Over 180,000 organizations across 190 countries trust ManageEngine to manage their IT
- Volkswagen
- Symantec
- CHS
- Lockheed Martin
- Allianz
- Unisys
- IBM
- NSE
- Siemens
- Infosys
- Dell
- EY
- Lanb
- nissan
- nyu
- samsung electronis
- hcl
- Toshiba
- ComCast
- Northrop Grumman
- NetApp
- Deloitte
- TCS
- xerox
- nielson
- ebay
- Michigan State
- Toyota
- Panasonic
- Mitsubishi
- Bank of America
- Yamaha
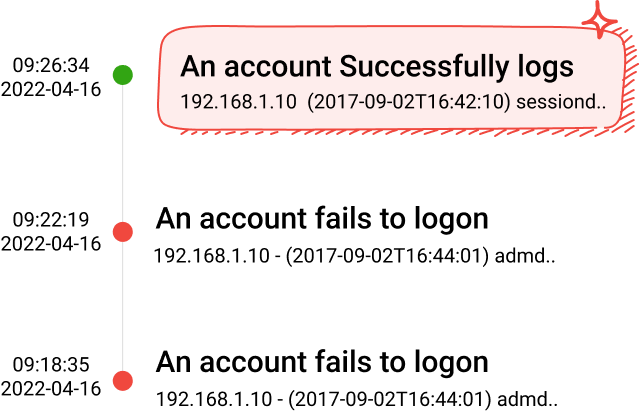
Access and manage cybersecurity incidents from anywhere
Alerts
Near real-time SMS and email alerts
- A logon from a malicious IP has been detected.
Event correlation
Correlate events across your network to identify indicators of compromise.
- User account threat
Excessive VPN Logon Failed due to incorrect..
- Brute Force attacks
A series of multiple logon failure
- User account threat
Cloud application monitoring
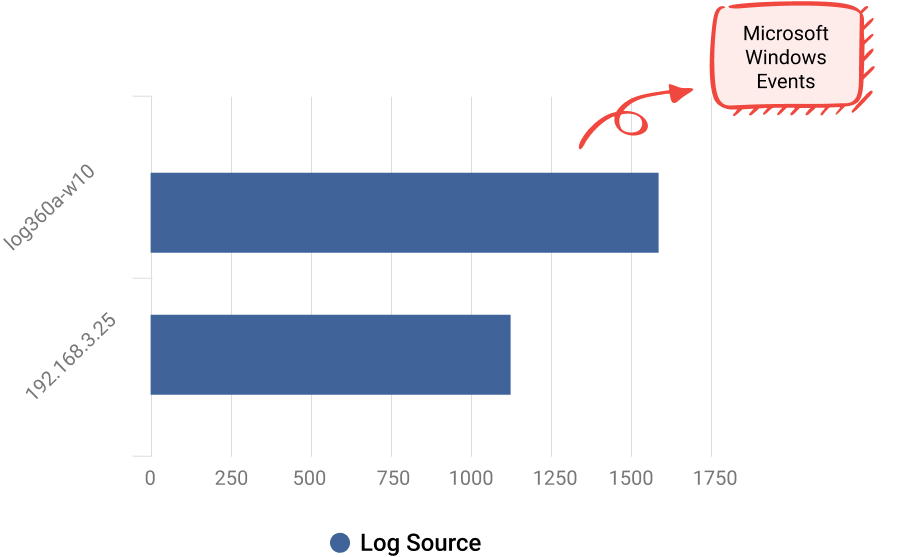
Comprehensive visibility on cloud application usage

The Cloud advantage
The cloud version helps you leverage Log360's comprehensive security operations capabilities as a service. Now you can collect and manage logs, generate audit-ready reports, correlate events, detect threats, and ensure compliance to the latest security regulations in the cloud.
Why Log360 Cloud is perfect for your business

