Cloud security and how to recognise a trustworthy cloud service provider
- Last Updated : June 12, 2023
- 1.7K Views
- 8 Min Read

COVID-19 has undoubtedly been one of the biggest challenges of our lifetime, but our region has really pulled together to keep the economy afloat. In addition to efficient contact tracing and hotel quarantine systems, businesses were quick to adopt new technology to keep their operations running strong. CRN and Garner report that public cloud services will cross a whopping $5.7 billion in sales this year. For comparison, last year's were roughly $4.8 billion. It goes to show that we are determined to thrive in the post-pandemic world, even if that means adopting and experimenting with unfamiliar technology.
But with everyone making this transition so quickly, some people are rightfully asking—just how safe is the cloud?
Cloud security challenges
When navigated correctly, the cloud is actually very secure. It keeps your data away from prying eyes and hands, ensuring that only authorised personnel have access. But just because your data is on the cloud doesn't mean it's automatically safe. Cloud service providers face unique data security challenges that you must be aware of.
Security: In a manner of speaking, the cloud is everywhere. The absence of a fixed perimeter opens the cloud up to more cyber threats, and you'll need an extra level of protection to combat this. What's more, cloud services are easy to sign up for, which means that more of your employees could be using software programs that your IT team aren't aware of. This is called shadow IT. Although shadow IT seems harmless, your employees may be unintentionally giving data access to unvetted software systems.
Data protection: This refers to the challenges of storing and processing data itself. A cloud vendor has to ensure that:
A client's data is always available to them
That data isn't leaked to unauthorised people
The data is stored in the right geographical locations to comply with local laws
Clients have the flexibility to migrate their data to other vendors
They get rid of old data responsibly
Trust: Possibly the biggest challenge for cloud vendors is gaining trust. Naturally, they must earn their customers' confidence in their products and services, but they must also develop trustworthy relationships with partners and third-party app vendors. The key to building this trust is transparency. By keeping everyone in the loop on who handles what areas of the business, cloud providers can improve accountability, identify threats faster, and easily comply with the legal regulations in different regions.
It's important to familiarise your employees with these challenges and the strategies to overcome them. This gives your team more context when researching providers to see if they handle data security and privacy responsibly. Not to mention that the full burden of data protection doesn't only fall on your software provider. In many ways, you become a team against data security threats.
Below, we'll break down some of the ways to overcome cloud security challenges to help your employees stay proactive and evaluate cloud service providers more efficiently as digitisation ramps up across the world.
Strategies to overcome cloud challenges
1. Adopt a zero-trust model
One of the key principles of cloud security is to trust no one and nothing. This doesn't necessarily mean that you shouldn't trust your employees to handle data responsibly, but it does mean that providing training and education to your workers about data security is helpful. It also means that no security measure should be trusted as your sole line of defence. Whether you store your data on a public or private cloud, you still have to take multiple security precautions.
The best way to do this is to require two-factor authentication (2FA) or multi-factor authentication (MFA) every time someone wants access to specific data. A single password may no longer be sufficient against today's cyber criminals, but having two or three authentication modes put together drastically increases your data security.
When implementing a data authentication method, consider its specificity and brevity. Secret questions, facial recognition, and fingerprint IDs are specific to a person. One-time passwords and activation links expire after a short time. The more unique and time-bound your authentication modes, the stronger your security system.
The back end security also matters. Your employees should only have access to the information they need when they need it—and only within the right context. For example, you don't want them accessing customer payment information through a public wifi connection. Your authentication process should be able to prevent access in these situations.
Unfortunately, these kinds of granular security measures can bog down your system if they aren't implemented efficiently. Cloud providers have the responsibility to give you authentication systems that ensure security while always remaining user-friendly. Otherwise, simple tasks like logging into your work email can become exceptionally tedious.
Takeaway: Make sure that your cloud service provider offers 2FA and MFA options, and try them out to see how user-friendly they are for you and your employees.
2. Build security into every layer
Every piece of cloud software has multiple layers, and each of these layers needs to be secured to maintain data integrity. Here's a quick run down of the layers and what they're made of.
The infrastructure layer includes physical servers, firewalls, and other machines. If you use a cloud IaaS (Infrastructure as a Service) provider, they'll handle these systems for you, including setting up and maintaining them.
Next is the platform layer, which includes databases, cache servers, and microservices. PaaS (Platform as a Service) providers manage these systems.
The application layer is made up of the business logic, workflows, and hosting. SaaS (Software as a Service) vendors take care of these systems.
Finally comes the end user layer or the data layer, which includes web browsers and mobile apps. This layer is where you have the most control over how your data is secured.
