- HOME
- Email security threats: types and best ways to identify them
Email security threats: types and best ways to identify them
- Last Updated : December 2, 2024
- 2.1K Views
- 9 Min Read
For long, cyber attackers have preyed on emails as one of their most common targets. Though business communication has evolved, email has stood the test of time and is still one of the most preferred forms of official communication. Attackers find email to be a lucrative and attractive target because of the abundance of sensitive information shared through it. Email threats can be broadly classified into five different types.
Types of email security threats
Email security threats can be broadly classified as spam, phishing, spoofing, malware, and zero-day attacks. While these are just mechanisms, attackers come up with new and innovative ways of penetrating users' mailboxes using these mechanisms. In this article, we’ll take a look at the types of email threats and samples of each type of threat. This will help you spot fraudulent emails if there is an attack on your organization.
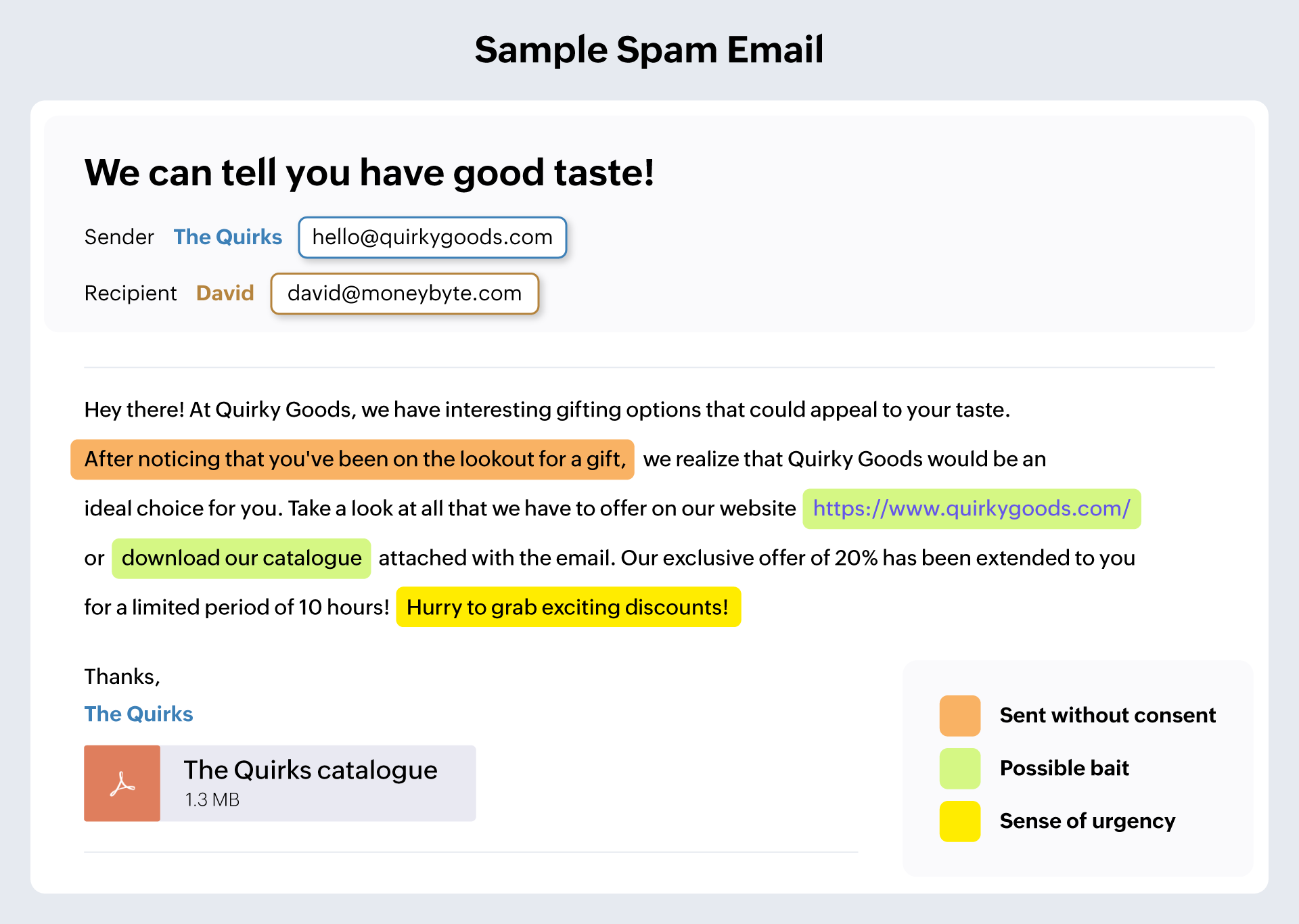
Spam
Spam refers to any unsolicited or bulk emails that find their way into your mailbox. These are usually emails from newsletters or subscription lists that you’ve specifically given your email address to. Email addresses are usually obtained by scraping websites, from purchasing lists, or by other indirect means. Spam attacks are usually not very targeted but the bulk nature of these emails usually yields at least a few conversions which could be the target of attackers.
Spoofing
Spoofing is when cybercriminals mask their identity and assume the identity of someone that the recipient trusts. This could take the form of a brand that's popular or someone who's very familiar with the recipient or the organization. Spoofing is one of the most common mechanisms used in phishing attacks. Most spoofing attacks occur when emails fail the SPF, DKIM, or DMARC authentication, leading to unverified sending domains or email addresses.
