Authenticate your - laptop
- desktop
- devices
at work
Authenticating laptops and desktops at work is a challenge, considering the different operating systems at play.
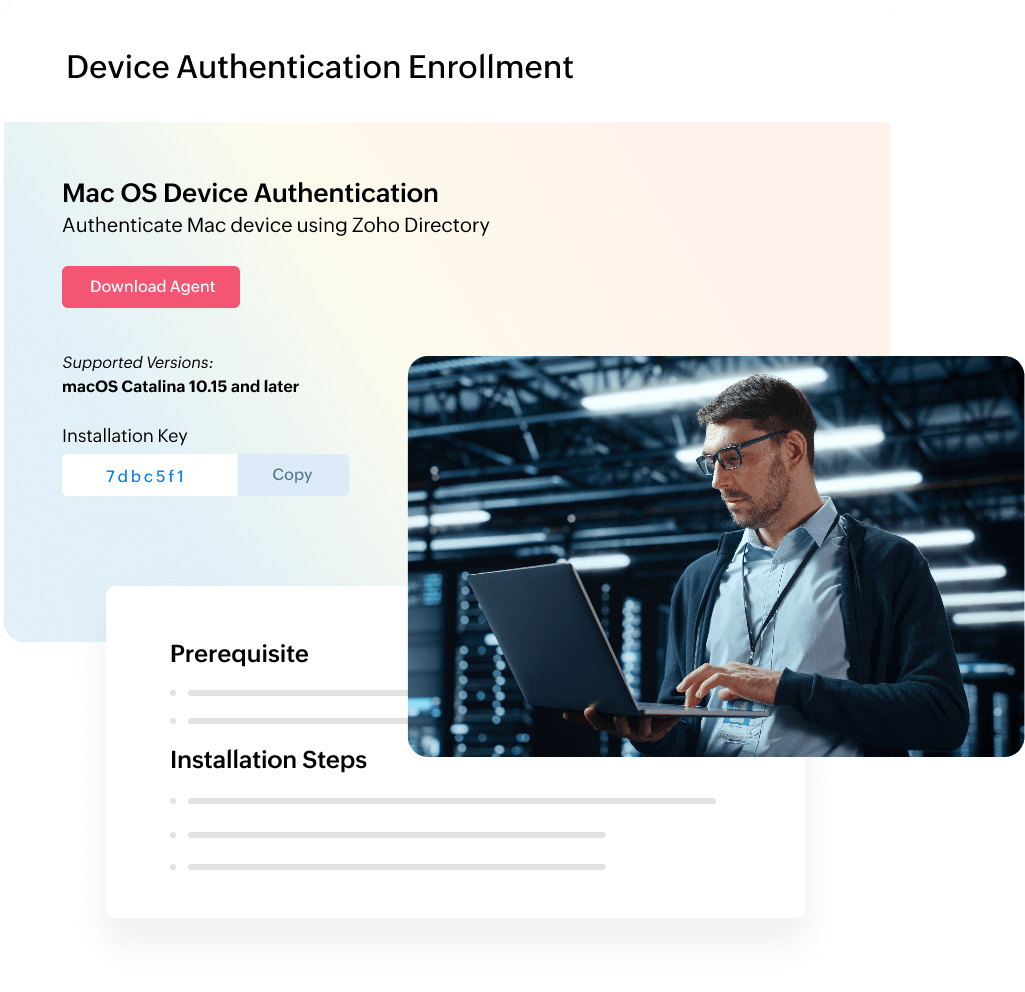
With Zoho Directory's Device Authentication, enroll all your Mac, Linux, and Windows devices to assign and unassign users, handle password resets, and change device permissions from a single space.
