fraudulent emails and prevent them from reaching your users.
Shield your users from zero-day attacks
Attacks that haven't previously been witnessed are called zero-day attacks. Attackers exploit vulnerabilities in the system that haven't been recognized, making users and systems unprepared to deal with such attacks. eProtect's advanced attachment and URL analysis capabilities, provide world-class protection against such new attacks.
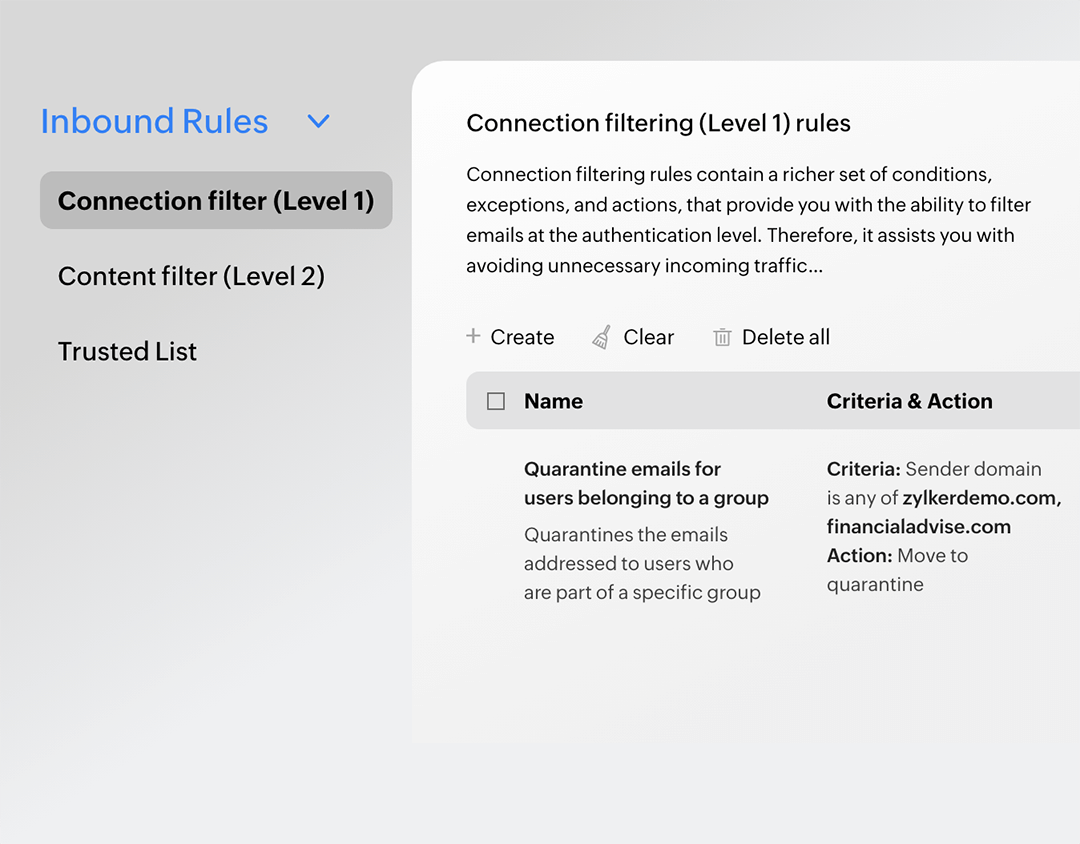
Secure your emails at the connection and content level
eProtect identifies malicious emails right when the connection is established between servers, based the sender IP address, authentication failures, and recipient data. Content analysis further scrutinizes emails for presence of keywords, certain tags, the email content, and URLs.
Inbound emails
Emails entering your organization can be checked for threats at the connection and content level and delivered to mailboxes with a warning or moved to the spam folder.