Instant set up
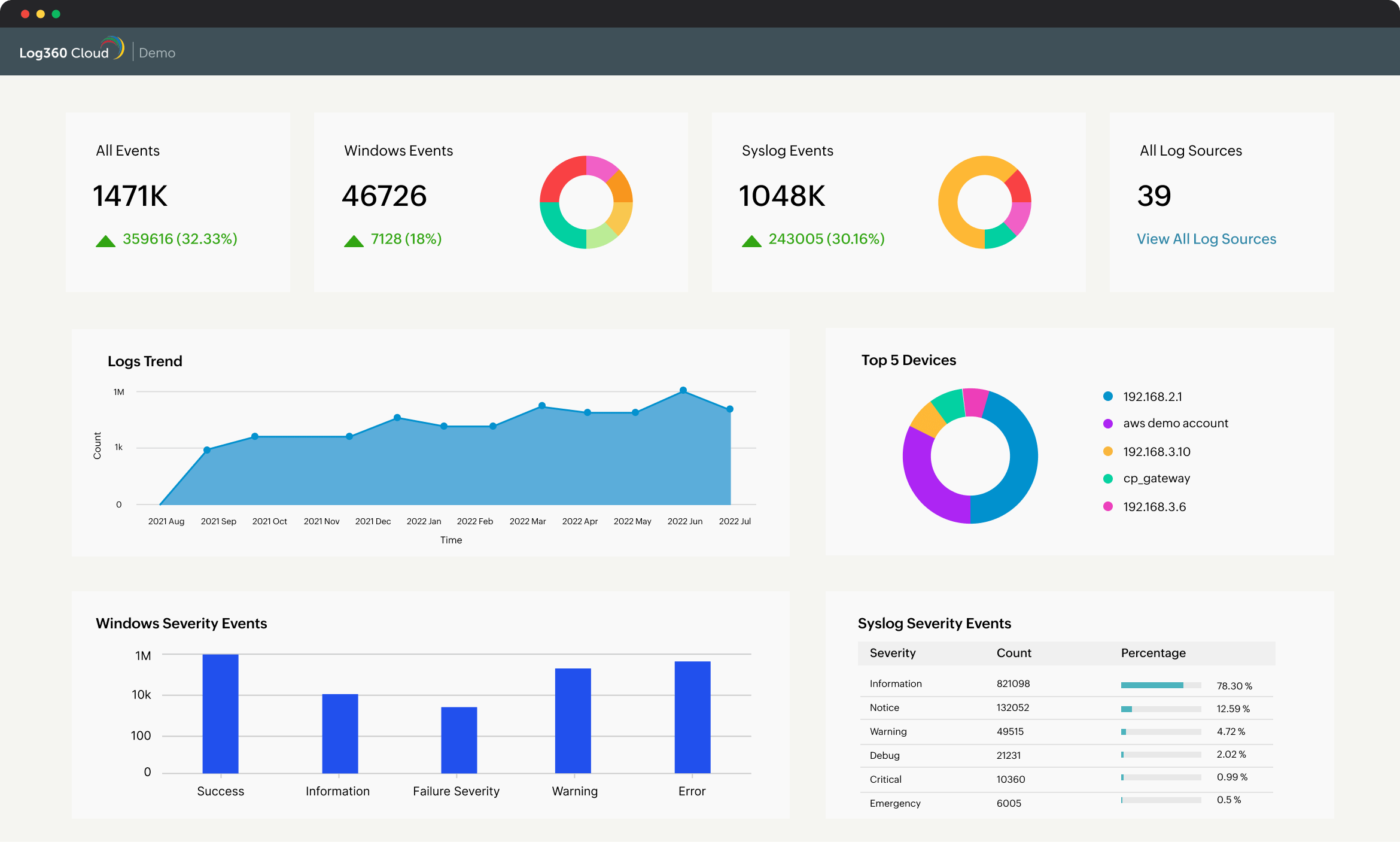
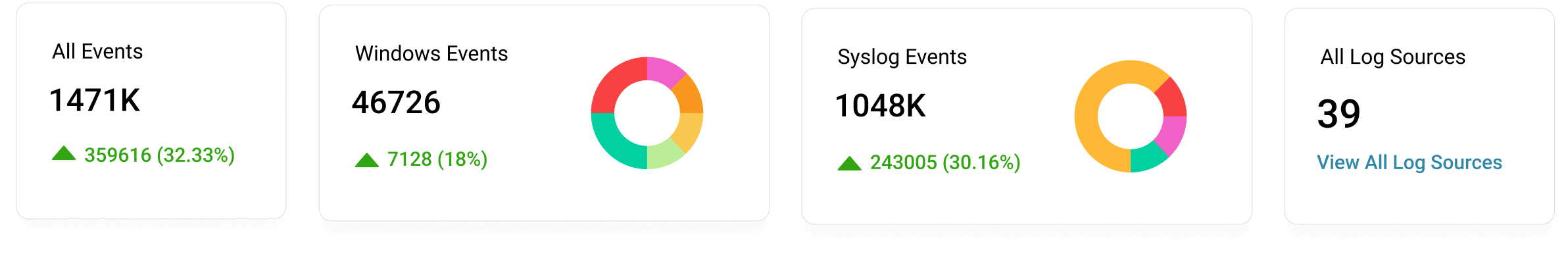
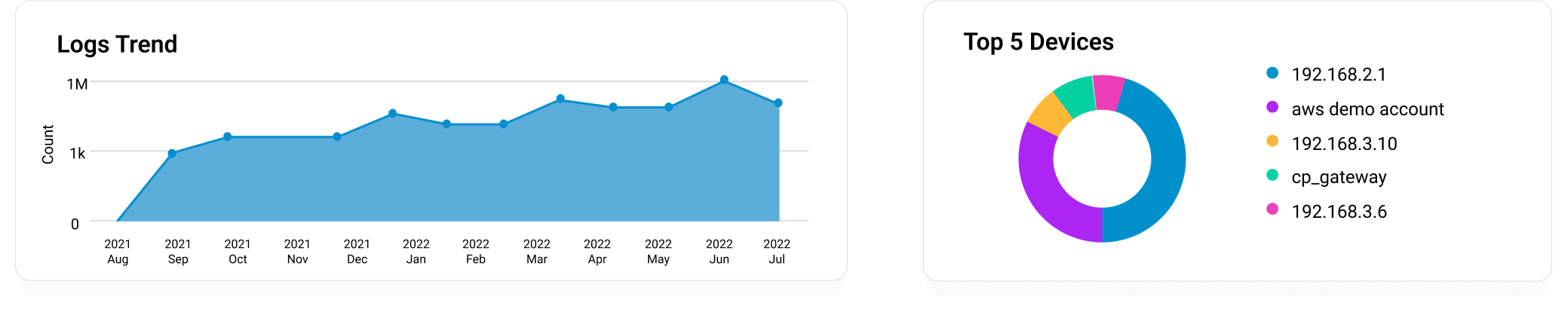
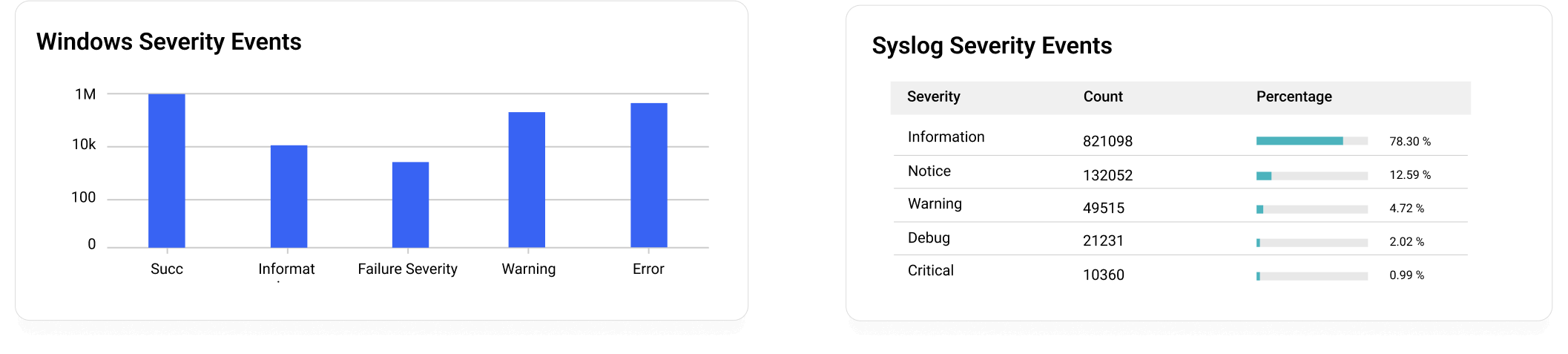
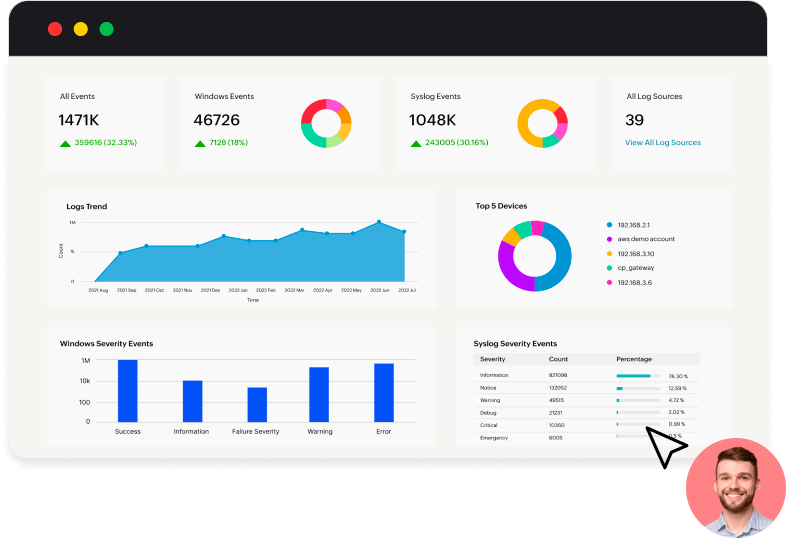
Just install the log collection agent, configure your devices, and start analyzing and visualizing logs within minutes in the form of graphs, charts, and other visual representations.