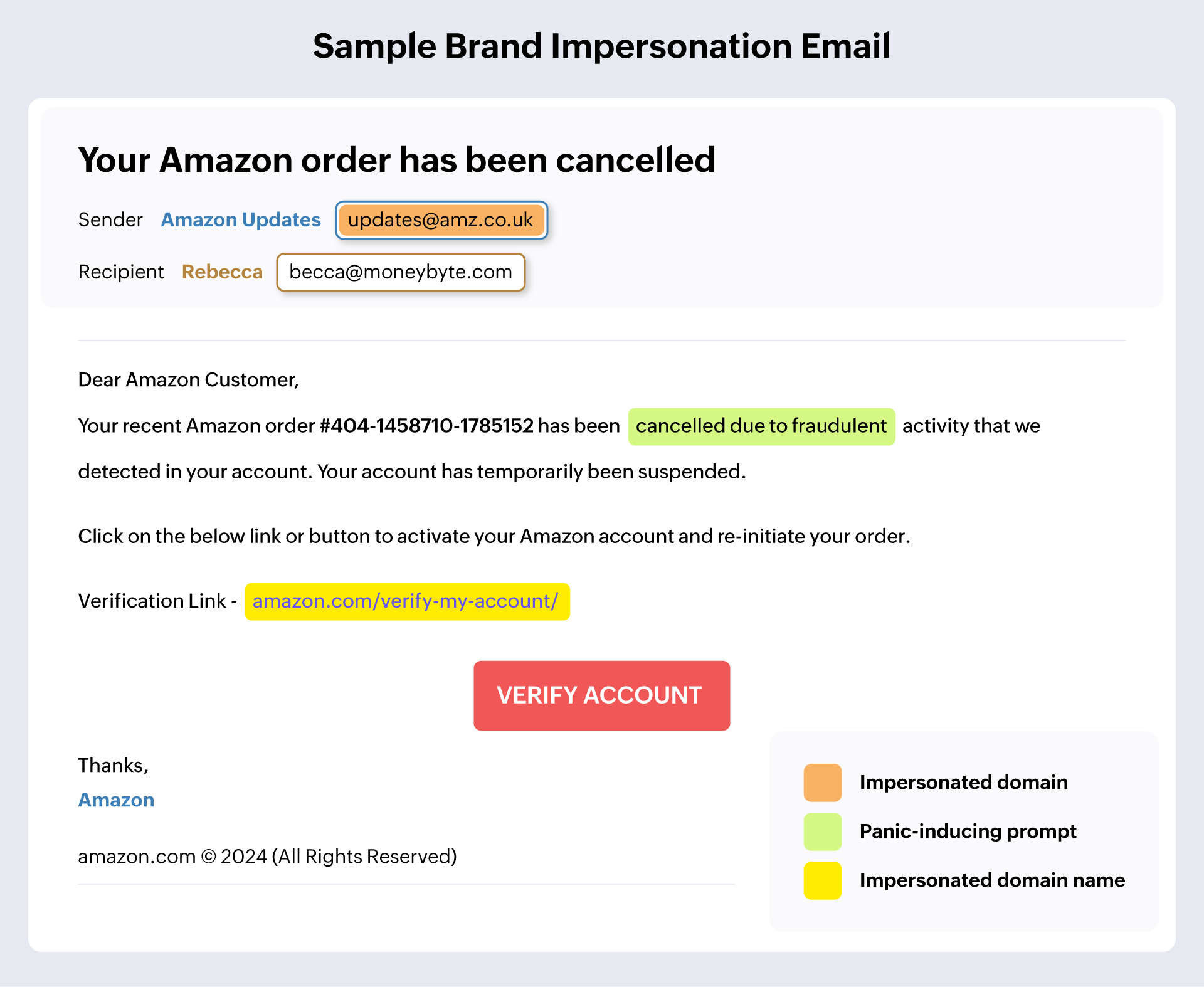
Domain or brand impersonation
Domain impersonation or brand impersonation is a spoofing technique where attackers mask their identity and emulate a reputed brand to get email recipients to trust them. In this technique, attackers use a spoofed domain that might look identical to a reputed brand's domain name. The spoofed domain name might have one or more letters in the name replaced with close lookalikes. Email recipients might mistake the sender email address to be from a legitimate domain and get tricked into trusting the email. Attackers might try to get a payment done, reveal sensitive information, or lead them to a website that requests them to enter personal details.
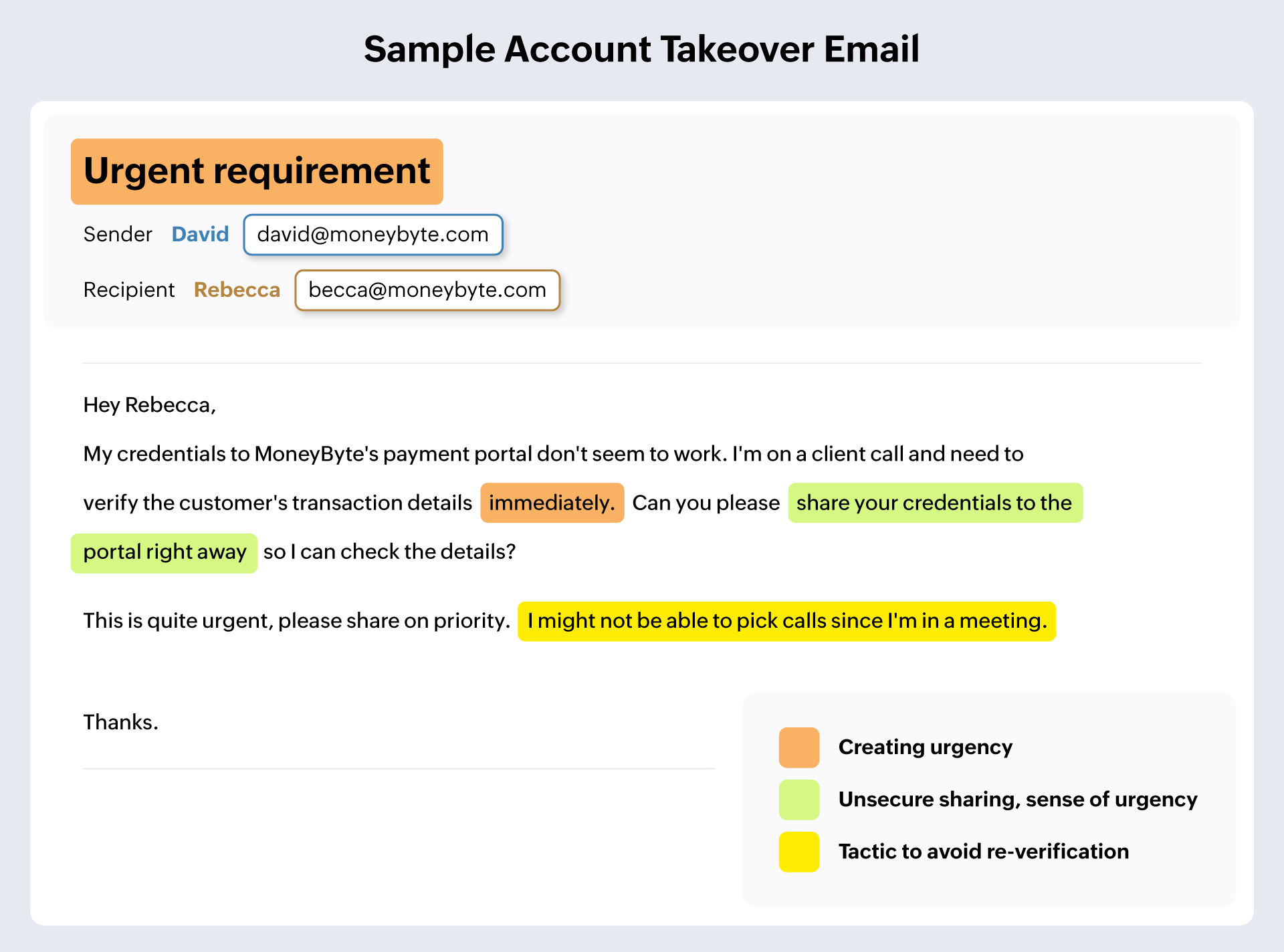
Account takeover
Account takeover refers to the process in which attackers gain access to an account and pose as the actual owners of the account. They may gain access through leaked passwords, or simply hack accounts that don't have the necessary level of protection. Once they gain access, attackers might change the login details and recovery options to prevent the actual owner from getting into their account. Then they use the owner's identity to either retrieve information from their contacts or sometimes for financial gains.
