Why prioritizing security and privacy is key?
Maintaining robust security is non-negotiable when it comes to data. Zoho FSM’s comprehensive security controls ensure your data is protected at every step. By encrypting data both in transit and at rest, and by allowing you to define who can access what, Zoho FSM provides peace of mind. You can ensure that your operations run smoothly while keeping your data safe from breaches or unauthorized access.
Advanced encryption
Zoho FSM uses AES-256 encryption, the industry standard, to protect your data. This ensures that your sensitive information remains secure, whether it's being transmitted or stored in the system. Encryption in transit keeps your data safe during interactions between your browser and Zoho FSM servers, while encryption at rest secures your data when stored on Zoho’s servers.
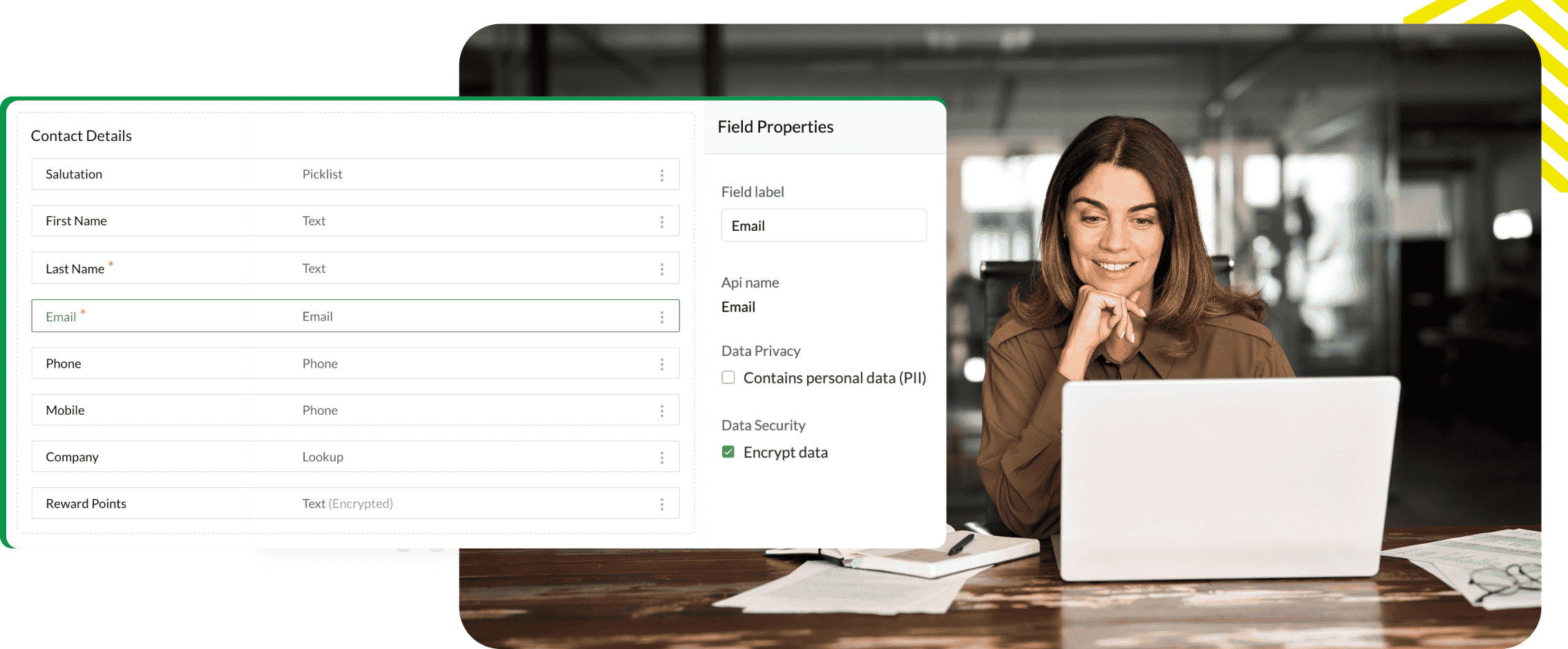
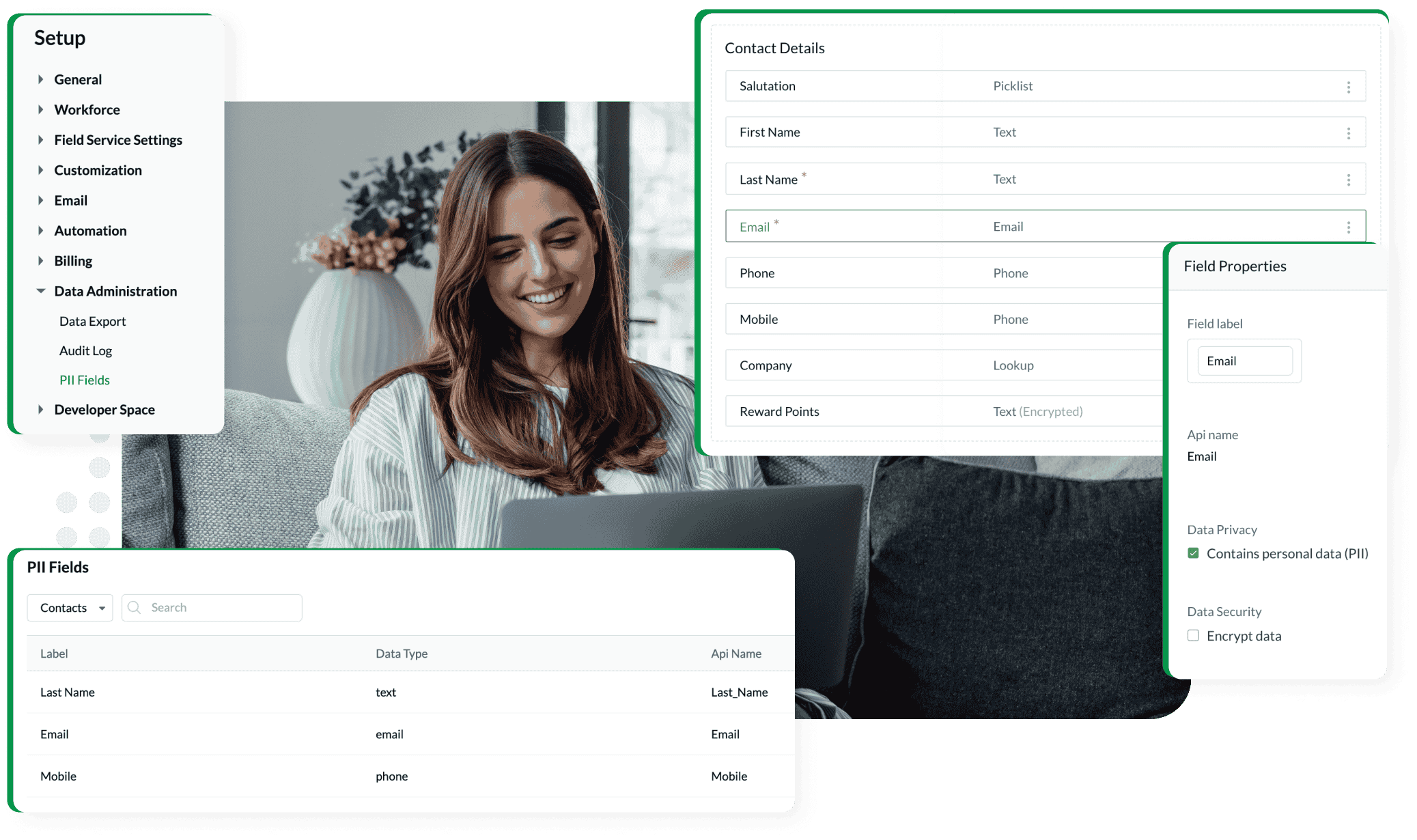
PII (Personally Identifiable Information) protection
Comply with privacy regulations by marking fields as PII. You can designate specific data—such as email addresses and phone numbers—as sensitive, restricting how this data is accessed, exported, and shared.
