- HOME
- All Topics
- Workplace Security
- The anatomy of a cyberattack: How employees can break the Cyber Kill Chain (A cybersecurity awareness month special)
The anatomy of a cyberattack: How employees can break the Cyber Kill Chain (A cybersecurity awareness month special)
- Published : November 4, 2024
- Last Updated : November 4, 2024
- 497 Views
- 4 Min Read
Attackers no longer target just systems—they target people.
In a digital-first workplace, the nature of cyber threats has evolved. Attackers no longer focus solely on systems and infrastructure. Instead, they target the human element—the employees, customers, and partners who interact with technology daily. By leveraging social engineering tactics like phishing, business email compromise (BEC), and spoofing, attackers manipulate people into granting unauthorized access, installing malware, or leaking sensitive data.
Employees are the frontline defenders of an organization’s cybersecurity, but they're also often its weakest link. Threat actors exploit employees’ trust, routines, and behaviors to bypass technical controls, making it imperative for organizations to understand the anatomy of these attacks and empower their workforce to recognize, respond to, and break the chain of cyber threats.
High-profile breaches in recent years
Incident | Year | Attack tactic | Description and impact |
2022 | MFA fatigue and social engineering | Attackers spammed an employee with MFA requests, impersonating Uber IT through WhatsApp to convince them to approve the access. This granted the hacker full access to Uber’s internal systems, compromising sensitive data, including customer information and source code. | |
