Evaluation Guide / Govern
Govern
Take control of your operations. Govern your data and processes with precision.

Users and Controls
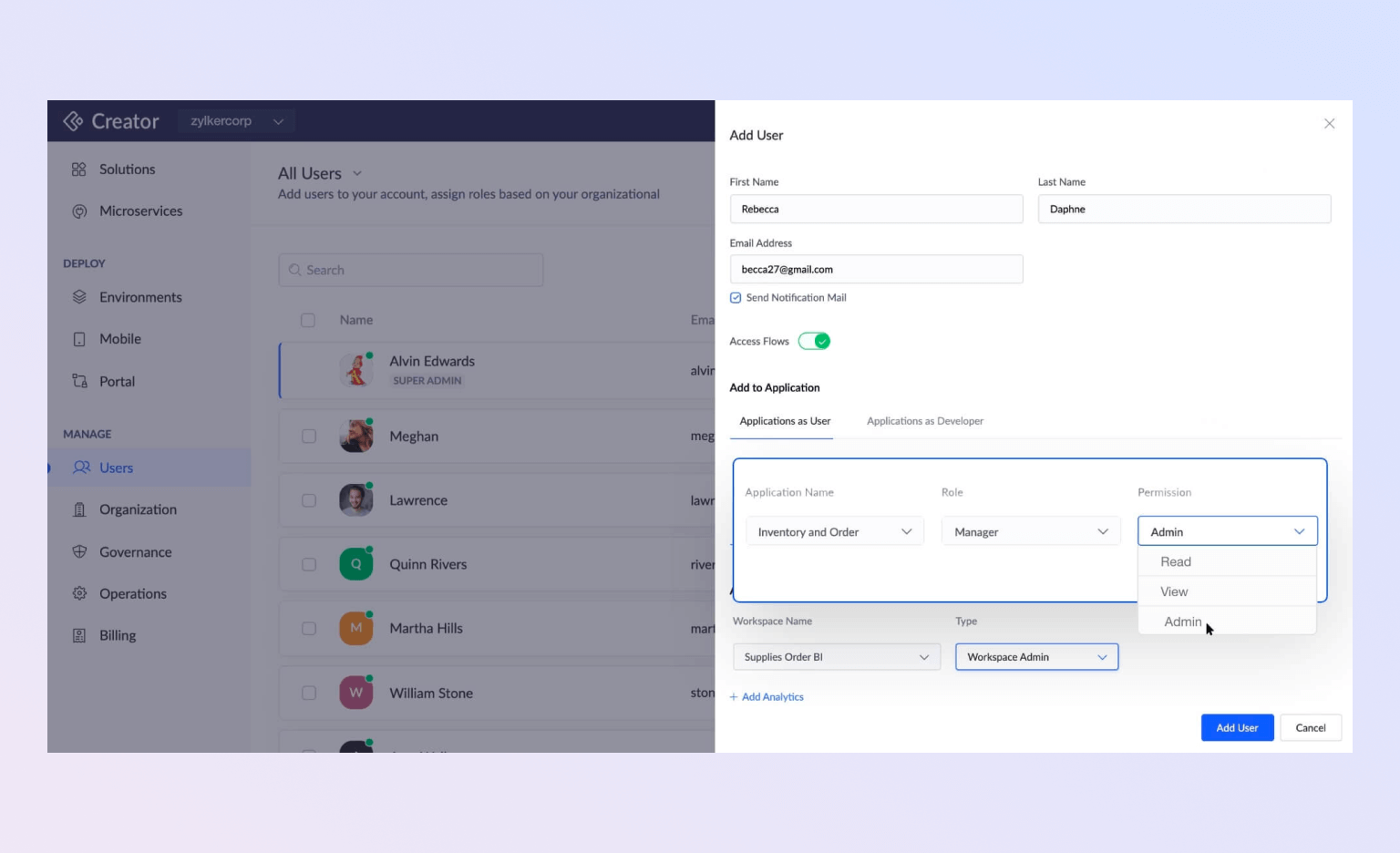
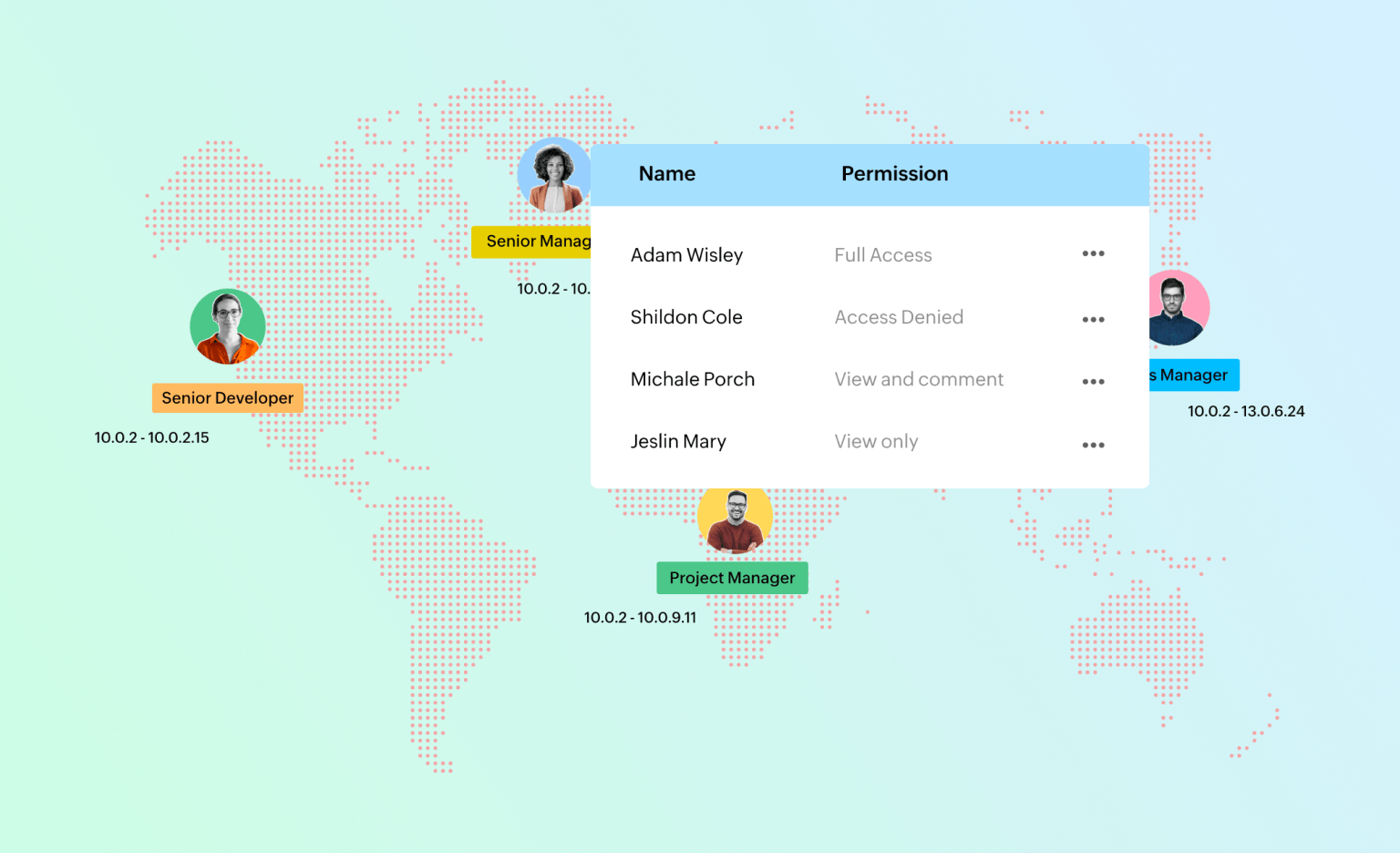
Role-Based Access Controls (RBAC)
In the realm of information security and system management, Role-Based Access Control (RBAC) is a significant feature that helps in managing user permissions based on their organizational roles. Zoho Creator's RBAC allows administrators to assign distinct roles to each user within the system. Each role comes with a specific set of permissions. This level of control helps maintain a more secure environment by ensuring that users only have access to the information necessary for their job functions. This approach also reduces the risk of data breaches by limiting the exposure of sensitive information to only those who require it for their roles.