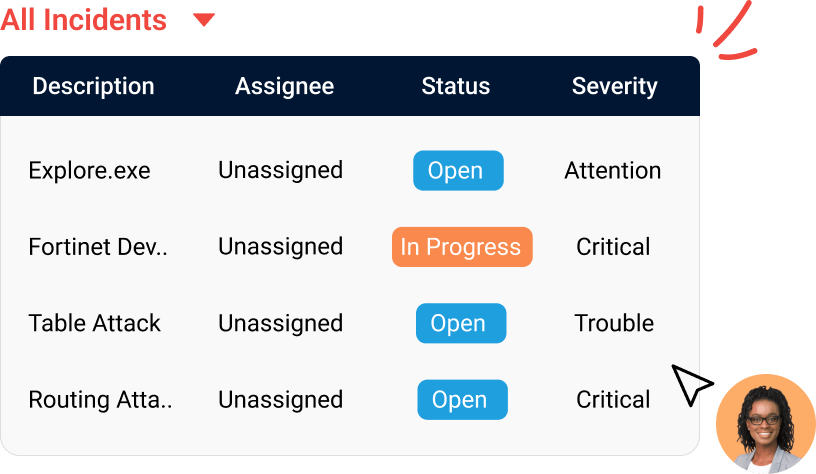
Effective incident management
The time between the occurrence of a security incident and the response to it can make or break businesses. With Log360 Cloud, view all the incidents in your network and track crucial information such as severity, status, and assignee.