2020 | Employee manipulation via social engineering | Attackers convinced employees to provide credentials, which gave them access to high-profile accounts. They used these accounts to launch cryptocurrency scams, causing reputational damage and highlighting weaknesses in insider access controls. | |
2021 | Credential theft and phishing | A stolen employee password allowed attackers to infiltrate the network, leading to a full-scale pipeline shutdown and ransom demand. This attack demonstrated the vulnerability of critical infrastructure to human error. | |
2020 | Phishing email and malware deployment | Attackers used a phishing email to gain initial access, deploying ransomware that disrupted operations and incurred financial losses, emphasizing the threat of targeted email attacks on large enterprises. |
Cybersecurity Awareness Month 2024
2024 marks 20 years of Cybersecurity Awareness Month (CSAM). Initiated in 2004 by the Cybersecurity & Infrastructure Security Agency (CISA) in partnership with the National Cyber Security Alliance (NCSA), CSAM has evolved significantly. It started as a campaign to promote basic cybersecurity practices and has transformed into a global movement that educates individuals, businesses, and governments on handling increasingly sophisticated cyber threats. The theme for 2024, “Secure Our World,” highlights this evolution.
Over the years, as cyber threats became more complex, the awareness initiatives expanded to include phishing detection, social engineering tactics, and more advanced defenses like multi-factor authentication (MFA). Today, it’s about proactive defense—understanding the full lifecycle of cyber threats and empowering every individual within an organization to play an active role in breaking attack chains.