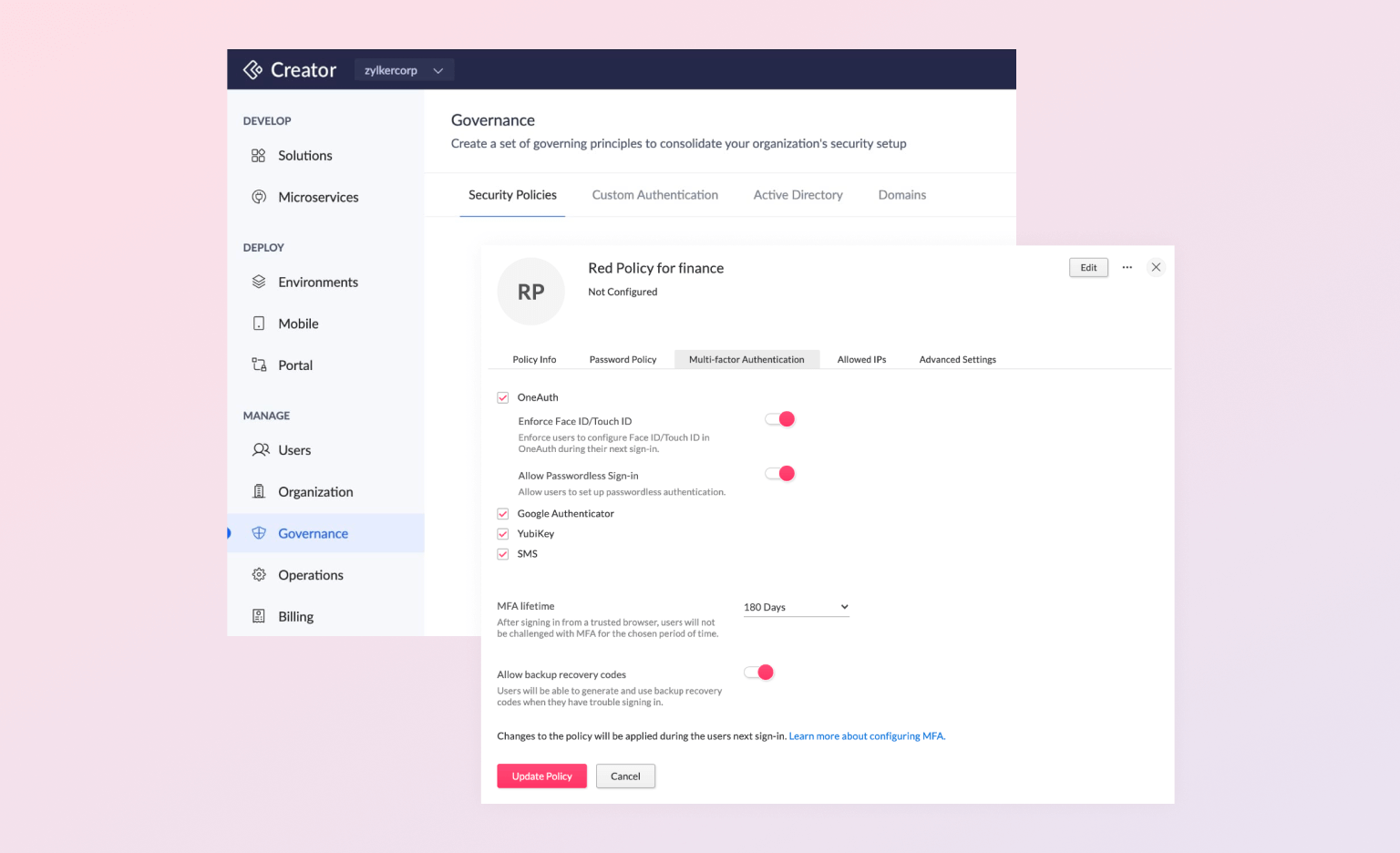
Security Policies
Security policies act as a backbone for maintaining the integrity of an organization's data and systems. In Zoho Creator, these policies go beyond the basic access controls. They define what actions users can perform and on what data, depending on their roles and responsibilities. A well-defined security policy helps in preventing unauthorized access and data breaches. By setting up stringent security policies, organizations can ensure a robust security posture, keeping their sensitive data secure at all times.
Multiple Apps, One Login
Zoho Creator enhances user experience and security with its 'Multiple Apps, One Login' feature. It eliminates the need for users to remember multiple sets of credentials for different applications. Instead, they can use one set of login details to access all necessary applications. This not only simplifies the process but also enhances security by reducing the likelihood of password mismanagement, which could potentially lead to unauthorized access.
IP Restrictions
Zoho Creator's IP restrictions feature provides an additional layer of security. With this feature, administrators can specify certain IP addresses or ranges from which users can access the application. This ensures that even if someone has valid user credentials, they cannot access the system from unapproved locations. This measure is particularly useful in preventing potential cyber threats originating from unknown or untrusted locations.