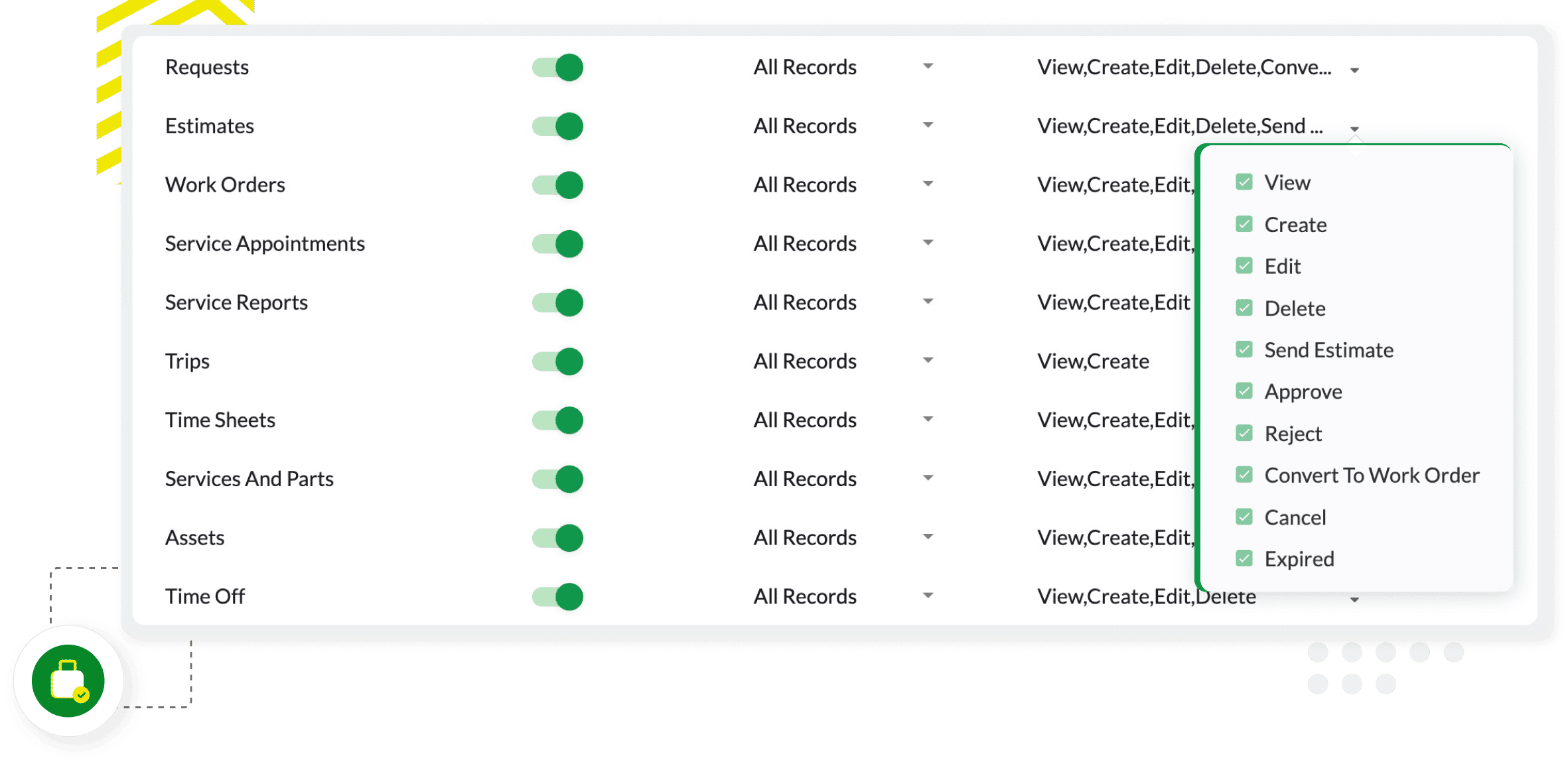
Profile-based permissions
Create custom profiles and assign specific permissions to users, controlling who can access, modify, or delete information in the system. Limit access to data by defining whether users can view all records or only those they own, ensuring that sensitive data is only available to authorized personnel.