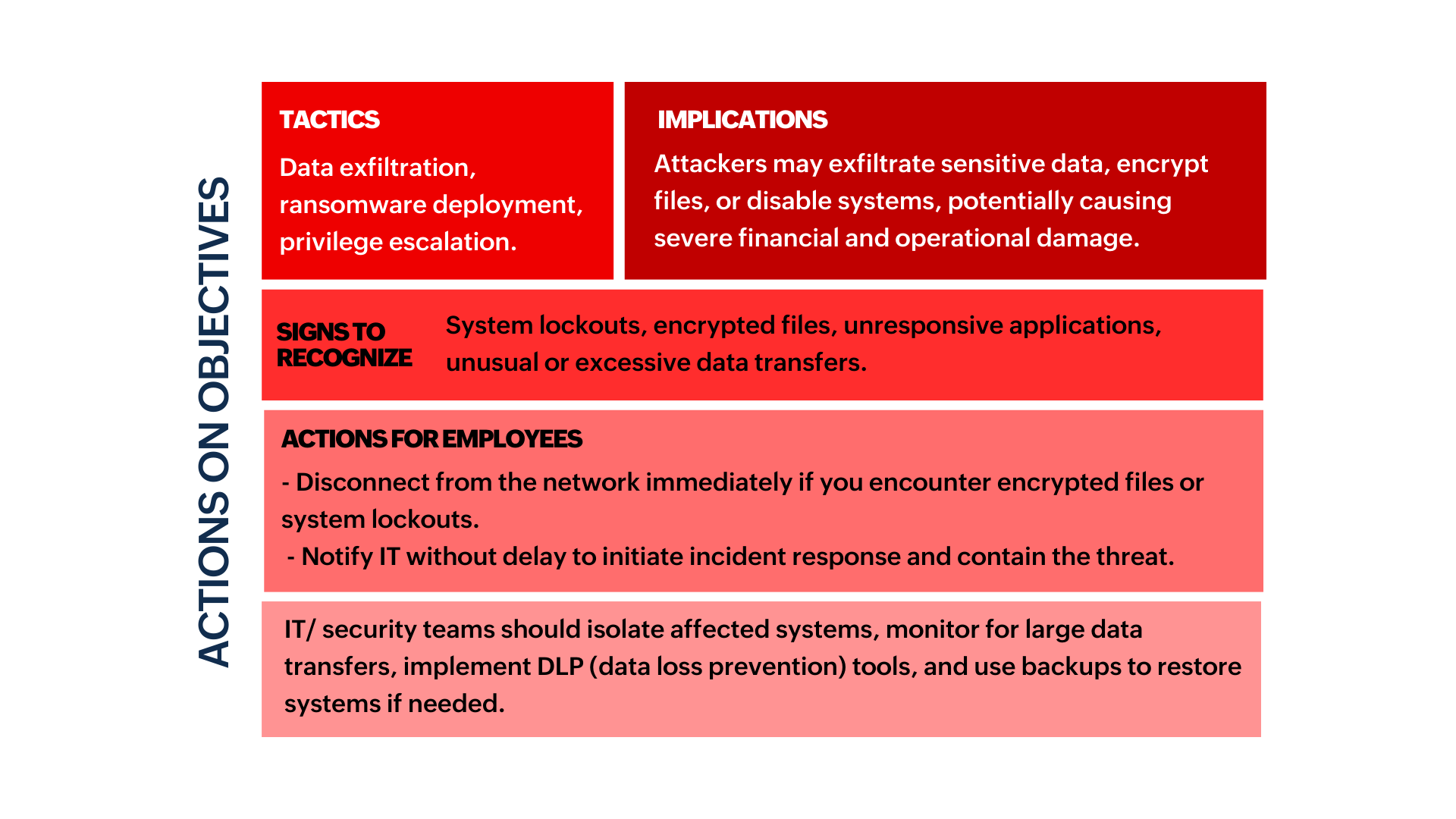
Cyber Kill Chain
Developed by Lockheed Martin, the Cyber Kill Chain is a framework designed to illustrate the stages of a cyberattack. By understanding this framework, employees can recognize how threats evolve and how to stop them at each stage.
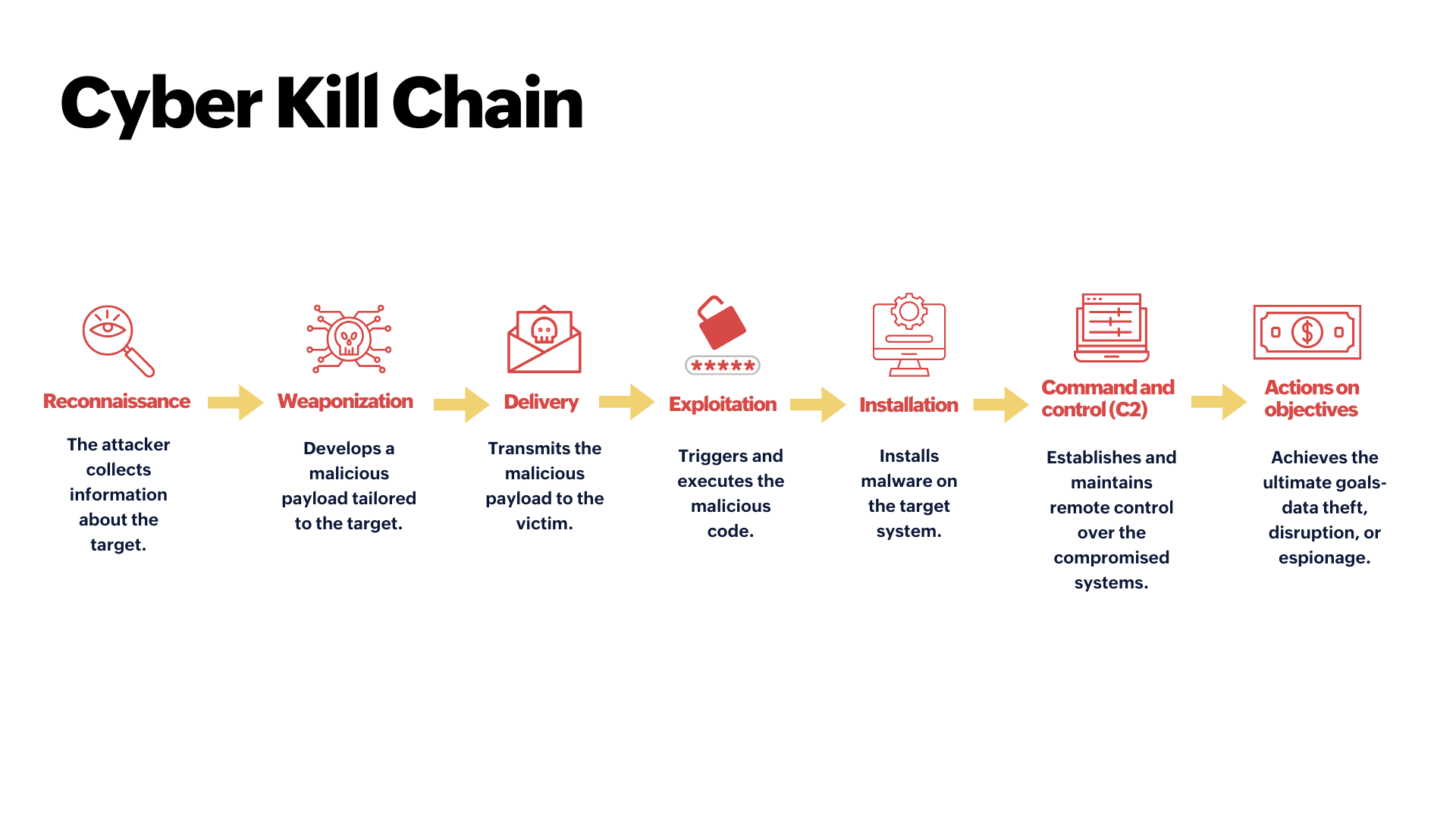
Inside the Cyber Kill Chain
For employees, this isn’t about knowing technical jargon; it’s about seeing how these steps play out in real time, how attackers manipulate human behavior, and how they exploit seemingly harmless actions.
In some stages of the Cyber Kill Chain, employees may encounter subtle signs of a potential threat—like an unexpected email or login prompt. While they aren’t