Application and Data
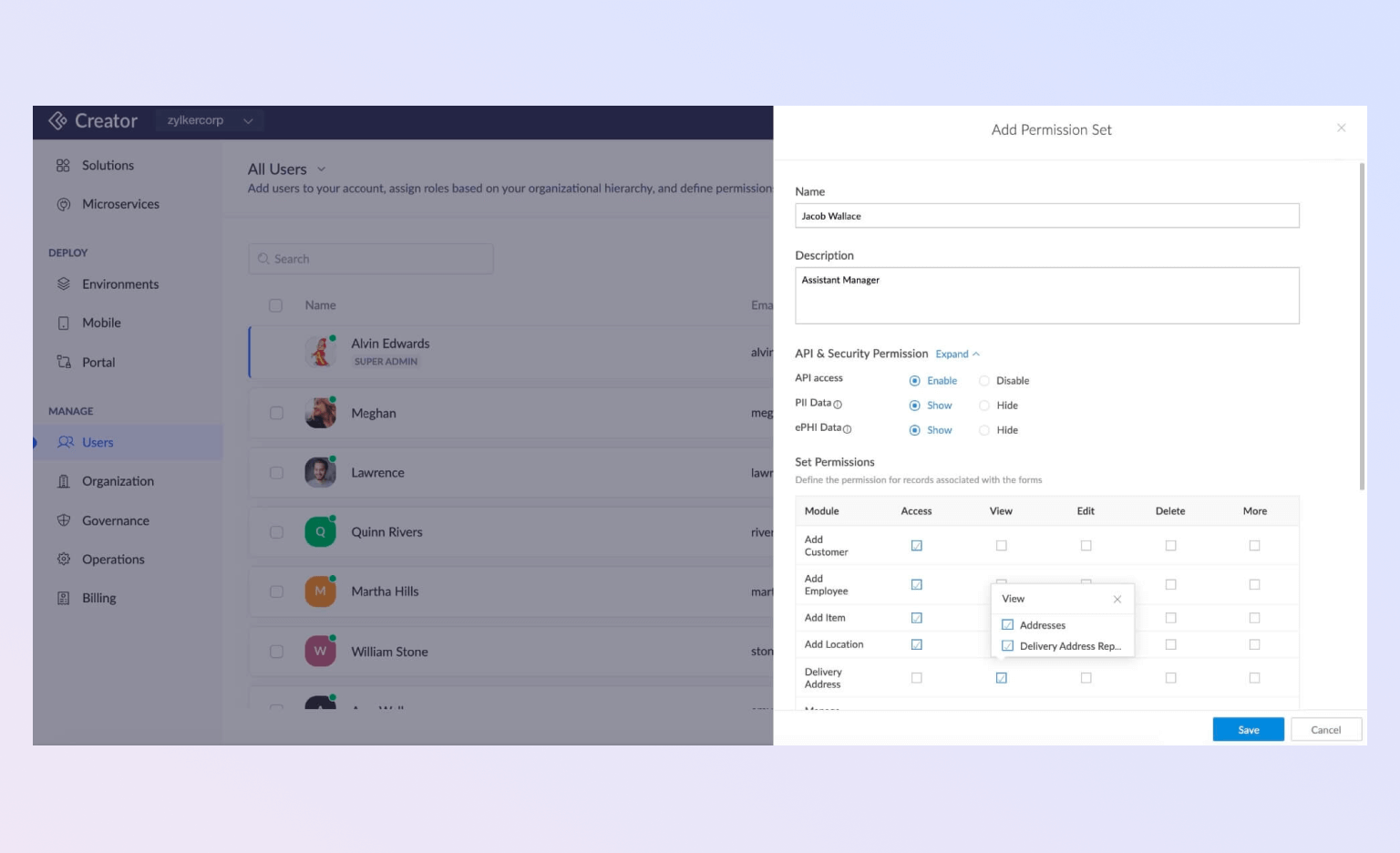
Audit Trails
Audit trails in Zoho Creator are secure, tamper-proof records that provide a chronological history of user activities within the application. Each entry in the audit trail records details such as who performed the action, what the action was, when it was performed, and what data was affected. This granular level of detail aids in troubleshooting, detecting anomalies, and supporting compliance efforts. Audit trails also promote accountability among users, as their actions are logged and can be reviewed if needed.
