- HOME
- Payment processing
- Secure transactions with payment tokenization
Secure transactions with payment tokenization
By Chandramouli
Security and efficient payment methods have become critical to businesses. With an increase in online transactions, cyber attacks on payment data are posing a significant risk to businesses and customers. Many can recall the Capital One breach of 2017 that compromised over 100 million customer accounts leading to thousands of fraudulent transactions. Payment tokenization can act as a strong line of defense when such breaches happen.
This article throws light on the basics of payment tokenization, its benefits, and much more.
Secure transactions with payment tokenization
Payment tokenization
Payment tokenization replaces sensitive payment card information, such as Primary Account Numbers (PANs) and credit card numbers, with a non-sensitive unique identifier known as a token. Card details are converted into random characters, making them incomprehensible to unconcerned parties during payment processing. It helps mitigate the risk of data breaches and fraud.
PCI DSS (payment card industry data security standards) mandates secure storage and restricted access to cardholder data. Payment tokenization coupled with encryption plays a significant role in data security and also ensure merchants are compliant with PCI DSS.
How does payment tokenization work?
As highlighted earlier, the purpose of tokenization is to convert PAN details or credit card details with surrogate values. These values (tokens) may be stored in a token vault, which is owned by the token provider. The token creator may be an acquirer, issuer, network, or payment processor.
During the payment transaction, the merchant shares the token to its creator for checking out with the PAN or credit card details. Though the details are not sent back to the merchant, they are used to authorize the transaction with the other stakeholders of the transaction.
Step 1: Information acquisition -> Capture the payment details from customers.
Step 2: Request for tokenization -> Send the collected payment details with the tokenization provider.
Step 3: Token generation -> The token creator uses combinations of algorithms to generate a unique token that represents the given card details. The token is shared with the merchant.
Step 4: Token storage -> The token can be stored by the merchant, and when required, can be shared with the token provider during the transaction.
Step 5: Authorization -> Based on the token provider's authorization, the information is forwarded to the issuing bank for payment authentication and completion of the payment transaction.
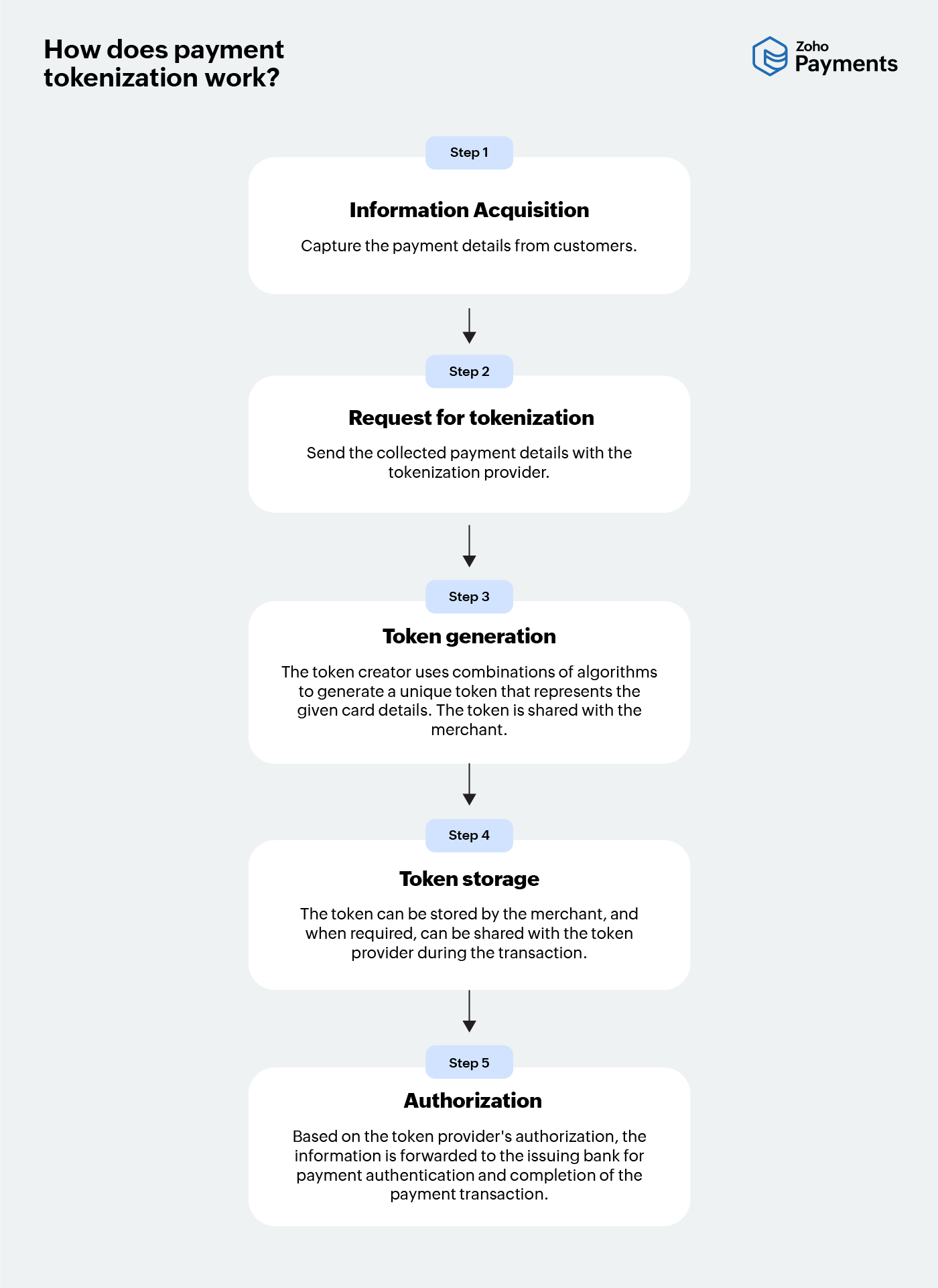
Steps involved in payment tokenization
While many steps in the above illustration are self-explanatory, token generation and storage require more of an explanation.