Conversation hijacking
An outcome of account takeover is conversation hijacking. Hackers use the identity of the account owner and have conversations with their contacts. They perform adequate research on prior conversations in the account and emulate their style of emailing so that email recipients respond without questioning it. Hackers might start new conversations or steer the course of ongoing conversations in these accounts in such a way that it profits them with essential information.
According to IBM's Cost of a Data Breach Report 2023, USD$4.45 million was lost in data breaches that occurred through account takeovers. It’s crucial to detect attempts of account takeover and conversation hijacking promptly.
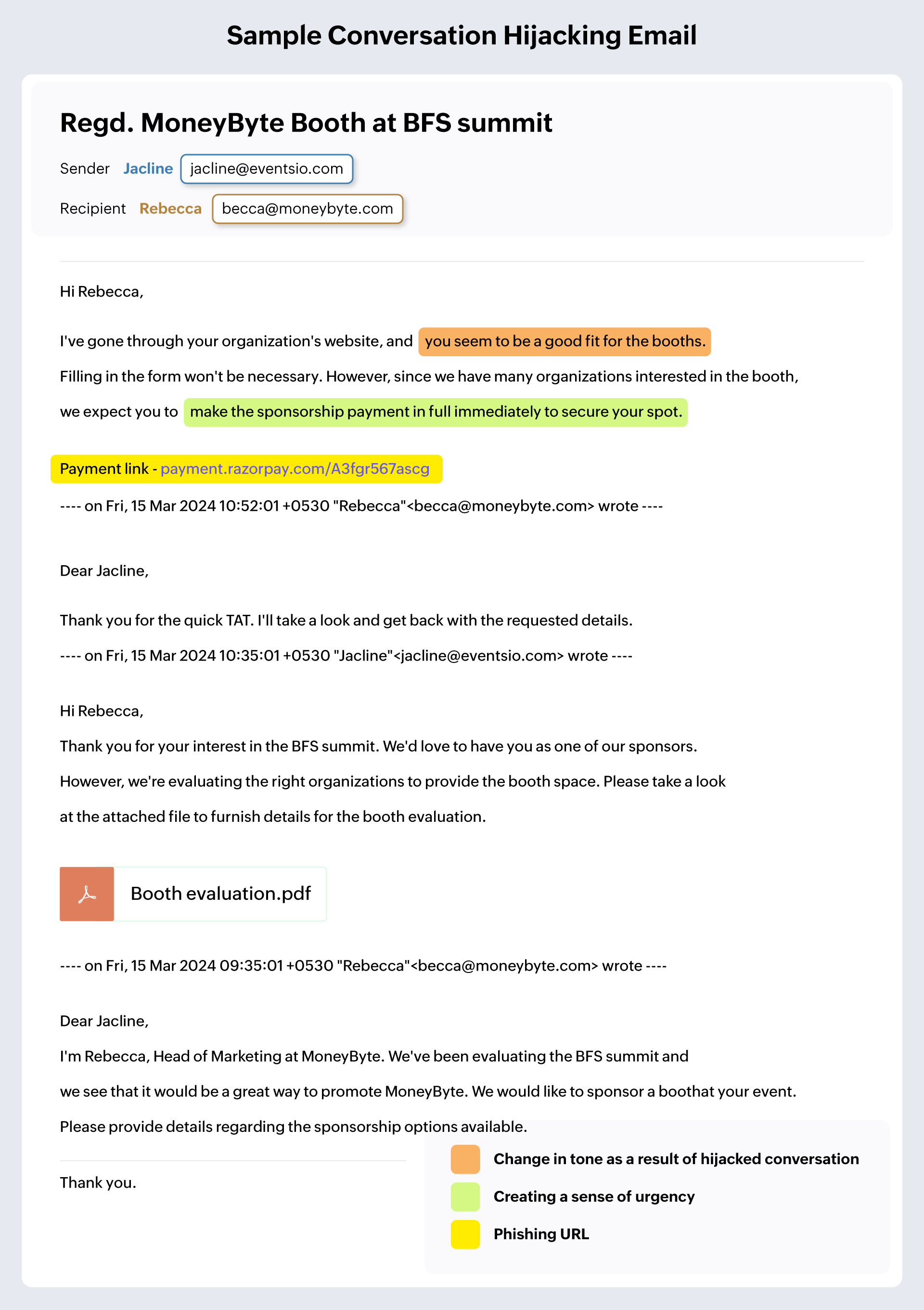
Explanation of the attack:
In the above example, events.io has been hacked. If you closely observe the conversation, you’ll notice that there’s a change in tone between the first and second emails addressed to Rebecca. In the first email, the sender, Jacline, mentions that a stringent policy will be followed to provide the booth space. In the second email, Jacline responds to Rebecca's email with enthusiasm about their partnership for the event. An important factor to be noted here is that Jacline responds even before Rebecca gets back with details. Additionally, there is a sudden urgency in the tone and a nudge to make the payment immediately. These details could point to a potential conversation hijacking attack and pose a need to exercise caution before responding.
Phishing
In phishing attacks, threat actors masquerade as email senders from reputed or trusted entities and lure email recipients into trusting them. This technique is commonly referred to as social engineering. Phishing emails contain hooks that nudge recipients to divulge sensitive information such as credit card numbers, account credentials, social security numbers, and more. Cyber attackers use this information to extract money, pose as the account owner, or even monitor the emails of a particular organization's employee to cause large-scale disruption. Attackers make the content enticing and urgent enough to get email recipients to respond or react to their emails.
Business email compromise
Business email compromise is one of the most common phishing attacks where the attacker assumes the identity of a trusted person or organization familiar with the email recipient and tricks them into performing a sensitive action, such as revealing the credentials of an important account, authorizing a financial transaction, or logging into a safe lookalike website that could actually be a scam website tailored to deceive people.