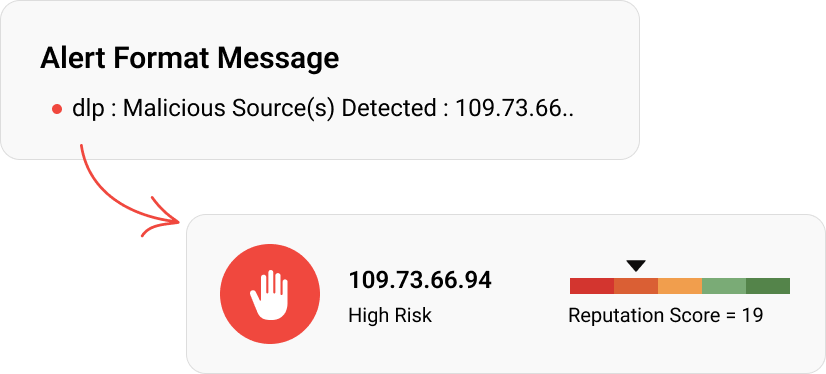
Threat detection
Retrieve the latest information from multiple reliable threat feeds and monitor your network for signs of possible threats. Conduct forensic investigations, ensure accountability in incident resolution, and more using built-in threat detection capabilities.

Built-in analytics and reporting
Generate reports that show who did what, when, and from where. Visualize metrics in the form of graphs and charts to make informed decisions. With threshold-based alerts for incidents, shield yourself from alert fatigue. Know more.

Detect indicators of compromise
Correlate seemingly unrelated network events to identify indicators of an attack. With quick, accurate alerts, you can take a proactive stance and prevent damage to your network data and resources.

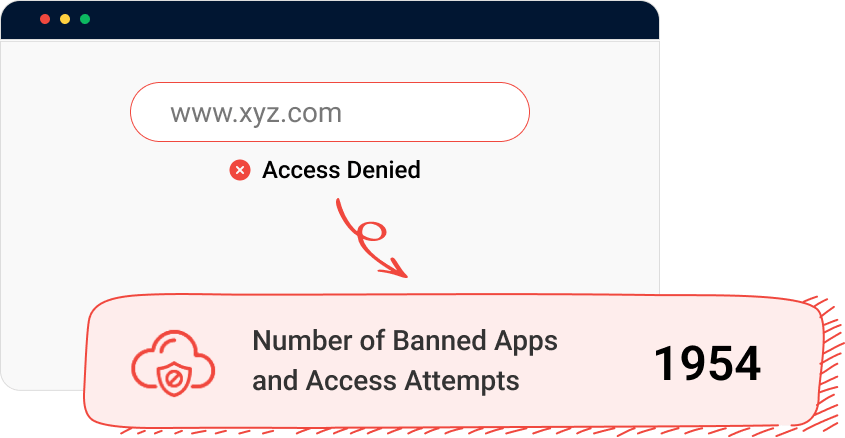
Cloud security
Enforce protection of all web applications in your network. Gain visibility into your cloud platforms with a cloud access security broker. Discover shadow applications being used in your network and block user access to such applications using Shadow App Discovery.
Manage your security operations on the cloud
Sign up for free