responsible for directly intervening, recognizing these signs and reporting them promptly supports early detection and strengthens the organization’s defenses.
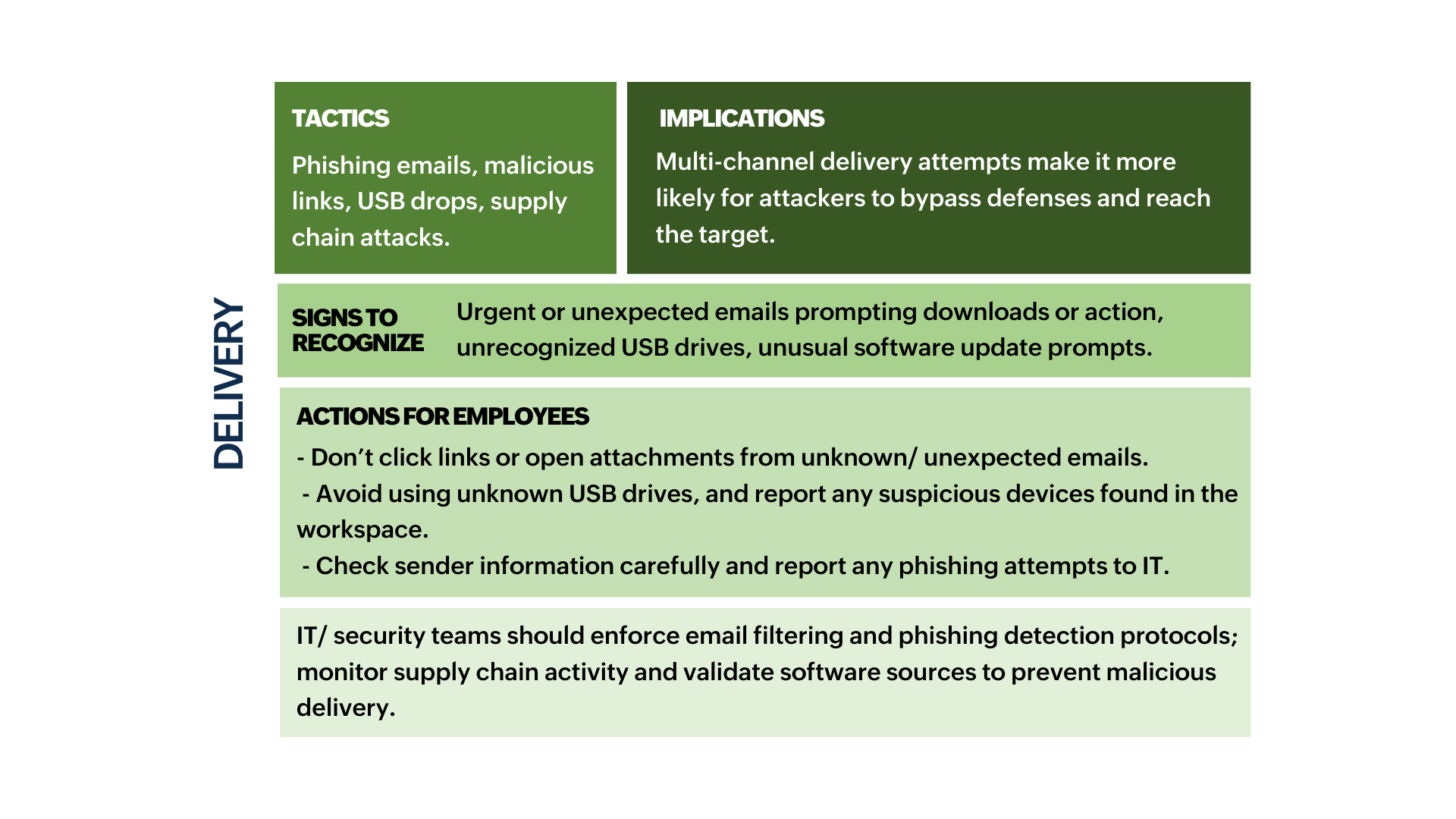
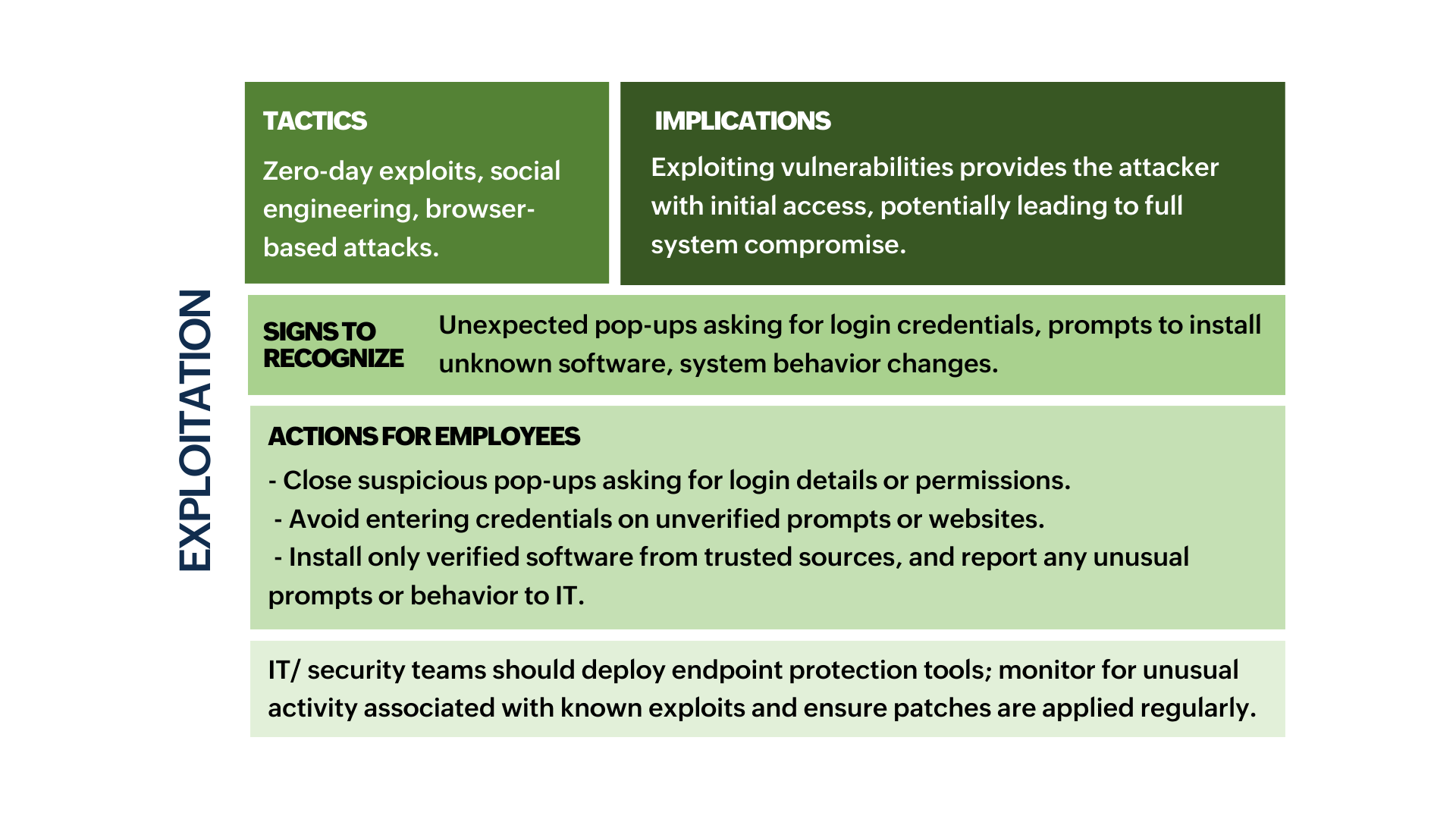
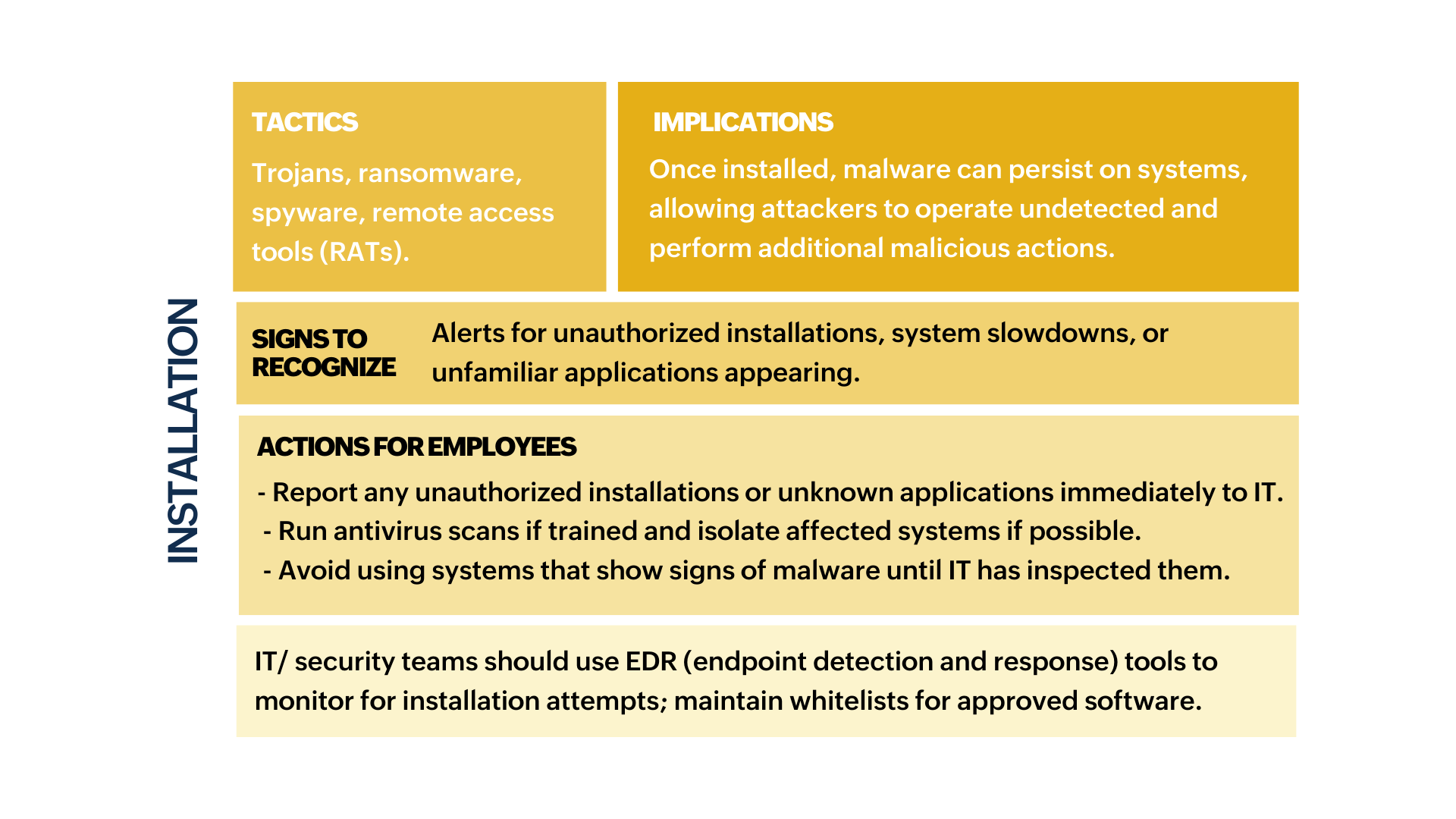
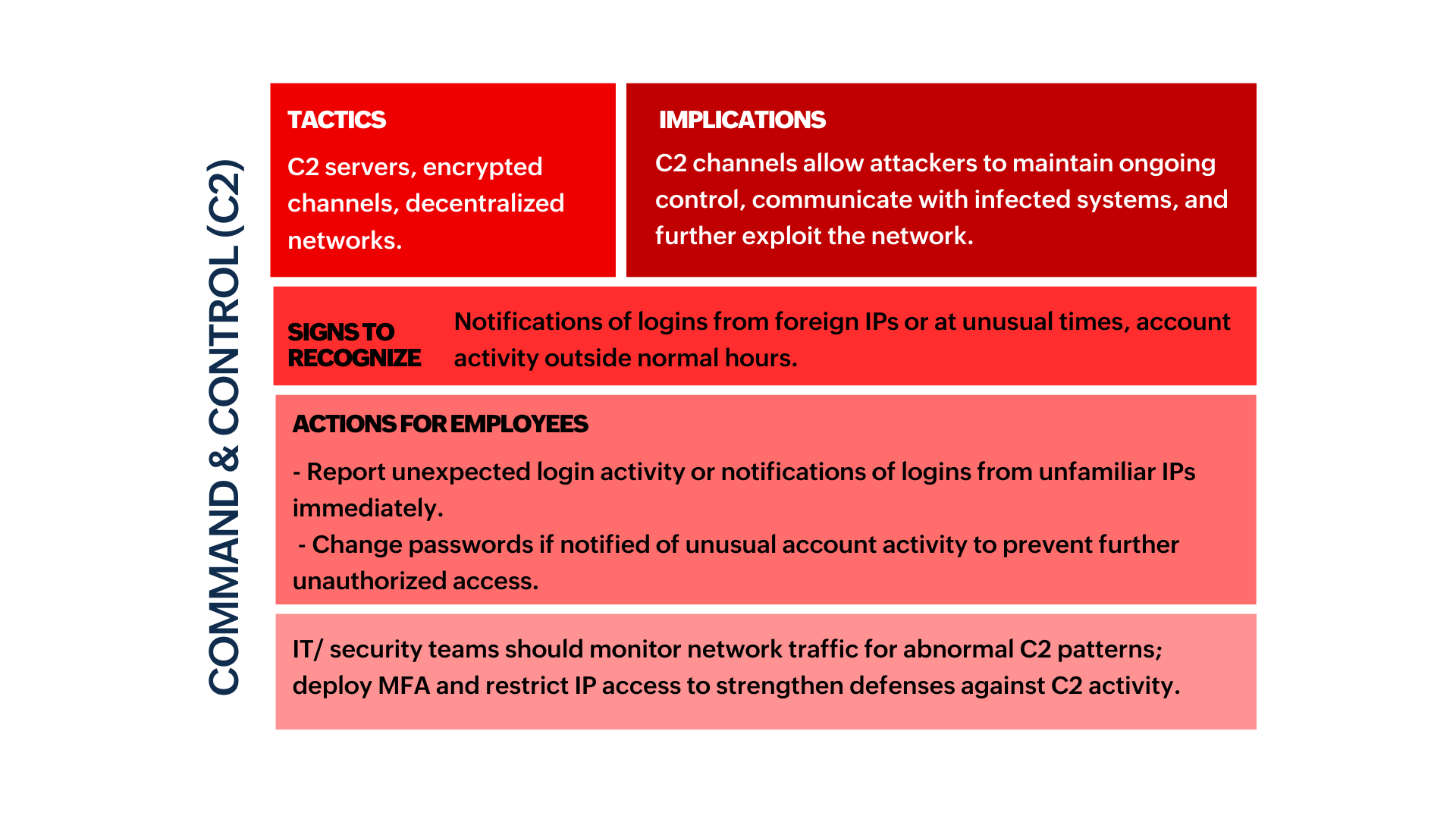
- The sections marked in green indicate stages where employees are likely to encounter or recognize signs of an attack and can take preventive actions.
- The sections marked in red indicate stages where detection and response are almost exclusively handled by IT/security teams due to the technical nature of the actions.
- The sections marked in yellow indicate stages where both employees and IT teams have roles, with employees spotting suspicious activities and IT teams taking control of containment and recovery.