Though it accounts for only 4% of all breaches, BEC has cost businesses an average of $5 million per breach.
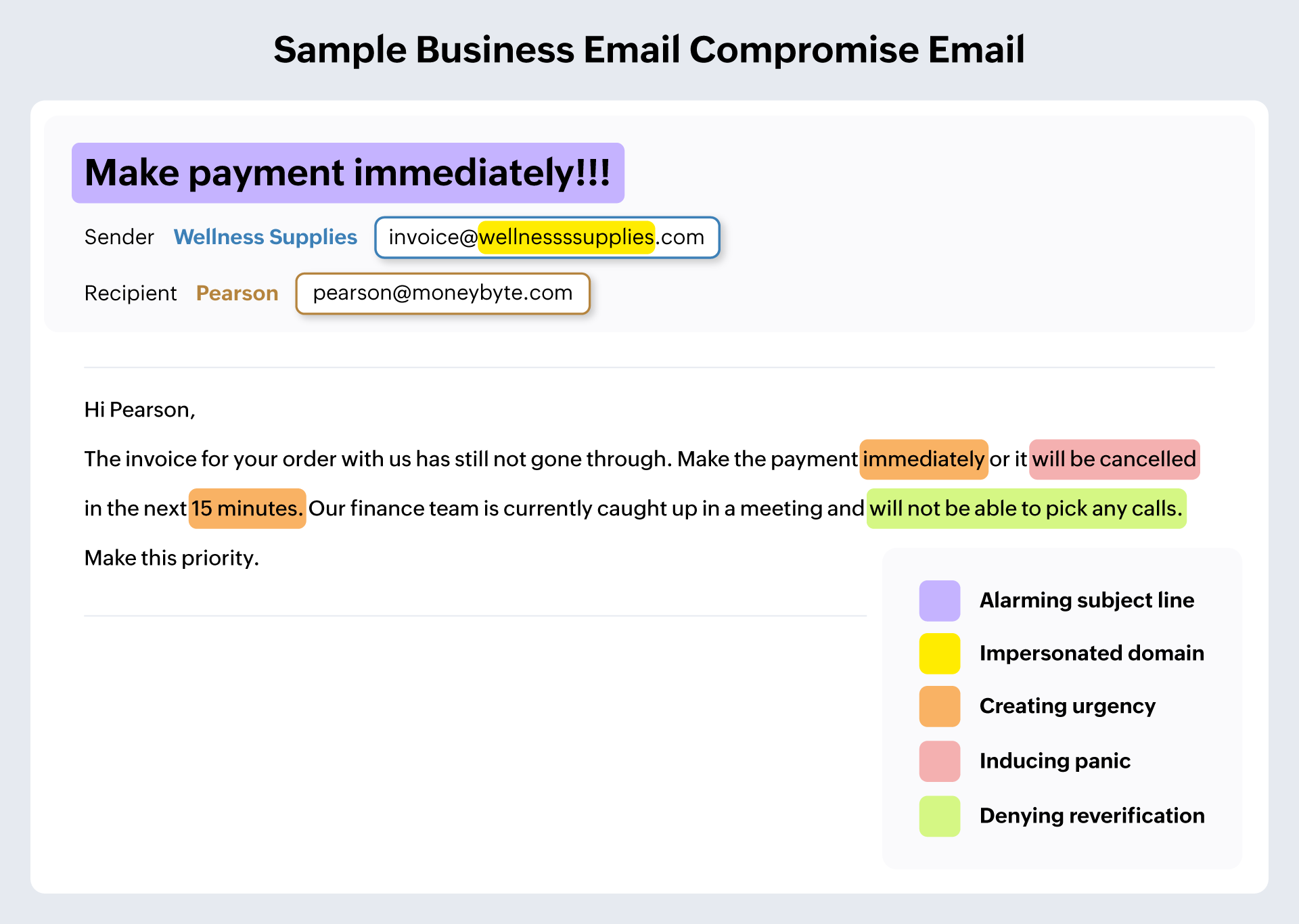
VIP fraud or CEO fraud
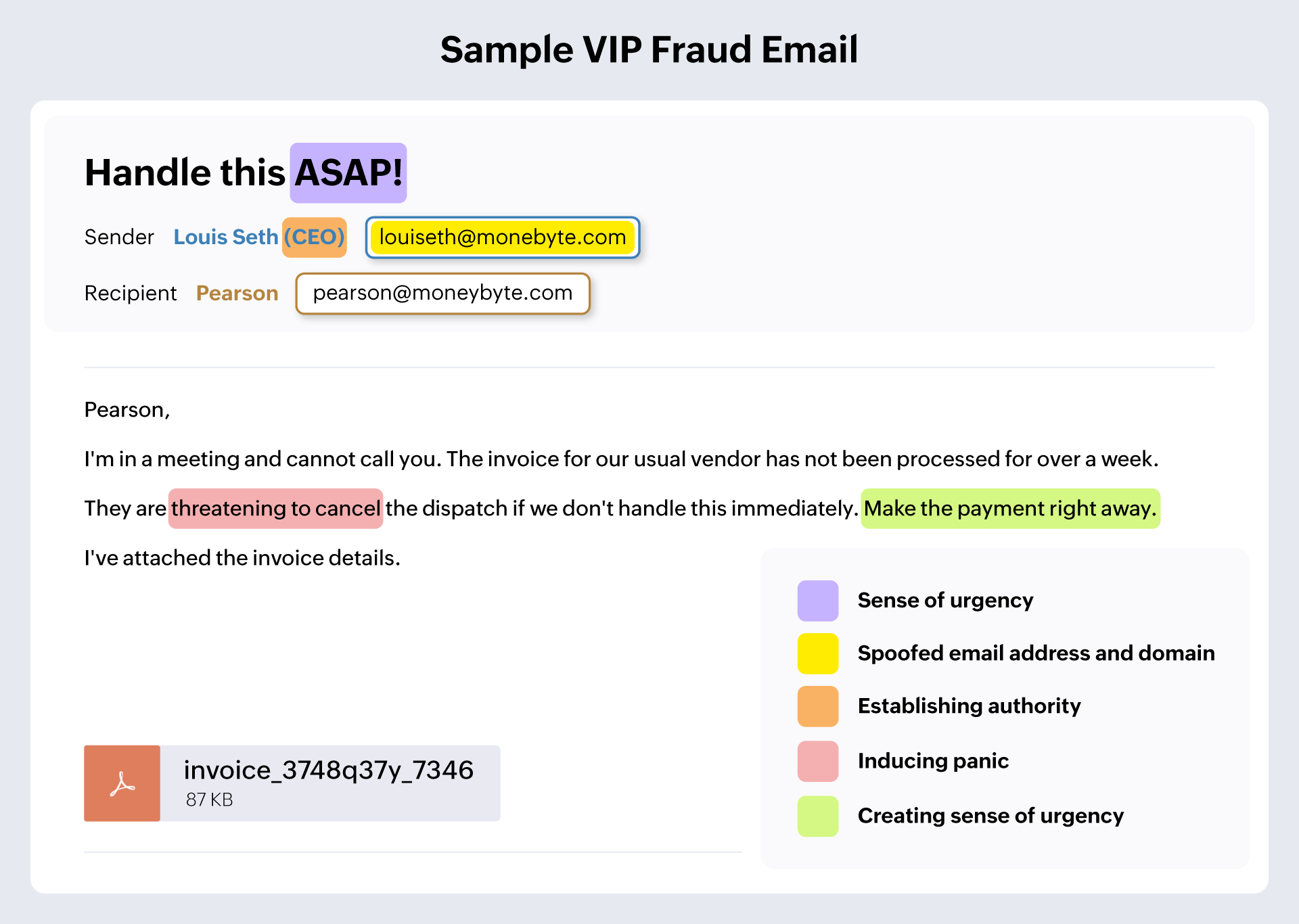
VIP fraud (sometimes referred to as CEO fraud or whaling) is one form of business email compromise, except that the person the attacker is impersonating is a high-profile executive of an organization. This could be someone such as the CEO, CFO, or other senior personnel of the organization. VIP fraud can either be from an email address spoofed to imitate the high-ranking professional, or the attacker could have taken over the actual email account of the person. VIP fraud often creates a sense of urgency because the email is from a high-ranking official, and recipients react to the email without pausing to check if the email is legitimate.