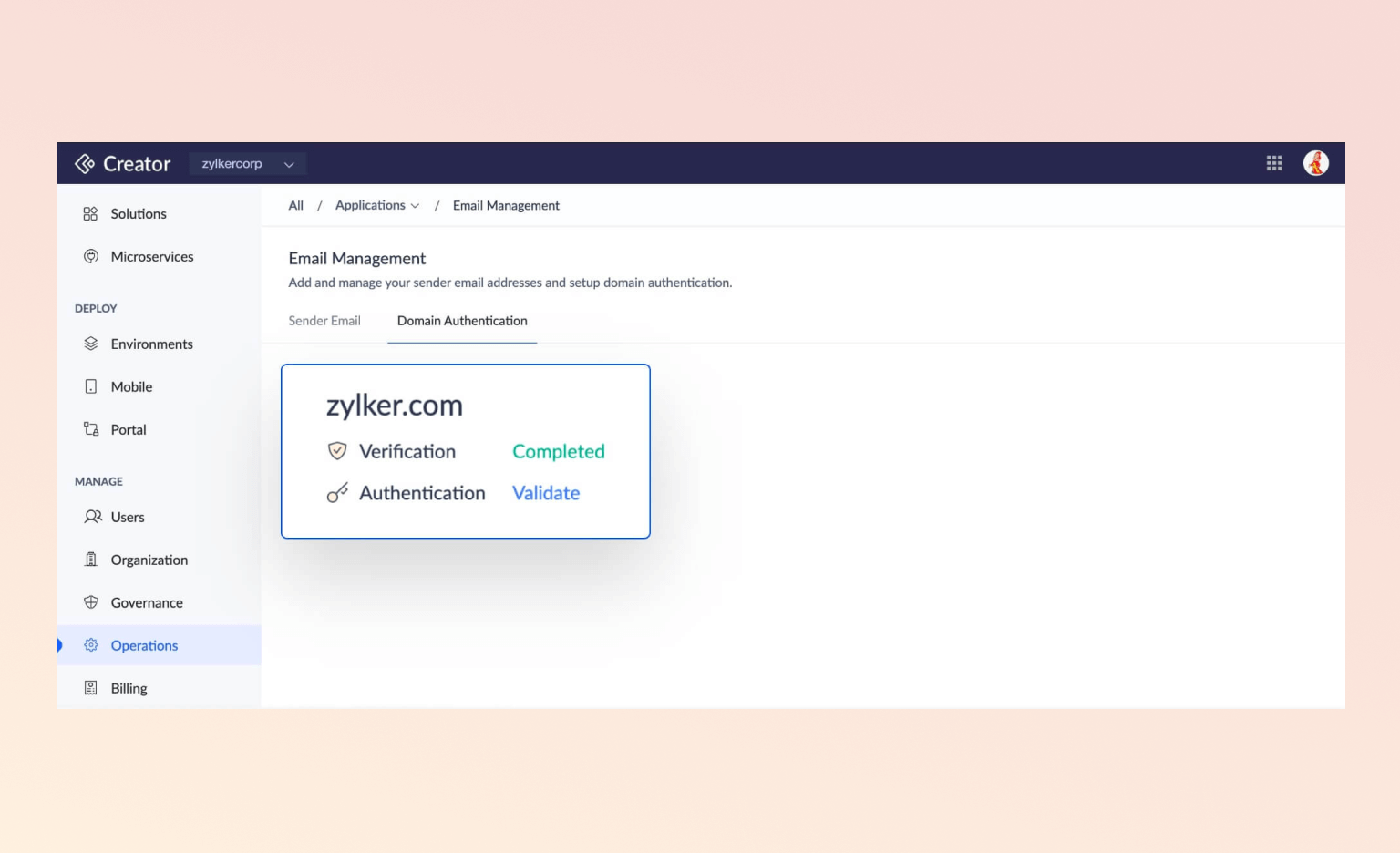
Domain Authentication
Zoho Creator employs domain authentication to ensure that only legitimate domains can access the application. This feature is crucial in preventing 'domain spoofing,' where an attacker pretends to be a trusted entity to gain unauthorized access. By authenticating the domain, Zoho Creator adds an extra layer of security, ensuring that only authorized domains can interact with the application, thereby reducing the risk of phishing and other types of cyberattacks.