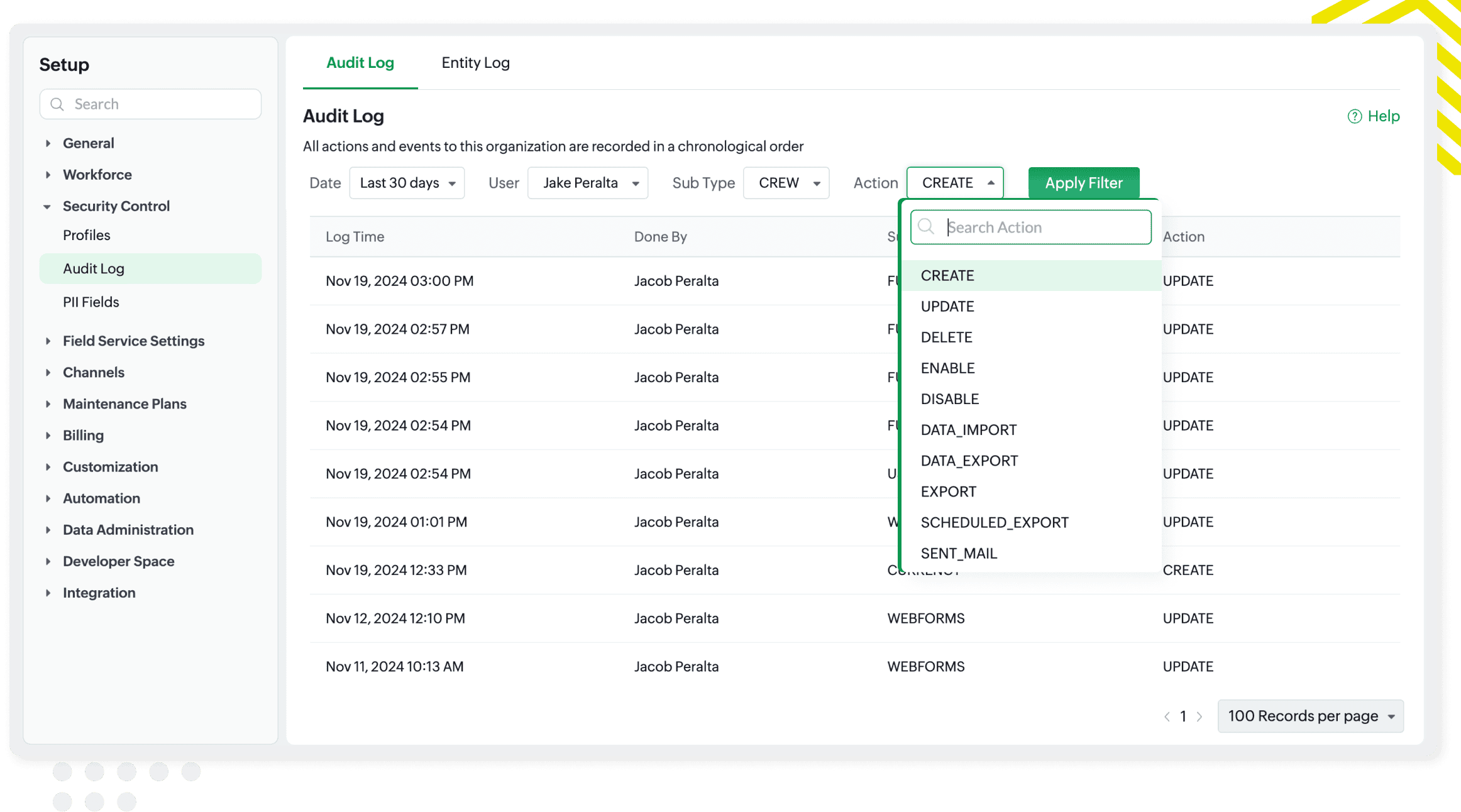
Comprehensive audit logs
Monitor all actions performed in the system with detailed audit logs. Zoho FSM tracks every modification to ensure full transparency. Filter logs by date, user, or module to identify quickly and track changes, giving you complete control over system activities.