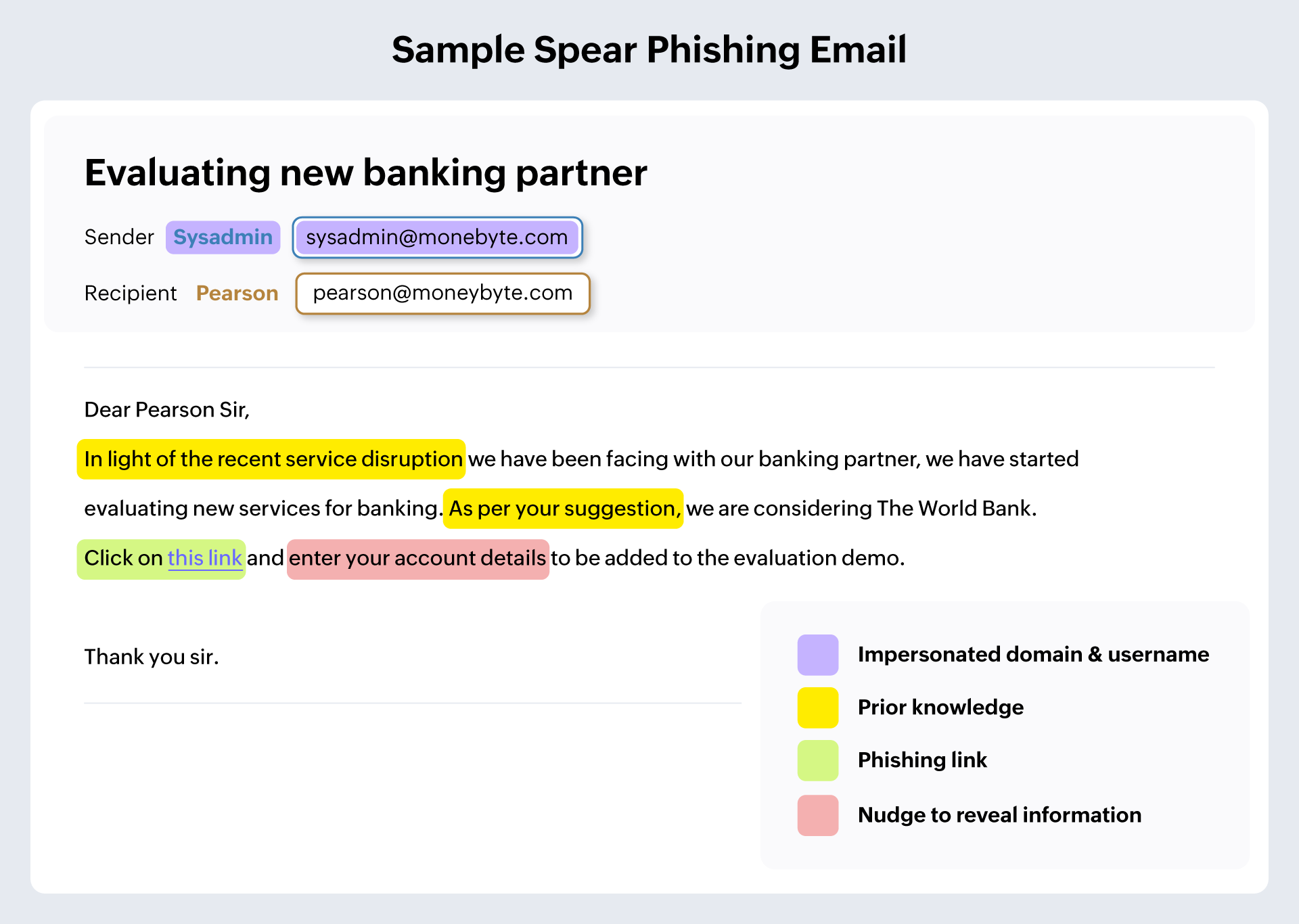
Spear phishing
Most phishing emails are sent to unspecified targets. But with spear phishing, the attackers conduct sufficient reconnaissance and investigate the specific person they intend to target. This helps them understand patterns, behaviors, and know the people they regularly interact with. They emulate someone the target closely interacts with just using enough knowledge and phish for very specific information that could be part of a larger attack. Due to the personalized nature of the attack, the target falls prey to the email.