Your data is only truly secure if all four of these layers are secured.
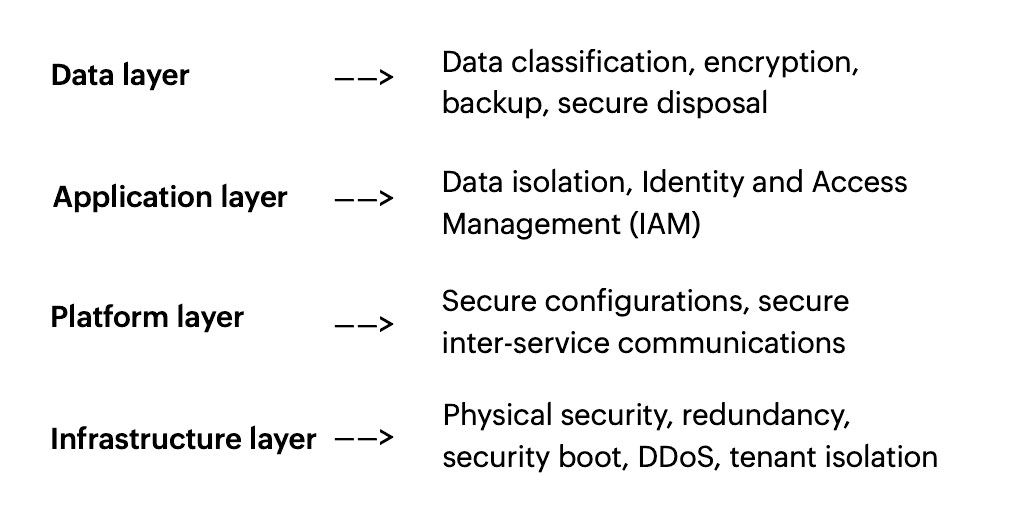
This means establishing:
Tenant isolation and security protocols against DDoS attacks in your infrastructure layer
Security configurations and interservice communication in your platform layer
Data isolation and controlled access in the application layer
Data encryption and backups in the data layer
That is a lot of security. Luckily, if you choose a SaaS vendor, they'll secure the application layer and all the layers beneath it, giving you a complete package that you can implement in your business. As a customer, you have to ensure that the data layer is secure so that the other layers can remain safe, but there are features and tools that your cloud service provider should give you to tighten your data layer. Some of these include data classification, encryption, storage, deletion, and ownership.
Takeaway: Familiarise yourself with the data security options offered by your cloud service provider, and understand which software layers you are responsible for. Take a look at the Australian Government's cloud computing and privacy factsheet for more information about your role in choosing a software provider.
3. Implement security feedback loops
When you entrust a cloud service provider with storing your business data, you're also trusting them with your customers' information. You have to ensure that nothing goes amiss with your data systems, so it's up to you to understand your software solution well enough to spot abnormalities. If users are trying to force their way into your system, or if you're getting a surge or traffic from bad domains, then you will have to follow up on these activities to ensure your customers' data is safe.
Any cloud customer will face these issues, so your vendor should have resources that can help you identify threat signals as well. Your cloud service provider should offer features such as instant email and SMS alerts, extensive audit trails, and activity, access, and network logs. When you notice something is amiss, you can check your logs to see what's happened. In most cases, your cloud provider can also look at their logs to identify threats and potential attacks.
If an event occurs, like a network attack or account breach, your provider will quickly act based on these logs. They might revoke access to specific problematic accounts and they'll let you know of any security breaches to their systems. Cloud vendors are bound by breach notification obligations. Depending on the seriousness of the breach, they should inform you within a stipulated time so that you can inform your customers.
Takeaway: Learn to identify abnormal behaviour across your software usage. If you see anything odd, check your logs to rectify it, and ensure your cloud provider is prepared to help you with events or incidents.
4. Communicate shared responsibility
When it comes to security in the cloud, you are just as responsible as your provider. Based on your cloud adoption model, you'll have more or fewer elements to manage.