Token generation and storage
As mentioned earlier, the payment information is converted into randomly generated characters and symbols with the help of a strong cryptographic algorithm. The token creator then generates a unique token to represent this information.
Token formats
Non-format preserving: The card information format is completely replaced with a new format—numbers to random characters.
Format preserving: Here, the data format remains the same, however, the values change. For example, credit card info of 9878 0987 9894 8530 may be changed to 1234 2342 5432 3453.
Partial replacement: In this case, only certain values of the information are changed while the others are retained. This is helpful in cases where certain information, like the last 4 digits of the card, is sought from the user.
The tokens are non-reversible, and card information cannot be retrieved. Based on the requirements of the customer, the tokens can be generated for a single transaction or multiple transactions. For example, when a customer opts for a subscription service, the same token can be used multiple times without exposing critical payment data.
Tokens are safe
Since the information is completely changed and may be stored in vaults, it’s impossible to reverse engineer the data to find out the original information. Therefore, in the event of a data breach, only the token data is exposed. Generally, the tokens are stored in PCI-compliant vaults, which makes it difficult for the hacker to break in.
Which types of businesses need to use tokenization for payments?
Subscription services: As discussed earlier, card information is tokenized in the file to process recurring payments.
Mobile wallets: Apple Pay, Google Pay, and other digital wallets use tokenization to secure mobile transactions.
eCommerce: Customer payment information is often tokenized by ecommerce companies to facilitate one-click payments, faster checkouts, and for improving online shopping experiences.
Benefits of payment tokenization
Enhanced security: Reduces the risk of data breaches by minimizing the unauthorized use of payment information.
Quicker payments: Tokenization helps in storage and the faster use of payment information, resulting in quicker payment completions.
Reduced false declines: With tokens, processors, card networks, and issuing banks tend to decline less frequently, significantly reducing the discomfort customers may experience during a decline.
Conclusion
Securing payment information has proven to be invaluable for various industries, including subscription services, mobile wallets, and ecommerce by offering enhanced security, quicker payments, and a decrease in false declines. In essence, payment tokenization is a crucial technology that not only protects cardholder data but also streamlines the payment process, providing both security and efficiency for businesses and consumers alike.