Get device authenticationWatch a Video
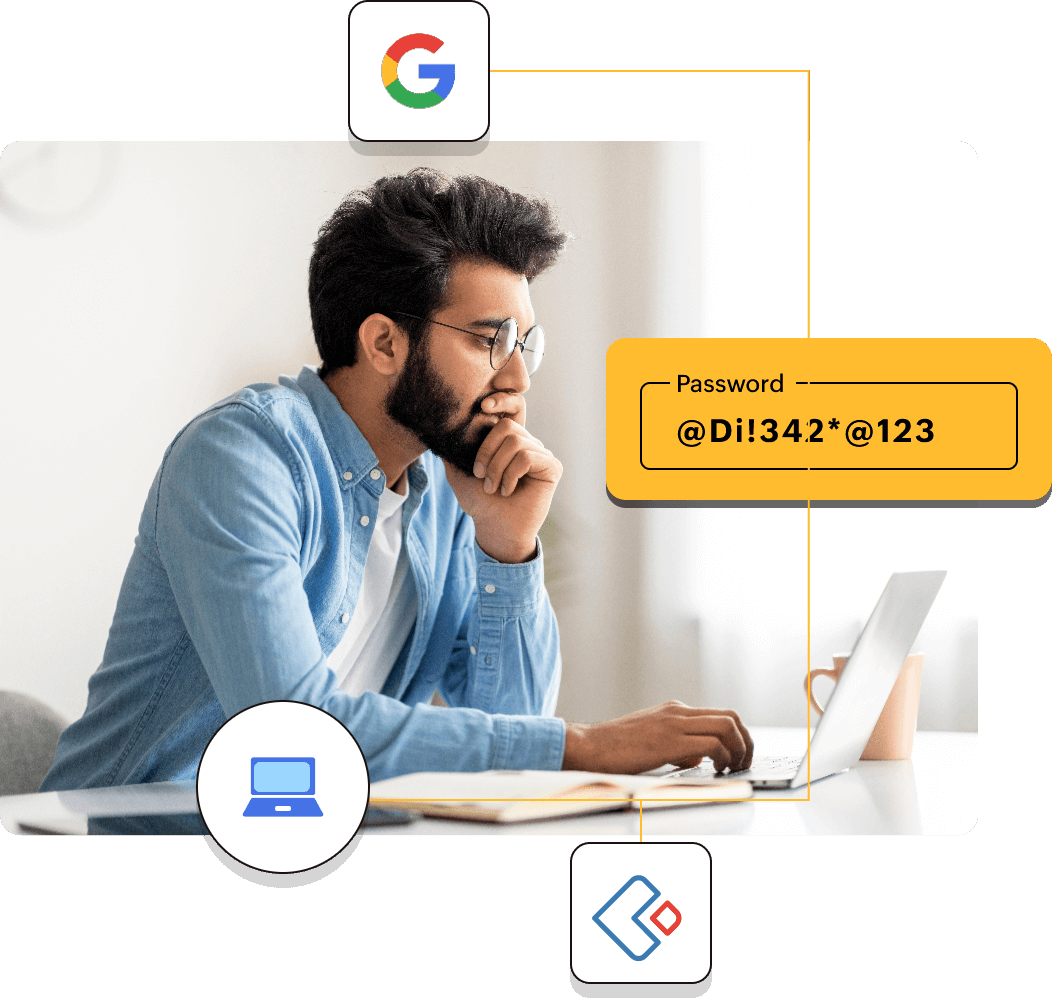
Improved employee login process
Give your employees an uncomplicated way to access their apps and devices with one set of credentials.
Save time for IT admins during device allocation
Authenticate, allocate, and manage all your Mac, Linux, and Windows devices directly from Zoho Directory (ZD).
Manage apps and devices from a single space
Use Zoho Directory as the central console to authenticate and manage all your apps, devices, and their interactions.
Reduce employee login time with one set of credentials
Employees often use separate login credentials to access their cloud apps and devices. With Zoho Directory's Device Authentication in place, employees get the advantage of accessing their apps and devices with one secure set of credentials. This reduces the overall friction and time spent.
Help IT admins save time when performing various device operations
Enrolling and allotting devices every time someone joins a company is a time-consuming process for IT admins. When it has to be done for several devices at once, this makes everything more hectic.
With Zoho Directory's Device Authentication, IT admins can easily enroll all Mac, Windows, and Linux devices. Crucial actions, such as handling device permissions when employees join, leave, or change roles, can be performed directly from Zoho Directory.
A central place to monitor all your apps, devices, and identities
Do you manage apps and devices with two different software solutions? Legacy software makes it difficult to centralize apps and devices of various operating systems. Zoho Directory (ZD) provides an easier way to manage all hardware and software with different operating systems—as well as employees and their interactions—from a single space. This gives you a clearer view of your resources and better control over organization-level security.