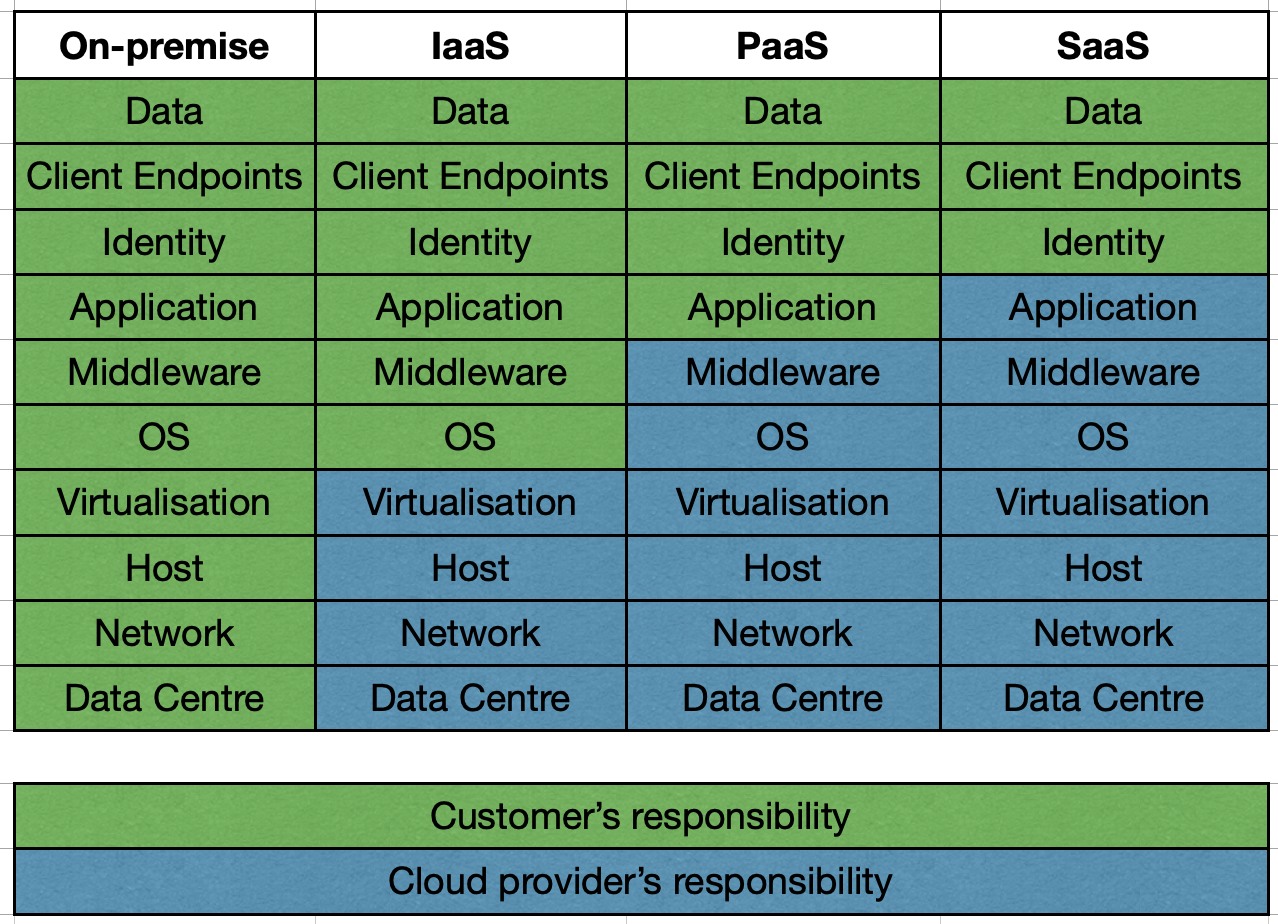
If you use a cloud IaaS provider, then the vendor will handle all infrastructure-based security, and you will have to account for the operating system, application, and data security.
With a PaaS provider, you only have to take care of building and securing your application and its data.
With a SaaS provider, your responsibilities are further reduced. You only have to take care of verifying user identities and securing the data itself.
As a cloud service customer, it's important to play your part in maintaining data security. For example, in early 2020 when Zoom was becoming everyone's first choice for virtual meetings, many users had strangers joining their personal sessions. This is a potential security violation, and Zoom addressed this by introducing a waiting room and mandatory passwords. However, in such situations, the users should also be careful of where and how they share meeting information. Airdropping links using a public wifi network might not be a good idea.
Takeaway: Accept your role in protecting your data on the cloud. Be diligent about your usage, and always use the security functions embedded in your cloud solutions.
Concluding remarks
Cloud security has nothing to do with whether you're a small business or a large enterprise. Regardless of your size, industry, and level of cloud adoption, your data may be at risk if you don't follow certain measures. The cloud can be very secure, but blindly trusting it is setting yourself up for failure. To protect your data and your customers' data, you have to cultivate a culture of cyber security and privacy within your business.
This includes:
Nurturing security and privacy champions in every team
Educating your employees about the value of good security measures
Prioritising risk management and reduction
Designing processes with security and privacy as the foundation
Establishing an agile and collaborative work environment
Being transparent with your customers
Above all, remember that cloud security is a long-term goal. Do your research, ask questions, and choose your cloud service provider wisely.