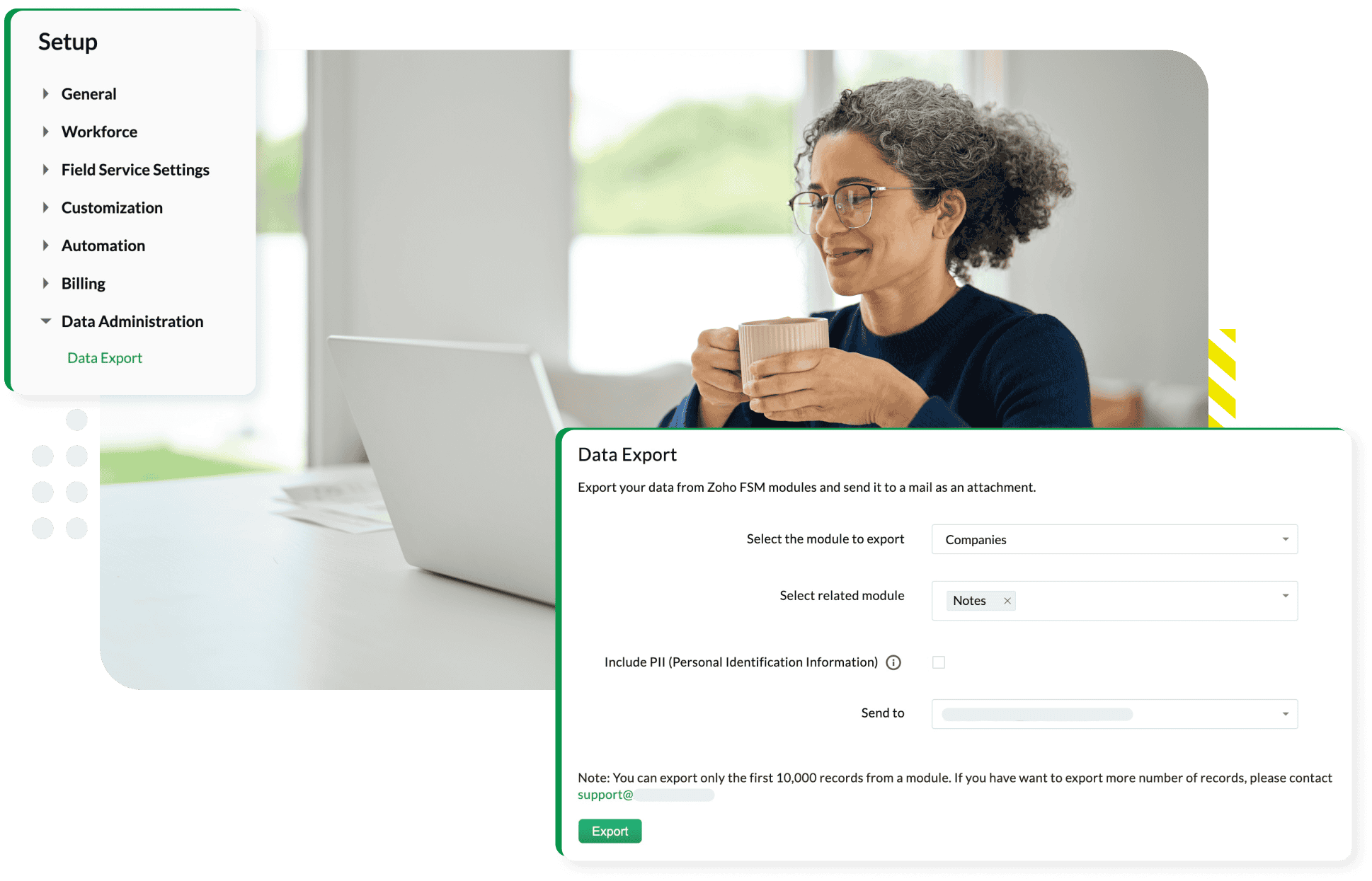
Secure data export
Control how data is exported by choosing whether to include PII fields in reports and data exports. This ensures that sensitive information is protected during external sharing and data extraction, maintaining privacy and security even outside of Zoho FSM.