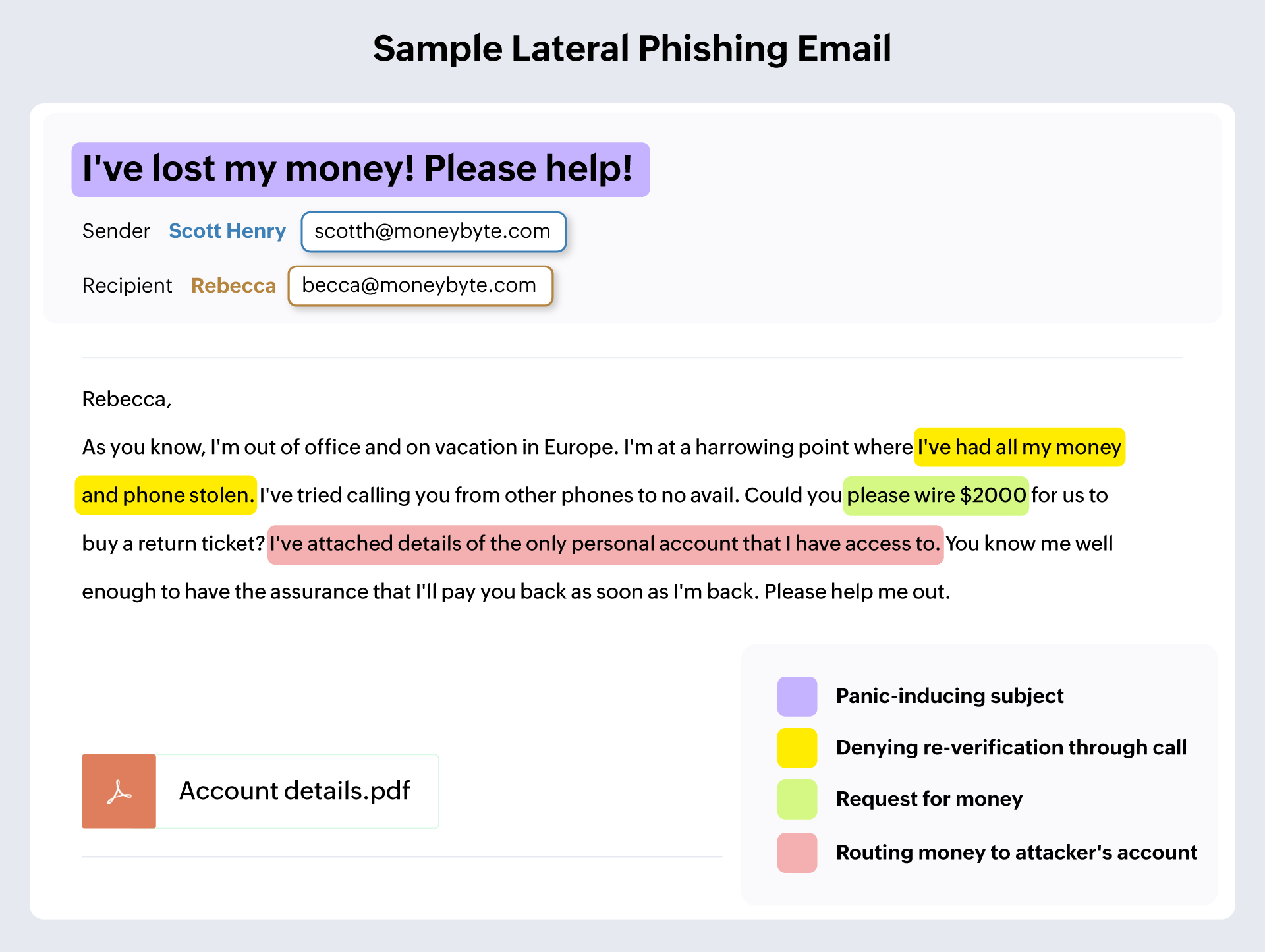
Lateral phishing
Lateral phishing attacks usually begin with an account takeover. Attackers prey on unsuspecting users whose accounts have recently been compromised. They assume the account owner’s identity to send emails to close contacts both within and outside the organization. The recipients assume that the account owner sent the email because the email address remains unchanged, and they resume the conversation without exercising enough caution. Lateral phishing attacks pose an increasing threat in the current cybersecurity landscape because they bypass most security measures without being detected.
Quishing
Quishing refers to phishing attacks that make use of QR codes to extract information. These QR codes are designed to lead the recipients to a malicious website that could download malware onto their system or extract information such as account details or other personally identifiable information (PII). The QR code is attached as an image to the phishing email under the pretext of being something innocuous, such as a product brochure or a voice message. The recipients scan the code and are led to expose sensitive information. Quishing attacks tend to bypass usual security measures because most security filters identify QR codes as images that don't cause any harm. Email recipients should be wary of these attacks by verifying the URL that the QR code leads them to.
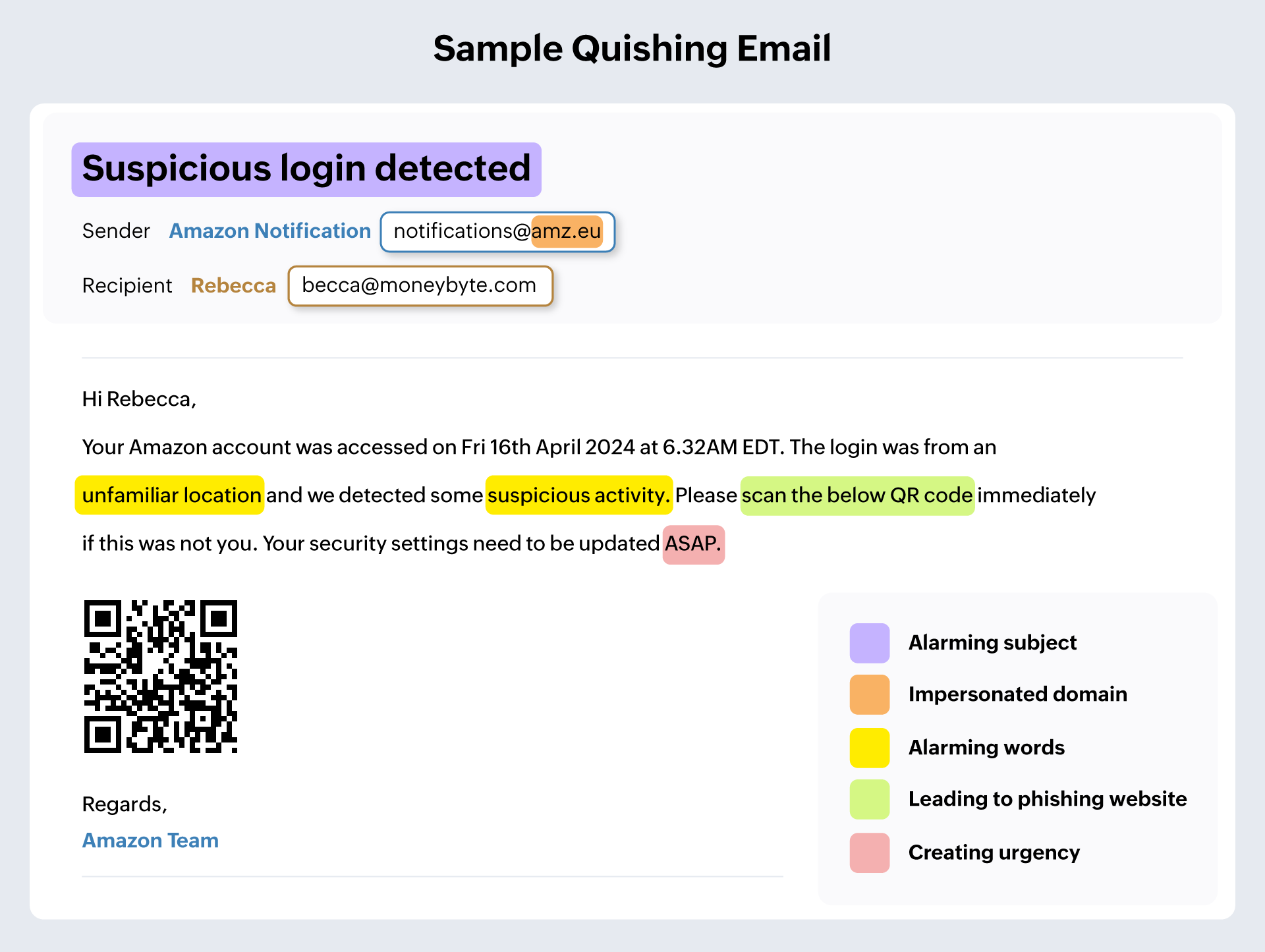
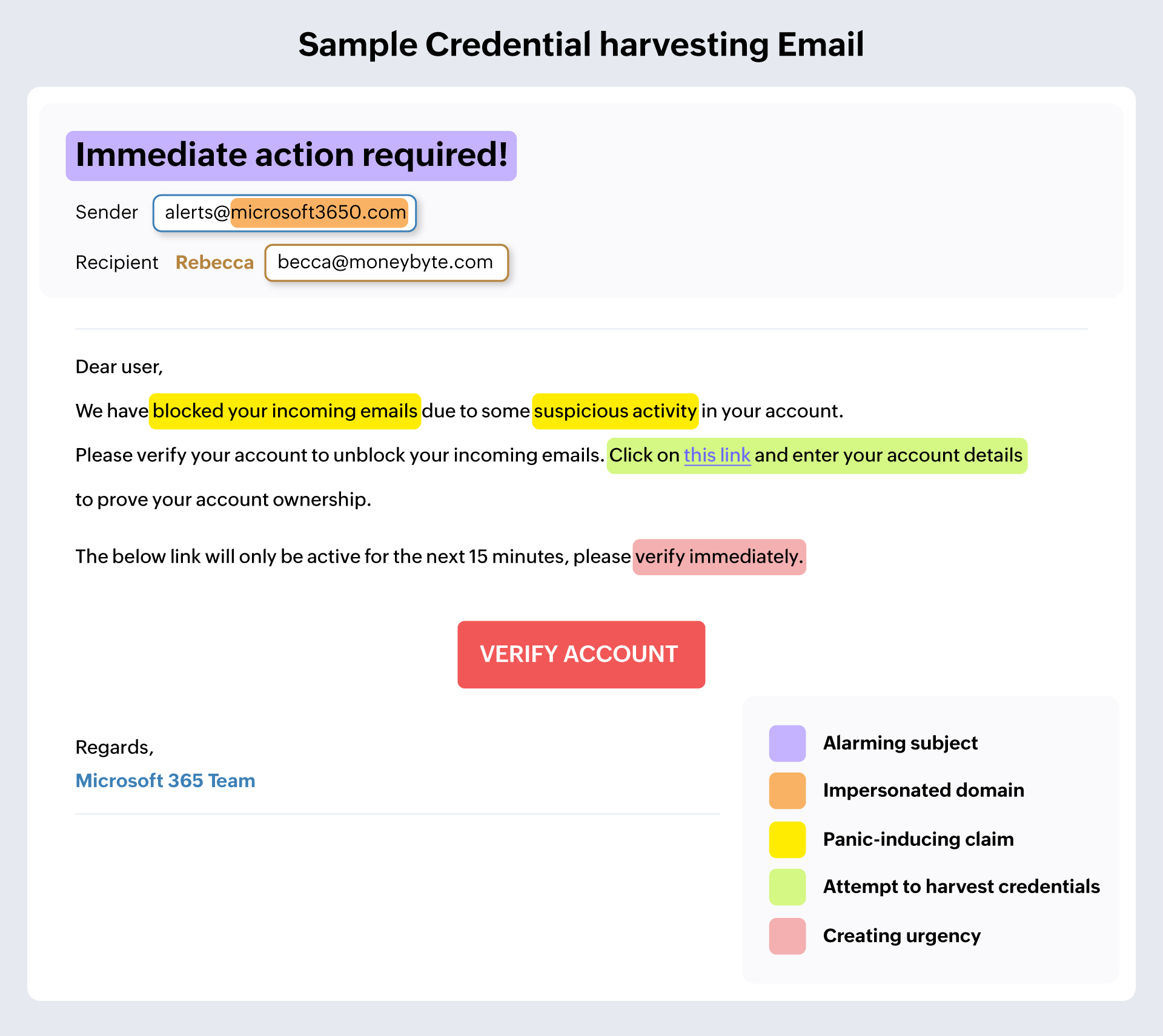
Credential harvesting
Credential harvesting attacks usually aim to make email recipients reveal their credentials to a particular account, which they can later use to plan a bigger attack. The email sender poses to be a legitimate entity, such as a banking institution. They include a URL to a website that could be a very close lookalike of the actual institution, and the user is nudged to enter their credentials. In the background, this is just a phishing website that collects the entered credentials and uses them either to transfer money or steal the identity of the user and conduct investigations about an organization.
According to IBM's 2024 threat intelligence report, 30% of cyber attacks used valid credentials collected through credential harvesting attacks.
Man-in-the-middle attack
Man-in-the-middle (MitM) attacks refer to scenarios where attackers insert themselves in a position to intercept the communication between the email sender and recipient. They can usually achieve this position through unsecure WiFi networks, DNS spoofing, or other such network-level issues. The intruder monitors the communication that happens between the two parties and analyzes patterns to launch a bigger attack. Sometimes, the intruder also has the unique position to modify the messages from the sender. These attacks mostly happen without either parties realizing that their conversation is being eavesdropped on. It mostly comes to light only when the attacker uses this information in a forthcoming attack and the root cause comes to light.