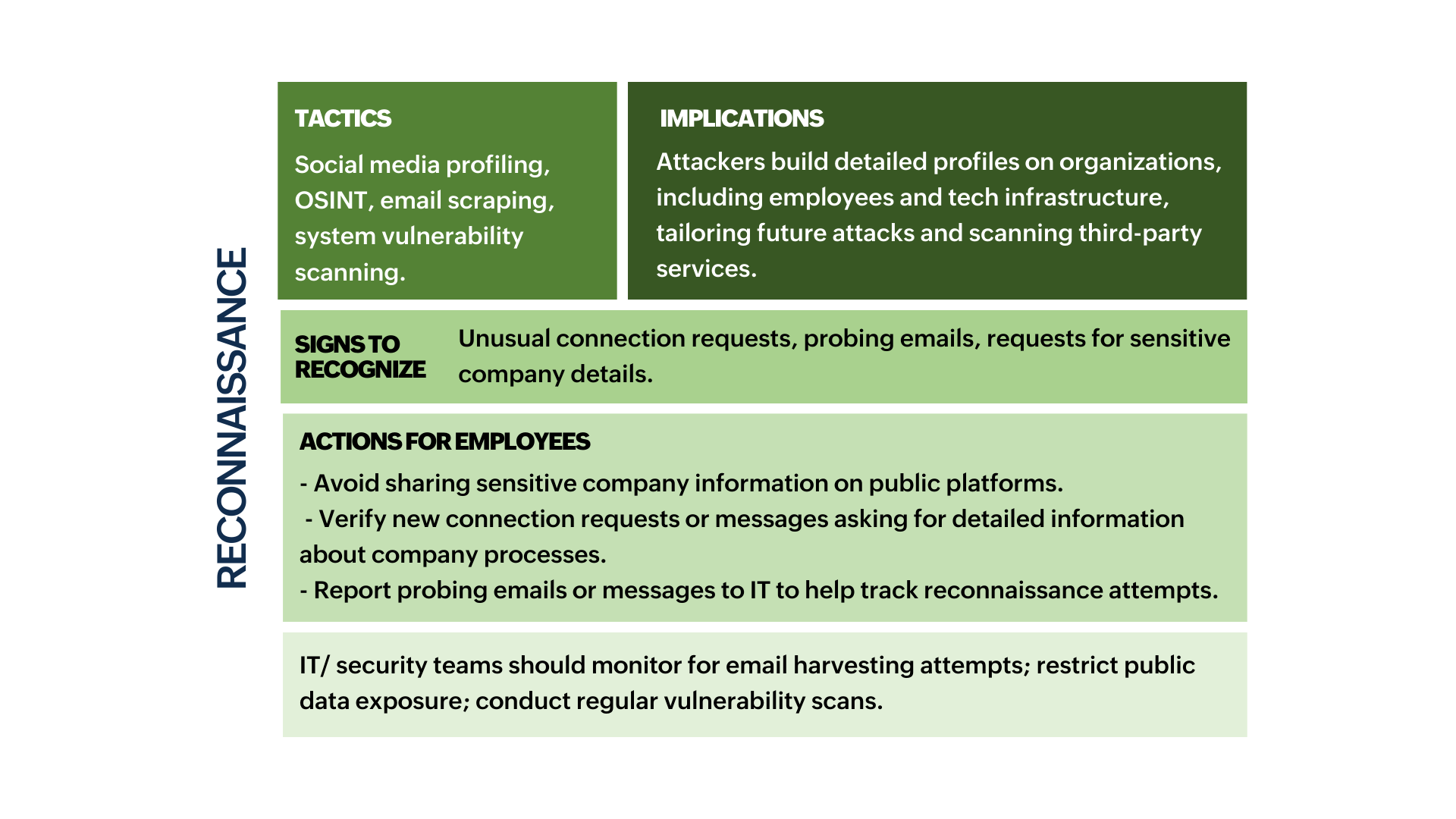
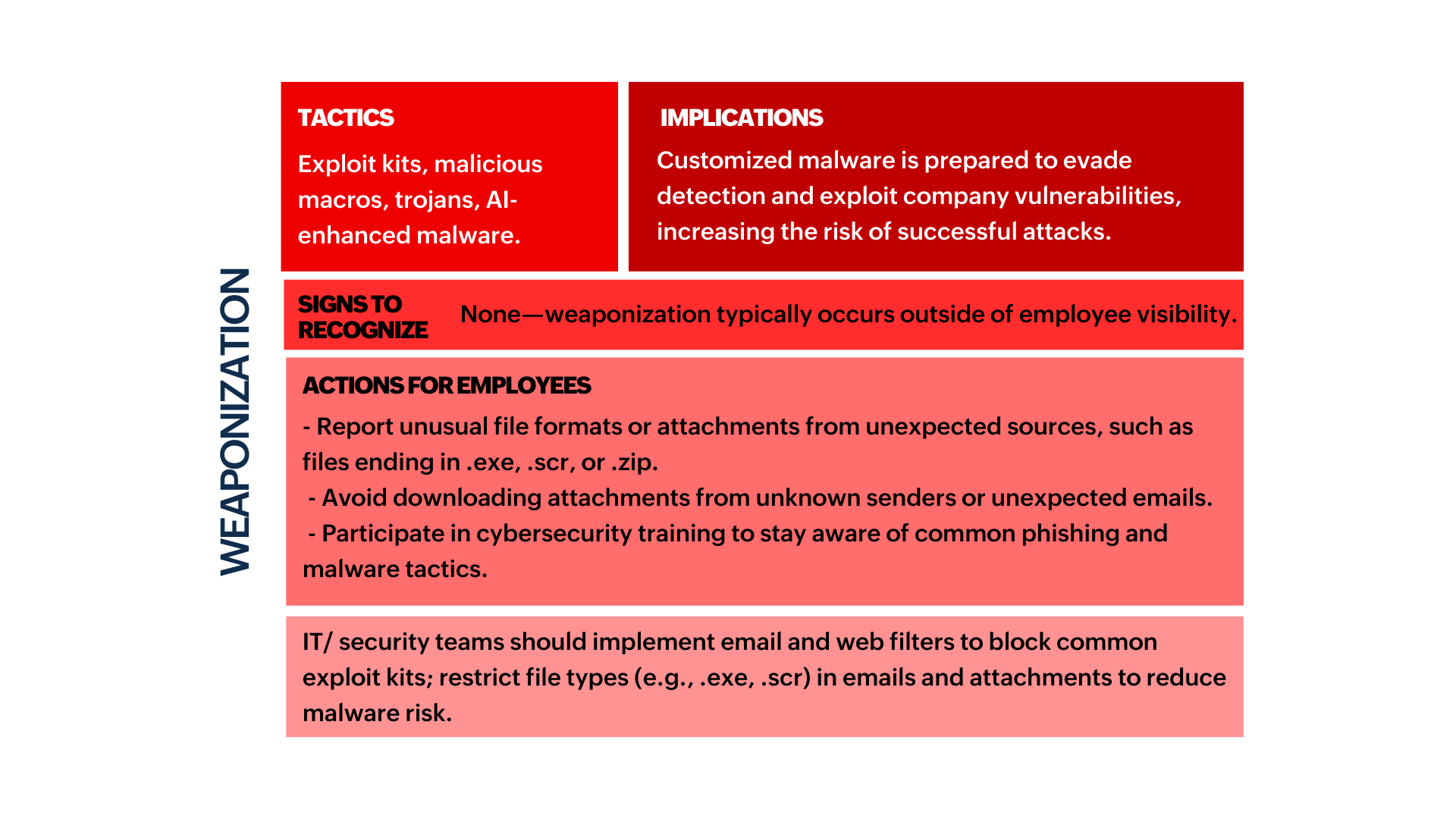
To effectively embed this knowledge across your organization, consider the following measures:
Training sessions: Conduct regular, engaging training sessions on identifying phishing attempts, recognizing unusual system behavior, and understanding secure online practices. Implement phishing simulation platforms like KnowBe4 or Cofense and use them as a basis for your training materials.
Policies and reporting: Ensure there are clear, well-documented policies on cybersecurity practices. Establish simple, straightforward reporting mechanisms so that employees can quickly inform IT teams about potential threats.
Conclusion
The Cyber Kill Chain isn’t just a technical framework; it’s a strategic defense blueprint that empowers employees to act as the first line of defense against cyber threats. By understanding each stage, employees can anticipate potential attacks, respond swiftly, and disrupt malicious actions before they escalate.
Today, security is a shared responsibility. When employees stay vigilant, report anomalies, and follow best practices, they not only protect themselves but also shield their colleagues, customers, and the company as a whole. Let’s make cybersecurity an integral part of our everyday routine—one that secures not just our data, but the future of our organization. Together, we can build a resilient, secure digital environment.
This article is co-authored by Sandeep Kotla and Vignesh S.
Sandeep is an accomplished inbound marketer at Zoho Corporation, specializing in digital workplace strategies, digital transformation initiatives, and enhancing employee experiences. Previously, he handled analyst relations and corporate marketing for Manage Engine (a division of Zoho Corp) and its suite of IT management products. He currently spends most of his time re-imagining and writing about how work gets done in large organizations, reading numerous newsletters, and Marie Kondo-ing his inbox.
Vignesh works as a Marketing Analyst at Zoho Corporation, specializing in content initiatives and digital workplace strategies. He's a passionate creator with a penchant for marketing and growth. In his free time, you can see him shuffling between books, movies, music, sports, and traveling, not necessarily in the same order.