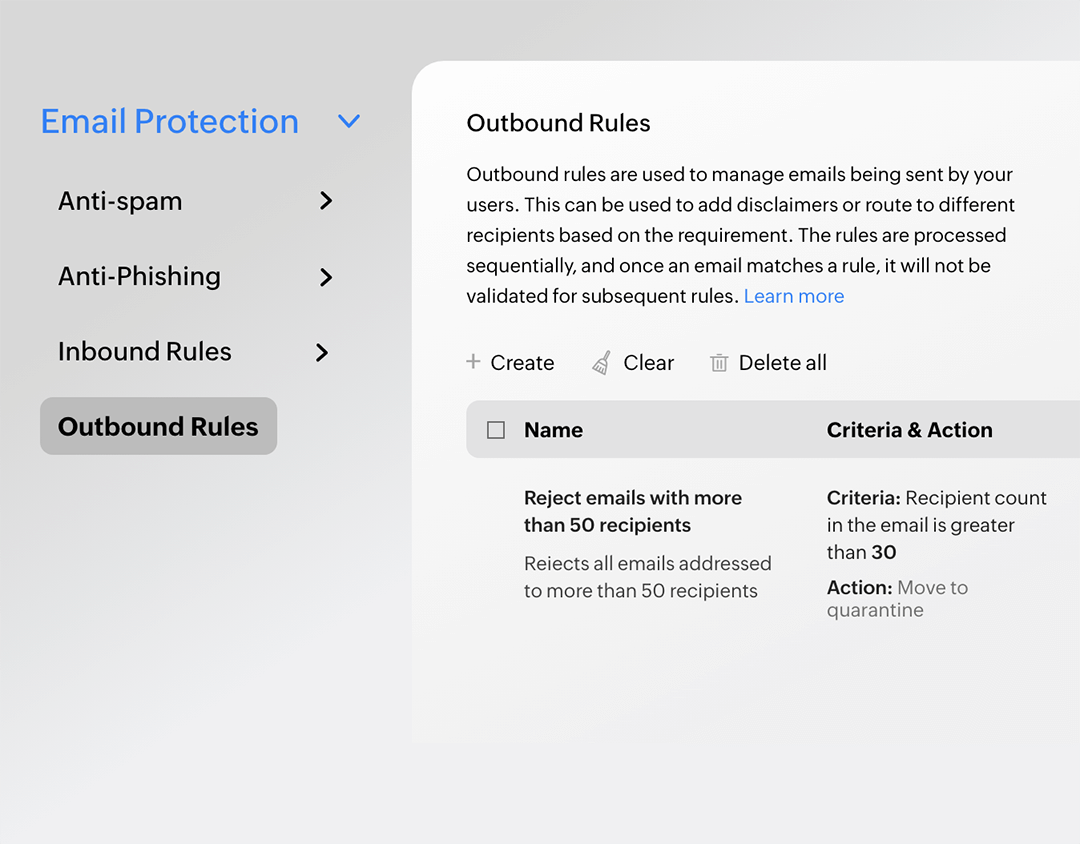
Outbound emails
Emails sent by your users from your organization's mailboxes can also be checked for any threats based on a set of conditions and the necessary action can be taken.
Choose your quarantine management strategy
With eProtect, you can stay worry free about your quarantine management. Give your trusted users access to manage their quarantined emails and for other users, the quarantine notification that's triggered at a frequency of your choosing notifies users of their quarantined emails and it makes your job that much easier!
Frequently Asked Questions
Why is email security important?
An organzation's most sensitive data is present in its emails. With the rising possibility of attackers gaining access to these emails, protecting them with an additional layer of security becomes important. Enhancing your email security ensures that emails with cyberattacks such as spam, phishing, spoofing and malware do not gain unauthenticated access.
What are the some of the best practices for robust email security?
Ensure that you have a robust cloud email security solution which is continuously updated to combat new kinds of threats. Migrate from legacy on-premise email security gateways and regularly review your email security policies and settings to provide top-notch security for your users. Additionally, conduct periodic security awareness trainings and inform users that they should exercise caution while opening emails, links and attachments from unknown senders.
How does a cloud email security gateway work?
A cloud email security gateway works to prevent email threats from reaching a user's mailbox and works in addition to the security provided by your email provider. The email security gateway stands as an intermediate layer between the email sending server and the receiving server while filtering any harmful content that your email provider's security systems could fail to detect.
How should I deal with a suspicious or spam email?
When you encounter a suspicious email, it's best to mark the email as spam and report the email to your organization's email administrator. Depending on the nature of the email, your administrator could consider configuring email security policies both in eProtect and your email provider.
What are the prevalent email security threats?
Email security threats can broadly be classified into five types, namely spam, phishing, spoofing, malware and zero-day attacks. Phishing can be further classified into spear phishing, business email compromise, credential harvesting, etc. Similarly, spoofing can be of varying types such as brand impersonation, VIP fraud, CEO impersonation, social engineering attacks and more. Malware could occur as ransomware, spyware, adware, viruses, etc.
eProtect's security capabilities provide protection from all of these attacks.
What is the difference between a cloud and on-premise email security provider?
In an on-premise email security provider, physical servers need to be set up and maintained in an on-premise location. With cloud email security providers, no server maintenance is required and the emails are scanned for threats through the cloud. This makes the cloud options less prone to third-party attacks, while ensuring better safety and stability.