Malware
Malware, or malicious software, refers to the broad range of cyberthreats that can infect and damage a computer system or an entire network. Malware is usually sent in the form of links, attachments, executables, embedded scripts, or downloadable documents that can further block access to important files in your system or steal data. This happens when these attachments or links are downloaded or clicked on. Sometimes, malware can even run in the computer's background, collecting data about user behavior and identifying patterns without the user even being aware of its presence.
According to one report, almost one in 10 emails was identified as being malware compromised.
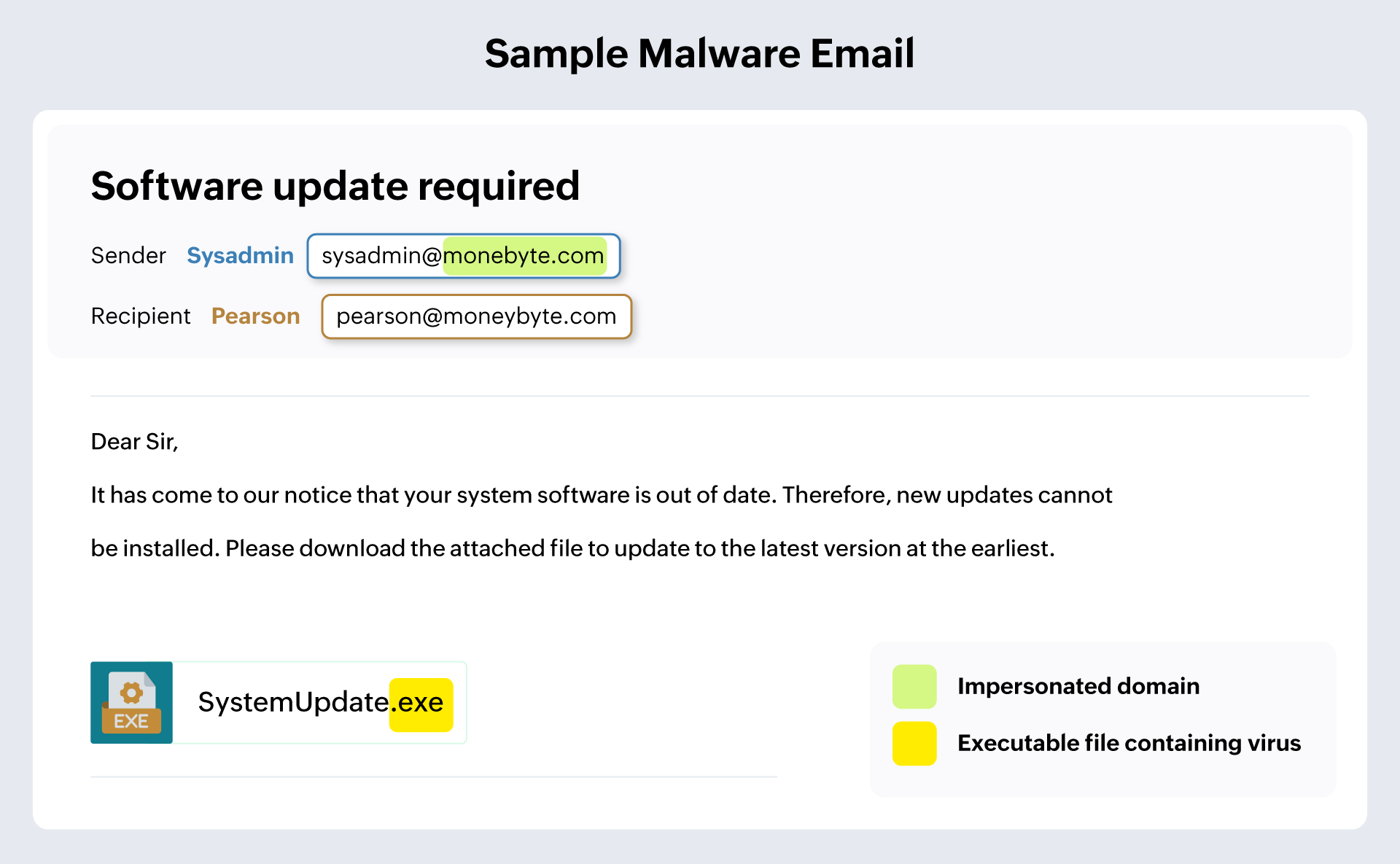
Viruses
Viruses are a type of malware usually present in files or documents. When sent through an email, the recipient might download the attachment without realizing the malicious nature of the attachment. The attachment containing the virus is then downloaded onto the computer, and once the file is opened, it could erase important files on the system or encrypt the files and deny access to the user.
Ransomware
Ransomware is one of the most common and lucrative types of malware. In this type of attack, the threat actor designs a type of virus that locks the actual user out of their computers or denies access to specific important files. The documents are encrypted and can be unlocked only by the attacker. The attacker demands a specific amount of money, and only when they receive it will they unlock the account and the user gets access back. Sometimes, threat actors deploy a double-extortion technique, where they post sensitive information on the dark web if their claim is not met.
Spyware
Spyware is a type of malware that can be sent in the form of attachments via email. When the file or document containing spyware is downloaded onto the system, it can secretly monitor financial transactions or other actions the user takes on their computer. One specific form of spyware is keylogging, where hackers collect data through keystrokes or reveal passwords to help with credential-harvesting attacks. Spyware is usually installed onto a system in the early stages of a larger attack.
Zero-day attacks
Zero-day attacks are launched by exploiting vulnerabilities in the computer or network before the developer or the end user has even had a chance to recognize the vulnerability. These attacks are in the form of code and most commonly delivered through email by deploying social engineering tactics. Once the email recipient downloads the file containing the code, it runs on the computer causing havoc on the system. Because these attacks use unexposed vulnerabilities, the attacks haven’t been commonly witnessed before. This makes the attacks difficult to combat and get access to the data back.
Wrapping up
Every year, novel email threats keep getting added to the list of known attacks as hackers find innovative and evasive ways to get past email defenses. To detect anomalies in emails and to secure your business's email environment from external threats, it's best to use a robust cloud email security solution or an email security gateway.
eProtect is one such cloud-based email security and archiving solution that provides an additional layer of security for email accounts. The solution offers advanced threat detection mechanisms that can secure on-premise and cloud email accounts from evolving email threats. eProtect is the security solution powering Zoho Mail, a platform trusted by millions of users.