Secure Email Transactions
Email communication is a common vector for cyber threats. Zoho Creator mitigates this risk by securing all email transactions within the platform. Emails sent through Zoho Creator are secured, ensuring that the information they contain is confidential and accessible only to the intended recipients. This protects sensitive information from being intercepted or misused, thereby enhancing overall communication security.
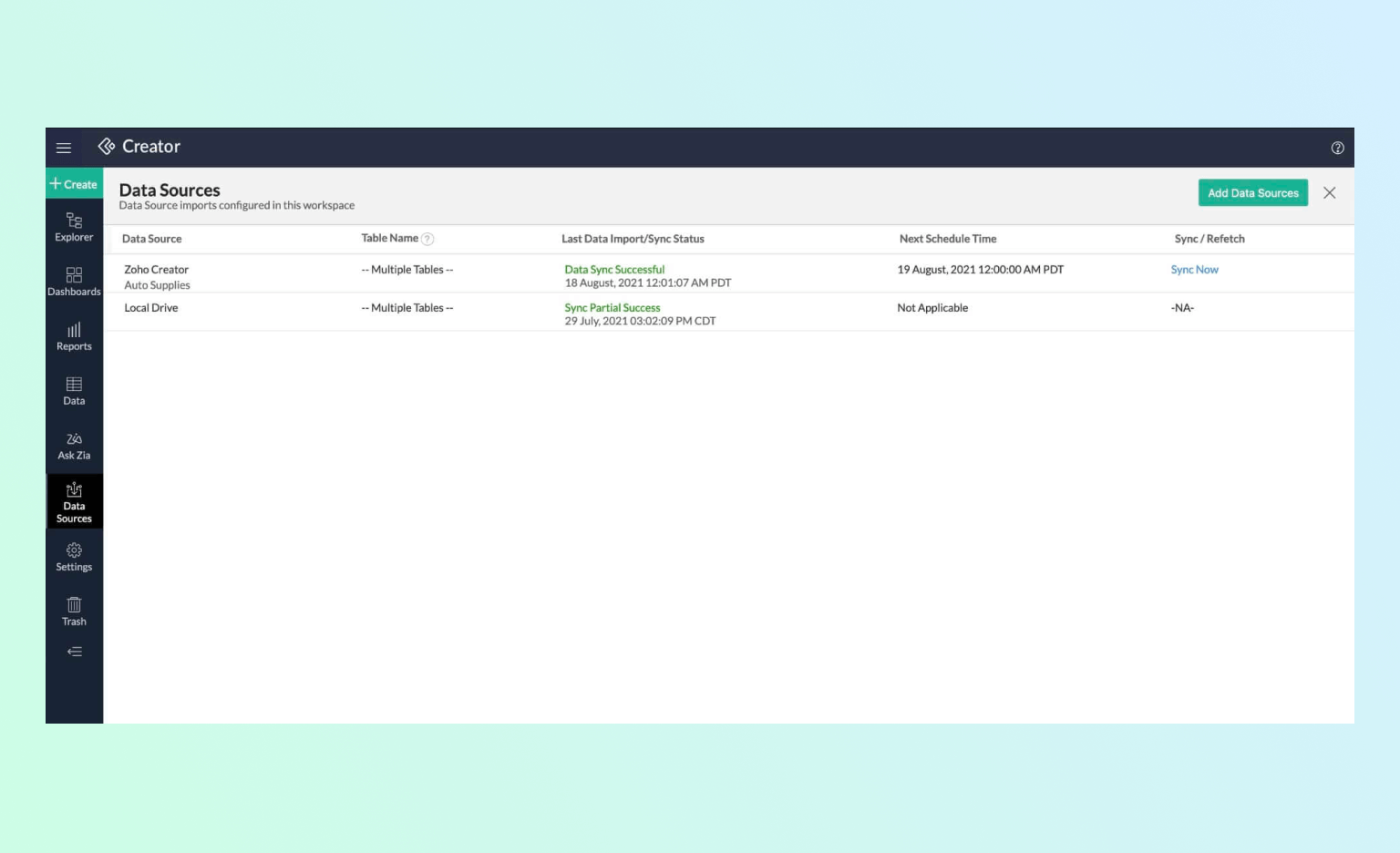
Data Bridge
Zoho Creator's data bridge feature is a powerful tool for data migration. It facilitates the seamless transfer of data between different environments, ensuring data integrity and consistency. Whether it's system upgrades or migrations, the data bridge feature ensures that data is accurately transferred without any loss or corruption. This not only maintains data integrity but also reduces downtime during migrations, ensuring business continuity.